Red Team: C2 frameworks for pentesting
C2 frameworks — the abbreviation to the Command and Control (C&C) infrastructure — are how red teamers and pentesters can control compromised machines during security assessments.
Although implemented on other models (P2P or out of band), C2 frameworks are typically designed under a client-server architecture and used to communicate with systems via a network connection. These kinds of systems mimic benign network traffic to avoid detection and bypass network security appliances. Many techniques can be used to establish command and control based on different levels of stealth depending on the victim’s network, structure, and defenses (MITRE ATT&CK). In detail, MITRE presents 16 distinct C2 techniques grouped into several sub-techniques and observed in past cyber incidents.
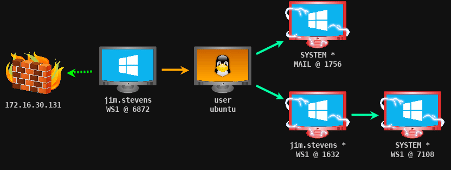
From the auditor’s perspective, when an initial foothold is established, that point can move laterally through the internal network, using the C2 capabilities and jumping to other vulnerable or misconfigured network points. As expected, the first compromised machine is a valuable target. It is typically used as a pivot to access more sensitive network parts such as file servers and domain controllers.
As C2 is a bi-directional application, sensitive information can be easily exfiltrated from the environment. In the last few months, several cyberattacks were registered with a lot of stolen sensitive data, from military documents to credit cards and PII. To finish the chain, criminals can efficiently deploy data encryption malware such as ransomware via C2 to extort their victims.

What should you learn next?
C2 post-exploitation frameworks
Here, we present the most used C2 post-exploitation frameworks during internal assessments.
Cobaltstrike
Cobaltstrike is one of the most used platforms worldwide that allows the deployment of a beacon agent on the victim’s machine. This kind of agent provides a lot of functionalities, including keylogging, file upload and download, socks proxy, VPN deployment, privilege escalation techniques, mimikatz, port scanning and the most advanced lateral movements.
The Cobalstrike beacon uses a file-less approach under a stageless or multistage shellcode typically loaded by exploring a vulnerability or a weakness that will execute in memory the final payload without touching the disk. It supports C2 connection via HTTP, HTTPS, DNS and SMB protocols. In addition, Cobalstrike also provides a development toolkit called Artifact Kit that facilitates customized shellcode loaders.
URL: https://www.cobaltstrike.com/
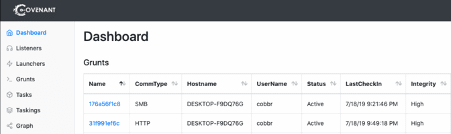
Covenant
Covenant is a collaborative C2 framework designed essentially for red teaming assessments. This post-exploitation framework supports .NET core and is cross-platform. It supports Windows, macOS and Linux-based OS. Covenant also provides a pre-configured Docker image to facilitate its installation.
The Covenant agent known as “Grunt” is developed in C#, and it can be customized directly on the C2 web portal. Many features are provided, such as lateral movement techniques, mimikatz, exfiltration scripts and so on. More details about this open-source project can be found on the GitHub page.
URL: https://github.com/cobbr/Covenant/
Sillenttrinity
Sillenttrinity is an asynchronous and multi-server command and control framework developed in Python3 and .NET DLR. This platform uses embedded third-party .NET scripting languages and dynamically calls .NET APIs; the author entitled BYOI (Bring Your Own Interpreter) technique.
This tool uses a dedicated team server with many modern features into a powerful C2 framework. The usage of WebSockets allows effective real-time communication between the team server and the agents installed on the victims’ machines. In detail, SILENTTRINITY uses Ephemeral Elliptic Curve Diffie-Hellman Key Exchange to encrypt all C2 traffic between the team server and its implant.
One of the appreciated features is its modularity — users can modify any module easily.
URL: https://github.com/byt3bl33d3r/SILENTTRINITY
Koadic
Koadic is a Windows post-exploitation framework that uses Windows Script Host (JScript/VBScript) and supports all Windows versions from Windows 2000 to Windows 11.
Koadic is an open-source tool and is available on Github. This framework is written in Python, and its payloads are JavaScript-based with XOR encryption. The agents are installed on the target machines using the default mshta or using the default mshta or Microsoft HTML Application stagers.
URL: https://github.com/zerosum0x0/koadic
Metasploit
The Metasploit framework is a popular tool distributed along with Kali Linux distribution and can be used to find vulnerabilities on networks and servers. As it is an open-source tool, it can be customized by operators and used with many operating systems, including Android, iOS, macOS, Linux, Windows, Solaris, etc.
Meterpreter is equipped with many features, including staged and non-staged payloads to enable port forwarding between networks.
URL: https://www.metasploit.com

FREE role-guided training plans
Merlin
Merlin is a C2 that uses HTTP/1.1, HTTP/2 and HTTP/3 protocols to evade detection and communicate with its agents. Merlin is a cross-platform tool written in Goland and capable of working in several operating systems.
Each merlin compilation will generate unique payloads capable of avoiding AV detection from the detection point-of-view, as demonstrated in this article. It uses a client-server architecture and provides the most advanced features of red teaming presented on other C2 frameworks in the market. As it is an open-source project, operators can customize Merling agents, their modus operandi and how it is loaded into the memory.
URL: https://github.com/Ne0nd0g/merlin
Sources
- What is C2, Varonis
- Merlin, Infosec Institute