Introduction to the Nikto web application vulnerability scanner
The increase in web applications on the internet today raises a security concern because in some cases, security is haphazardly considered during development. As a result, we often end up having vulnerable web apps that attackers might exploit, jeopardizing user information. To address this, multiple vulnerability scanners targeting web applications exist. In this article, we will take a look at Nikto, a web application scanner that penetration testers, malicious hackers, and web application developers use to identify security issues on web apps.
Nikto overview
Nikto was originally written and maintained by Sullo, CIRT, Inc. It is currently maintained by David Lodge, though other contributors have been involved in the project as well.

FREE role-guided training plans
It is built to run on any platform which has a Perl environment and has been incorporated within the Kali Linux Penetration Testing distribution. It is an open source tool, supporting SSL, proxies, host authentication, IDS evasion, and more. It can be updated automatically from the command-line, and supports the optional submission of updated version data back to the maintainers.
Nikto allows pentesters, hackers and developers to examine a web server to find potential problems and security vulnerabilities, including:
- Server and software misconfigurations
- Default files and programs
- Insecure files and programs
- Outdated servers and programs
Nikto features
During web app scanning, different scenarios might be encountered. Nikto supports a wide variety of options that can be implemented during such situations. The following is an overview of the included options in Nikto:
-Cgidirs: This option is used to scan specified CGI directories. Users can filter "none" or "all" to scan all CGI directories or none. A literal value for a CGI directory such as "/cgi-test/" may also be specified (note that a trailing slash is required). If this is option is not specified, all CGI directories listed in config.txt will be tested.
-config: This option allows the pentester, hacker, or developer to specify an alternative config file to use instead of the config.txt located in the install directory.
-Display: One can control the output that Nikto shows. Reference numbers are used for specification. Multiple numbers may be used as well. The allowed reference numbers can be seen below:
1 - Show redirects
2 - Show cookies received
3 - Show all 200/OK responses
4 - Show URLs which require authentication
D - Debug Output
V - Verbose Output
-evasion: pentesters, hackers and developers are also allowed to specify the Intrusion Detection System evasion technique to use. This option also allows the use of reference numbers to specify the type of technique. Multiple number references may be used:
1 - Random URI encoding (non-UTF8)
2 - Directory self-reference (/./)
3 - Premature URL ending
4 - Prepend long random string
5 - Fake parameter
6 - TAB as request spacer
7 - Change the case of the URL
8 - Use Windows directory separator ()
-Format: One might require output/results to be saved to a file after a scan. This option does exactly that. The -o (-output) option is used; however, if not specified, the default will be taken from the file extension specified in the -output option. Valid formats are:
csv – for a comma-separated lists
htm – for an HTML report
txt – for a text report
xml – for an XML report
-host: This option is used to specify host(s) to target for a scan. It can be an IP address, hostname, or text file of hosts.
-id: For websites that require authentication, this option is used to specify the ID and password to use. The usage format is "id:password".
-list-plugins: This option will list all plugins that Nikto can run against targets and then will exit without performing a scan. These can be tuned for a session using the -plugins option.
The output format is:
Plugin name
full name - description
-no404: This option is used to disable 404 (file not found) checking. This reduces the total number of requests made to the web server and may be preferable when checking a server over a slow internet connection or an embedded device. However, this will generally lead to more false positives being discovered.
-plugins: This option allows one to select the plugins that will be run on the specified targets. A comma-separated list should be provided which lists the names of the plugins. The names can be found by using -list-plugins.
There are two special entries: ALL, which specifies all plugins shall be run and NONE, which specifies no plugins shall be run. The default is ALL.
-port: This option specifies the TCP port(s) to target. To test more than one port on the same host, one can specify the list of ports in the -p (-port) option. Ports can be specified as a range (i.e., 80-90), or as a comma-delimited list, (i.e., 80,88,90). If not specified, port 80 is used.
-Pause: This option can be used to prevent tests from being blocked by a WAF for seeming too suspicious. It defines the seconds to delay between each test.
-timeout: It is sometimes helpful to wait before timing out a request. This option specifies the number of seconds to wait. The default timeout is 10 seconds.
-useproxy: This option is used in the event that the networks connected to require a proxy. This option asks Nikto to use the HTTP proxy defined in the configuration file.
-update: This option updates the plugins and databases directly from cirt.net.
Scanning vulnerable websites with Nikto
We shall now use Nikto to scan http://webscantest.com which is a website intentionally left vulnerable for testing web application vulnerabilities. Typing on the terminal “nikto” displays basic usage options.
Specifying the target host is as simple as typing the command “nikto –host target” where target is the website to scan. The options discussed above can be used to refine the scan to the desires of the pentester, hacker or developer.
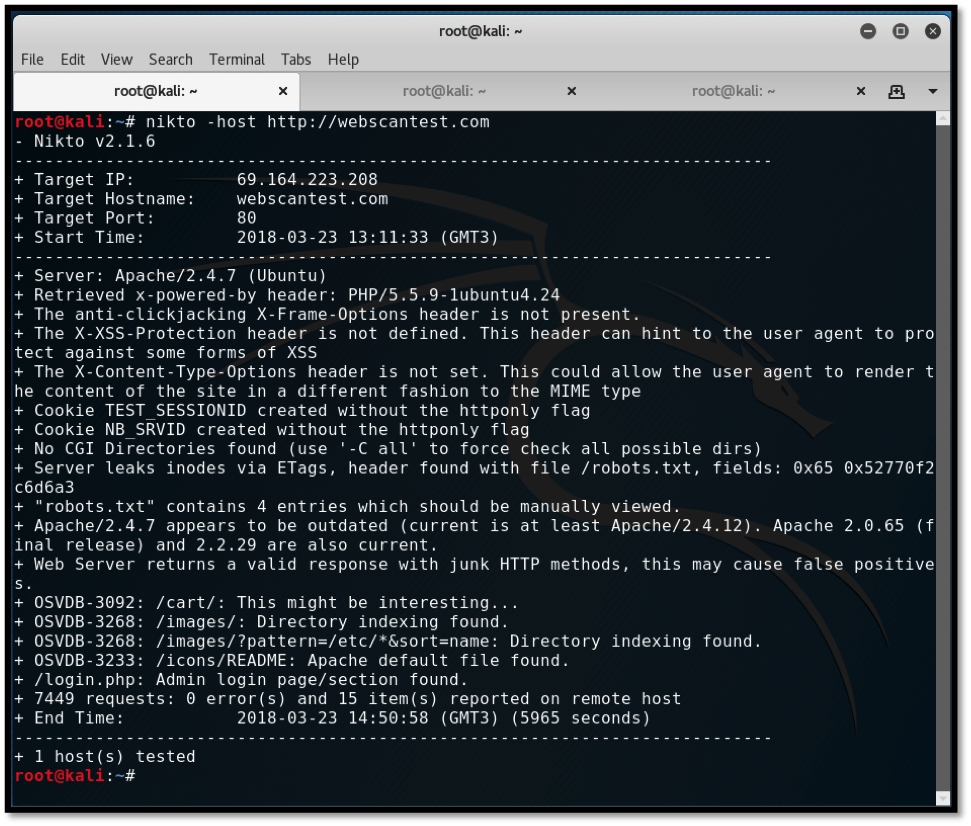
Once the scan is complete, results will be displayed in a format that closely resembles the screenshot below:
Bear in mind that report generation is allowed in the desired format as discussed previously.
From the scan results, we can clearly see the identified issues along with their OSVDB classification. Nikto reveals:
- Server details such as the web server used,
- txt file with the number of present entries,
- Directory indexing that allows anyone browsing the website to access backend files and
- Apache web server default installation files.
Let's take a look at the identified issues on our web browser.
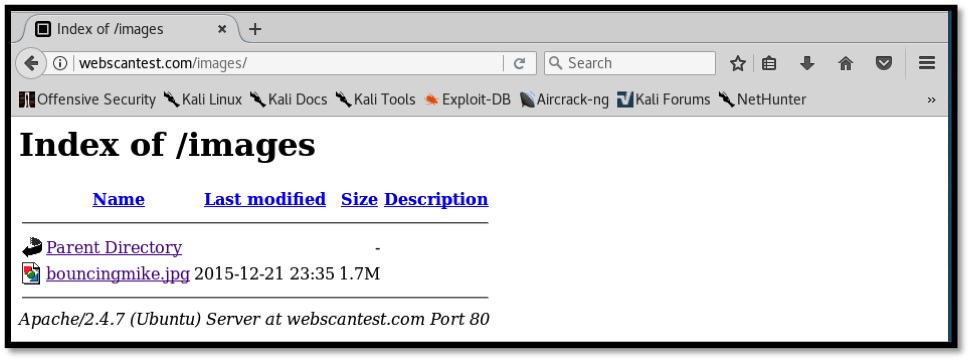
Directory indexing
A directory indexing vulnerability allows anyone visiting the website to access files that reside on the back end of the web server. These might include files containing code, and in some instances, even backup files. This results from poor permissions settings on directories within the website, allowing global file and folder access. In some instances, it is possible to obtain system and database connection files containing valid credentials.
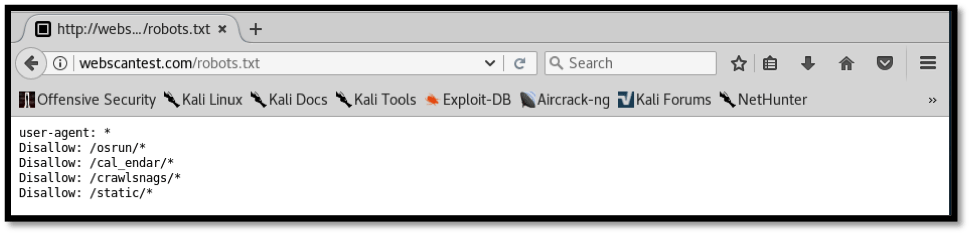
Directory indexing can be avoided by setting up appropriate permissions on files and directories within the web server. This can be done by disallowing search engine access to sensitive folders such that they are not found on the public internet as well as reviewing file and folder permissions within the web server to ensure access is restricted only to the required directories. The screenshot below shows the robots.txt entries that restrict search engines from being able to access the four directories. It should however be noted that this is not a permanent solution and file and folder permissions should be reviewed.
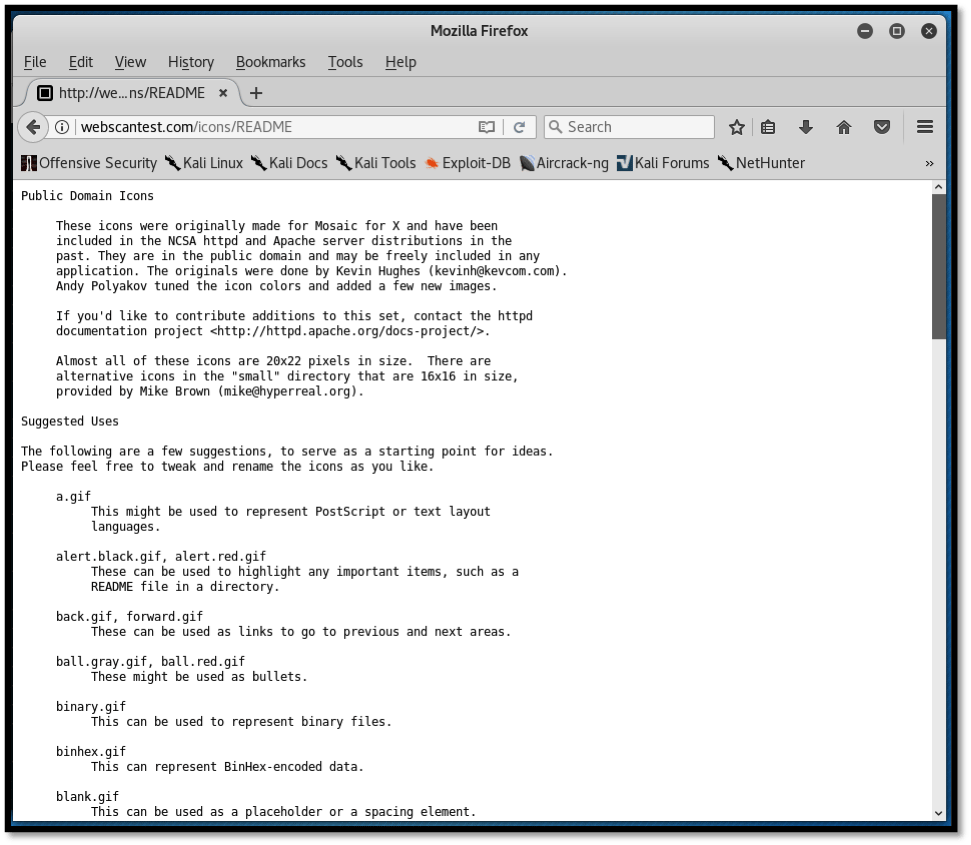
Default installation files
Default installation files may reveal a lot of information concerning the web server, and this may allow attackers to craft attacks that specifically target the web server as per the disclosed information. The screenshot below shows an example of a default file discovered by Nikto.
Default installation files need to be removed or hidden lest they disclose sensitive information concerning the web server.
Become a Certified Ethical Hacker, guaranteed!
Get training from anywhere to earn your Certified Ethical Hacker (CEH) Certification — backed with an Exam Pass Guarantee.
Conclusion
The Nikto web application scanner is the ultimate light weight web application vulnerability scanner that is able to run on the lowest specification computer system. The fact that it is updated regularly means that reliable results on the latest vulnerabilities are provided. This article should serve as an introduction to Nikto; however, much more is possible in terms of results and scanning options with this tool, for example the tampering of web requests by implementing Burpsuite. Check it out and see for yourself.