Pentesting SAP applications : An introduction
SAP (Systems-Applications-Products) is a software suite that offers standard business solutions; it is used by thousands of customers across the globe to manage their business. In other words, SAP systems provide the capability to manage financial, asset, and cost accounting, production operations and materials, personnel and many more tasks. Before we jump into SAP security and penetration testing, here are a few things that you need to understand.
Solutions: SAP offers various solutions that are targeted to specific areas. For example below are some of the commonly used SAP solutions.

What should you learn next?
Ex: CRM (Customer Relationship Management), ERP (Enterprise Resource Planning), PLM (Product Life Cycle Management), SCM (Supply Chain Management), SRM (Supplier Relationship Management)
SAP ERP is the most widely used solution that deals with key business functions of an organization.
Modules: Each solution has various modules that implement organization processes. Modules can be called locally or remotely. Below are some of the commonly used modules:
Ex: SAP Financial Accounting (FI), SAP Controlling (CO), SAP Sales and Distribution (SD), SAP Production Planning (PP), SAP Materials Management (MM), SAP Quality Management (QM), SAP Human Capital Management (HCM)
Platforms: Modules are linked together and integrated by their platforms. SAP Netweaver platform is primary technology and computing platform of SAP. Here is a list of other platforms:
Ex: SAP Enterprise Services Architecture, SAP NetWeaver Platform, SAP Business Connector, SAP HANA
Client: Client in SAP refers to a legally and organizationally independent unit such as a company or business unit. It is identified by a 3-digit number. Default clients are 000, 001, and 066.
Transaction: It refers to sequence of steps aimed at performing an operation in SAP database. Each transaction is identified by a transaction code such as SU01, FK01 and so on.
SAP runs on multiple operating systems and databases. ABAP is the main programming language used by SAP platforms.
SAP penetration testing
A penetration test on SAP systems would help you locate a wide range of issues to which the system might be vulnerable. SAP systems are seen by several developers as secure and robust because of the in-built authorization features etc. While this is true to some extent there would also be some issues which result due to misconfigurations, default installations etc. In ideal scenario, you would be provided with a SAPGUI version installed on a machine. SAPGUI is the GUI client that allows a user to access SAP functionality in SAP applications. You can also download SAPGUI by from the official SAP site. SAPGUI is the traditional fat client application but these days you find several SAP application being accessed through a web console. In any case, the following includes issues related to both SAPGUI as well as web console based installations. Let us now proceed and look at the vulnerabilities to which SAP systems are prone.
Use of default passwords
SAP Systems create the default users such as SAP*, DDIC and EARLYWATCH during the installation process in the clients. Below table lists out the username and the default passwords for those accounts. Among these SAP* has super user access and can give access to lot of sensitive functions. While pen testing a SAP application you can try logging in with any of these accounts. Here is a list of users and default passwords used by SAP applications.
In this context, it's important to note that SAP* account should not be deleted and instead be deactivated. This is because SAP* account is hard-coded in ABAP systems and does not require a user master record. If a user master record for SAP* does not exist in a client, then anybody can log on to the ABAP as the user SAP* using default password PASS. Most of the developers wrongly delete the account when this issue is reported. Therefore, the recommended solution is to deactivate the SAP* account and create another super user account.
Unencrypted transmission (lack of SNC protection)
When you are testing SAPGUI application (not the web based), you will notice that most of the communication happens over proprietary network protocols. There are two important protocols that SAP uses for communication:
- DIAG: The communication between SAPGUI and SAP Application Server is usually done using proprietary protocol called DIAG (Dynamic Information and Action Gateway).
- RFC: The communication among various SAP Net Weaver application servers is done using network protocol called RFC (Remote Function Call).
These protocols are defined on top of TCP/IP stack. Both DIAG and the RFC protocols do not support authentication and encryption while transmitting the data. What this means is an attacker who is present in the same network can simply see the passwords by sniffing the traffic. Unfortunately, tools such as Wireshark will not automatically sniff this traffic as it is compressed. However, there are SAP dissection plugins that you can install to see the traffic. Once installed the tool can dissect the main headers used by the DIAG protocol. Core Labs SAP dissection plug-in and SAP DIAG plugin by Positive Research Center are the two plugins available. Once the traffic is captured look for the destination IP address or usually for port 3200 as shown in the below screenshot. Other tools such as Cain & Abel, SapCap would also do this job.
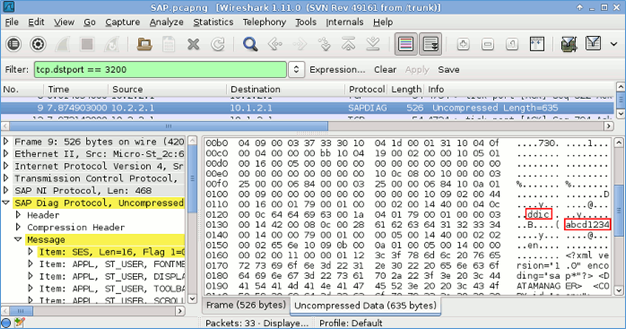
The solution to this is to use SNC (Secure Network Communications). SNC encrypts all the communication that happens between the various client and server components of the SAP system that uses RFC or DIAG. SNC also supports various cryptographic algorithms, which can be used by the developers for increased data protection. In addition, SNC cannot be implemented between SAP Application Server and SAP Database. Hence, it is recommended to have both Application server as well as the database in the same network. SNC offers three levels of security. They are:
- Authentication only: With this, the system verifies the identity of the communication partners only during authentication. This is the minimum protection level offered by SNC. No data protection is provided in this and hence is not recommended.
- Integrity protection: With this SAP verifies the integrity of the communication. Any changes made to the data between the two end points of communication is detected.
- Privacy protection: When using privacy protection, the system encrypts the messages being transferred so that confidentiality is ensured. Privacy protection also includes integrity protection of the data. This is the maximum level of protection provided by SNC.
Become a Certified Ethical Hacker, guaranteed!
Get training from anywhere to earn your Certified Ethical Hacker (CEH) Certification — backed with an Exam Pass Guarantee.
No account lockout mechanism
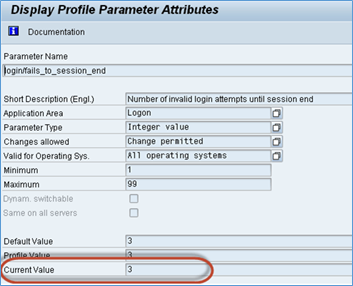
All applications are supposed to lock the user accounts upon encountering more than certain failed login attempts. In other case, that would lead to brute force attacks using which an attacker can steal guess the password. The parameter login/fails_to_user_lock specifies the allowed number of wrong attempts. Default value is 12. There is one more parameter login/fails_to_session_end that specifies the number of times that a user can enter an incorrect password before the system ends the session. Below is a screenshot of the settings screen.
In this article, we have seen introduction to SAP and a few vulnerabilities that are present in the SAP systems. In the next part, we will continue this topic and discuss a few other vulnerabilities that are to be tested during penetration testing of SAP applications.







