pWeb Suite - A Set of Web Pentesting Tools

pWeb Suite (formerly known as pCrack Suite) is a set of Perl-based penetration testing tools primarily focused on web application security and vulnerability testing. This tool is brought to you by Douglas Berdeaux, a.k.a Trevelyn, who is the founder of Weaknet Laboratories and the lead developer of known open source security projects and tools like WEAKERTHAN Linux (a penetration testing distro aimed for wireless penetration testing and web application security), Warcarrier OS (Live DVD for WiFi, GPS, Bluetooth, and Radio hacking), WiFiCake-NG, WardriveSQL, GPS-Parser-ng, WPA Phishing Attack for EAP Phishing, SSWR (Scripted Security for Wireless Routers), Catchme-NG, Perlwd (Perl UNiX MD5 HASH Cracking application), and many more.

FREE role-guided training plans
At first, pWeb Suite was only slated for WEAKERTH4N Linux but then the developer decided to release it to the public for other Linux distros, specifically the penetration testing distributions like BackTrack, Kali, Backbox, Blackbuntu, etc. This happened when I sent him a message in LinkedIn a year ago that I would like to try out the tools he just made for web penetration testing which was featured in his SOLDIERX HDB profile. The latest version of the pWeb suite can be downloaded here: https://code.google.com/p/pweb-suite/downloads/list
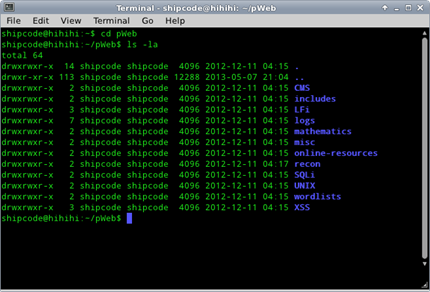
pWeb suite includes a list of cool tools that can be used for web application vulnerability testing like LFI (Local File Inclusion), RFI (Remote File Inclusion), SQLi (Structured Query Language Injection), XSS (Cross Site Scripting), Reconnaissance, and other utilities for Mathematics / Hashes / Passwords, wordlist utilities, logs and many more. Below are some of the tools which I love from this suite:
WordPress Sniper or wp_sniper
WordPress Sniper is an automated vulnerability finding tool for WordPress CMS (content management system) which allows you to utilize the information of exploits for the said CMS gathered from Exploit-DB through the use of the Scrape script, a tool buddy of wp_sniper which can also be found under the CMS directory.
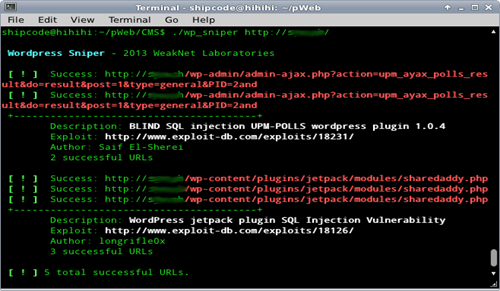
Sample Usage: ./wp_sniper http://hello.ph/ <options>
Options (as detailed by the help menu):
-d (check default installation files: /license.txt, /README.html, /wp-admin/install.php, /wp-admin/install-helper.php, /wp-admin/setup-config.php, /wp-config-sample.php, and /?s=')
-r (random wait time between GET requests (5000ms))
Simple Text Google Browser or stgb
This tool allows you to utilize Google dorks and outputs the results in your terminal emulator without having multiple windows. This can be found under the recon directory.
Sample Usage: ./stgb intitle:"Linux"
xssPlay XSS Automation Tool
xssPlay is a tool for scanning and exploiting non-persistent XSS vulnerabilities in web apps which means it tests each GET parameter in the URL given. It also takes a screenshot (if you apply the option -s) of the defaced page by using the MozRepl Firefox browser plugin, which is why you need to open Firefox and start the MozRepl plugin then leave it open for this to work.
This tool can be found under the XSS directory.
Sample Usage: ./xssPlay -u 'http://site.com/search.php?search=' <options>
Options (As detailed by the help menu):
-s (for screenshots)
-i (specify img url to deface with)
-c (use only CSS to deface web application)
-a (m|s|x|string) (specify user agent to use, or choose random)
-o (html|txt) (specify log output type)
-r (recursive for crawling)
Vulncode
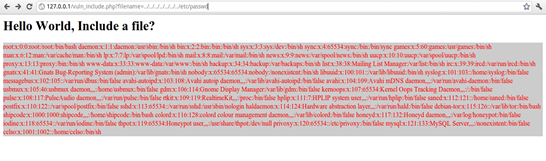
Vulncode is a PHP script that is vulnerable to Local File Inclusion (LFI) which is used for testing HelLFiRE. The code 'vuln_include.php' can be found under LFi/vulnCode directory of the pWeb suite. Below is the code itself:
[html]
INCLUDE FILE GOES HERE!</pre>
<style><!--
.boxen {
background: #ccc;
color: red;
}
--></style>
</pre>
<h1>Hello World, Include a file?</h1>
<div class="boxen"></div>
<footer></footer>
<pre>
HelLFiRE
HelLFiRE is a Local File Automation (LFI) Recon tool that is powered by Perl's Regular Expressions and is similar to Panoptic. To check the usage of HelLFiRE, just type ./HelLFiRE -h in your terminal emulator.
Basic Usage: ./HelLFiRE -u url
Added Options:
add -s seconds for sleep delay between requests.
add -a "USER AGENT" to specify USER AGENT.
Example:
./HelLFiRE -u 'http://127.0.0.1/vuln_include.php?filename=class.php' -a "Mozilla/5.0″ -s 2
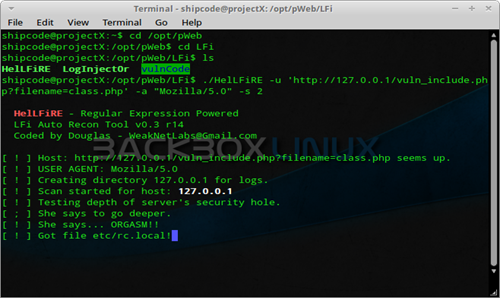
This tool allows you to retrieve all files from /etc directory by default on a Unix or Linux / GNU system which will be cloned and can be found under the ../logs/scans/127.0.0.1 directory if the attack is successful. If it says "83 (or any number) files raped from server", that means it was able to copy 83 files from the /etc directory. So if I use the command cat ../logs/scans/127.0.0.1/etc.passwd, I should be able to see something like this in the terminal:
[bash]
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/bin/sh
bin:x:2:2:bin:/bin:/bin/sh
sys:x:3:3:sys:/dev:/bin/sh
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/bin/sh
man:x:6:12:man:/var/cache/man:/bin/sh
lp:x:7:7:lp:/var/spool/lpd:/bin/sh
mail:x:8:8:mail:/var/mail:/bin/sh
news:x:9:9:news:/var/spool/news:/bin/sh
uucp:x:10:10:uucp:/var/spool/uucp:/bin/sh
proxy:x:13:13:proxy:/bin:/bin/sh
www-data:x:33:33:www-data:/var/www:/bin/sh
backup:x:34:34:backup:/var/backups:/bin/sh
list:x:38:38:Mailing List Manager:/var/list:/bin/sh
irc:x:39:39:ircd:/var/run/ircd:/bin/sh
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/bin/sh
nobody:x:65534:65534:nobody:/nonexistent:/bin/sh
libuuid:x:100:101::/var/lib/libuuid:/bin/sh
syslog:x:101:103::/home/syslog:/bin/false
messagebus:x:102:105::/var/run/dbus:/bin/false
avahi-autoipd:x:103:108:Avahi autoip daemon,,,:/var/lib/avahi-autoipd:/bin/false
avahi:x:104:109:Avahi mDNS daemon,,,:/var/run/avahi-daemon:/bin/false
usbmux:x:105:46:usbmux daemon,,,:/home/usbmux:/bin/false
gdm:x:106:114:Gnome Display Manager:/var/lib/gdm:/bin/false
kernoops:x:107:65534:Kernel Oops Tracking Daemon,,,:/:/bin/false
pulse:x:108:117:PulseAudio daemon,,,:/var/run/pulse:/bin/false
rtkit:x:109:119:RealtimeKit,,,:/proc:/bin/false
hplip:x:111:7:HPLIP system user,,,:/var/run/hplip:/bin/false
saned:x:112:121::/home/saned:/bin/false
postfix:x:110:122::/var/spool/postfix:/bin/false
sshd:x:113:65534::/var/run/sshd:/usr/sbin/nologin
haldaemon:x:114:124:Hardware abstraction layer,,,:/var/run/hald:/bin/false
debian-tor:x:115:126::/var/lib/tor:/bin/bash
shipcode:x:1000:1000:shipcode,,,:/home/shipcode:/bin/bash
colord:x:116:128:colord colour management daemon,,,:/var/lib/colord:/bin/false
honeyd:x:117:132:Honeyd daemon,,,:/var/log/honeypot:/bin/false
iodine:x:118:65534::/var/run/iodine:/bin/false
thpot:x:119:65534:Honeypot user,,,:/usr/share/thpot:/dev/null
privoxy:x:120:65534::/etc/privoxy:/bin/false
mysql:x:121:133:MySQL Server,,,:/nonexistent:/bin/false
celso:x:1001:1002::/home/celso:/bin/sh
postgres:x:122:134:PostgreSQL administrator,,,:/var/lib/postgresql:/bin/bash
lightdm:x:123:135:Light Display Manager:/var/lib/lightdm:/bin/false
arpwatch:x:124:136:ARP Watcher,,,:/var/lib/arpwatch:/bin/sh
SimplyMySQLi or SMSI
SMSI is a simple and lightweight MYSQL Injection vulnerability scanner tool that dumps the database of the web application that is vulnerable to SQL injection. This script can be found under the SQLi directory.
Sample Usage: ./smsi -u '< URL >' -a < User Agent >
LogInject0r
LogInject0r is a script that can also be found under the LFi directory. It is used for finding out the log file of the web server that is vulnerable to Local File Inclusion and clones the /etc directory through injection of PHP exec() functions in the log.
Sample Usage: ./LogInject0r -u < URL >
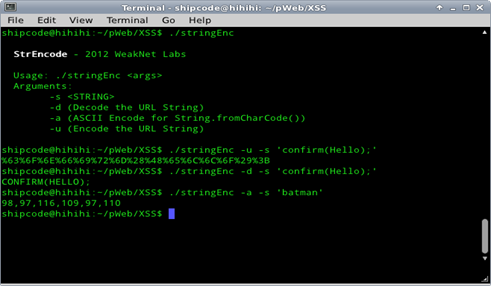
StrEncode
StrEncode is an XSS (Cross Site Scripting) String Encoding Tool which allows you to decode or encode a string URL. It can also do ASCII Encoding for String.fromCharCode().
FileScope
FileScope is a web server reconnaissance tool that allows you to use your own customized wordlist file to brute force web directories and files which is useful for information gathering. You can also recursively scan the directories of the web server by using the option -r.
FileScope can be found under the recon directory.
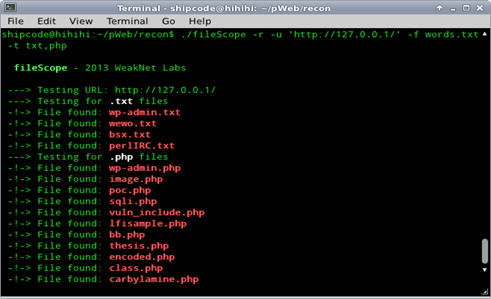
Sample Usage: ./fileScope <options>
Options (As detailed by the help menu):
-f <wordlist>
-u <URL>
-s <seconds to sleep between requests>
-t <file types, comma separated: js,tar,txt>
-r (make search recursive)
Havijmd5BF
Havijmd5BF is a script that leverages Havij Report HTML file online MD5 (Message-Digest algorithm 5) brute forcer. This script can be found under the online-resources directory.
md5online
md5online is a script that encodes your string into MD5 by leveraging md5-lookup.com. This script can be found under the online-resources directory.
pBinCracker
pBinCracker is a script that leverages pasteBin and Paste2 RAW MD5 cracking softwares. This script can be found under the online-resources directory.
ripemd160online
ripemd160online is a script that leverages ripemd-lookup.com, an online RIPEMD-160 (RACE Integrity Primitives Evaluation Message Digest) algorithm lookup tool. This script can be found under the online-resources directory.
sha1online
sha1online is a script that leverages sha1-lookup.com, an online Secure Hash Algorithm 1 (SHA-1) lookup tool. This script can be found under the online-resources directory.
sha256online
sha256online is a script that leverages sha-256.sha1-lookup.com, an online SHA-256 (Secure Hash Algorithm 256-bit message digest algorithm) lookup tool. This script can be found under the online-resources directory.
References:
http://weaknetlabs.com/linux/pcrackdemo/pcrackdemo.html
http://pentestlab.org/pweb-suite-perl-based-web-app-penetration-testing-tools/
(My old article about pWeb suite)
http://pentestlab.org/hellfire-local-file-automation-tool-of-pweb-suite/
(My old article about HelLFiRE)
https://code.google.com/p/pweb-suite/w/list

FREE role-guided training plans







