Inside 1,602 pentests: Common vulnerabilities, findings and fixes
Each year, Cobalt releases its State of Pentesting report, which extracts trends and statistics about the state of security from penetration testing engagements on its platform. This year’s report is based on an analysis of 1,602 pentests performed in 2021 and survey results from 601 companies that are not all Cobalt customers. Of these 1,602 pentests, nearly three-quarters of companies sought Cobalt’s services for pentests of their web applications or web APIs. As a result, the vulnerabilities and remediation recommendations outlined in Cobalt’s report skewed heavily towards web apps and APIs.

FREE role-guided training plans
The vulnerabilities
Analysis of 1,602 pentest engagements provides Cobalt with deep visibility into the vulnerabilities and security issues its customers are struggling with. Based on its analysis, Cobalt was able to identify the most common vulnerabilities and pentest findings in 2021 and break down results by asset and industry.
Top five most common vulnerabilities
Cobalt has been publishing a list of the five most common vulnerabilities in its State of Pentesting Reports since 2018. The 2021 report’s list includes:
- Server Security Misconfigurations (28.1%)
- Cross-Site Scripting (15.5%)
- Broken Access Control (14.7%)
- Sensitive Data Exposure (8.4%)
- Authentication and Sessions (8%)
For those familiar with the report, this list may look familiar. Each year since 2018, the top five vulnerabilities have been the same with the only differences being the order and the frequencies. However, ‘Server Security Misconfigurations’ consistently takes the top spot by a large margin (12.6% in this case).
This trend is not unique to Cobalt’s report. Developers have been struggling with the same security issues for years. For example, the OWASP Top 10 List has been largely unchanged for years, with most updates simply merging existing categories to make room for other common vulnerabilities.
Top five findings for 2020
In its report, Cobalt makes a distinction between vulnerabilities and findings. In general, vulnerabilities are classes of security issues, while findings are specific instances that might be identified during a pentesting engagement. For example, cross-site scripting (XSS) is a vulnerability, while Stored and Reflected XSS are findings.
In addition to its top five vulnerability classes, Cobalt also reported on the top five most common specific findings. These include:
- Broken Access Control: Insecure Direct Object References (IDOR): 9.4% of total findings
- Cross-Site Scripting: Stored: 8.7%
- Components with Known Vulnerabilities: Outdated Software: 4.1%
- Broken Access Control: Username/Email Enumeration: 3.8%
- Cross-Site Scripting: Reflected: 3.7%
In its report, Cobalt claims that both Stored and Reflected XSS make this top five list. This is despite the fact that this vulnerability has been known for a decade and has been declared “dead” in some corners.
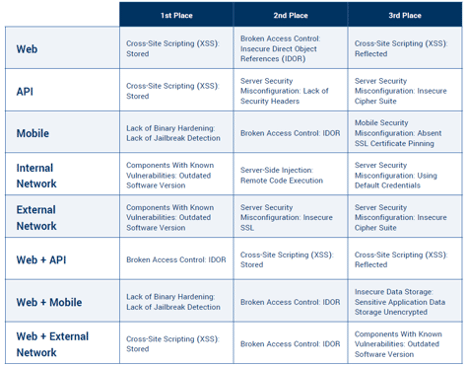
Asset-specific findings
While Cobalt’s pentests were primarily focused on web apps and APIs, it also has data regarding mobile devices, internal and external networks, and the combinations of web plus APIs, mobile and external networks. The table below identifies the three most common findings for each of these categories.
Cobalt defines 286 possible findings, but only twelve appear in these twenty-four slots. The mistakes that are being made are often repeated across multiple different asset classes.
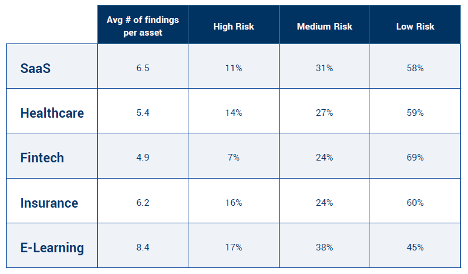
Industry-specific findings
Cobalt also broke down its report findings by industry. This led to one of the most striking results from the report: “Industries which are more likely to handle financial, health or other sensitive data such as Healthcare, Insurance and Fintech, are still susceptible to IDOR vulnerabilities. This well-known flaw could allow an attacker to bypass authorization controls and access Personally Identifiable Information (PII) or Protected Health Information (PHI).”
Many of these industries also have significant findings per asset, as shown in the table below. Cobalt calls out that e-learning, an industry that experienced rapid growth in 2020 due to the pandemic, is struggling the most.
What’s going wrong, and how do we fix it?
Developers are struggling with well-known vulnerabilities. However, this is only part of the problem. Developers are also making the same mistakes over and over.
Based on the results of its analysis, Cobalt surveyed 601 companies to identify root causes. On average, their respondents claimed to have identified and fixed 54 vulnerabilities in the last year but, 60% saw the same vulnerability show up again. Based on these results, Cobalt identified four recommendations for remediating the issue:
- Defense in depth: Many companies implement secure development practices, but some vulnerabilities still slip through. Using multiple lines of defense, including pentesting, provides the highest probability of identifying issues before they become a problem.
- Make pentesting accessible: Many organizations claimed that pentesting was unusable due to cost and setup time. Fixing this is essential to improving security.
- Fix all of the problems: Vulnerability triage commonly means that critical vulnerabilities are fixed quickly, while lower-risk ones are addressed more slowly if at all. As a result, companies.
- Automate and integrate: Reliance on manual processes with disparate tools slows vulnerability management. A sustainable approach requires better tools.

What should you learn next?
Check out the full state of pentesting
Here, we only scratched the surface of the findings of the report. Check out the complete report here.