Top five open source intelligence (OSINT) tools [updated 2021]
In this article, we will look at the top five open-source intelligence tools.
Before we jump directly into the tools, it is essential to understand what open-source intelligence (OSINT) is and how it can benefit researchers, malware actors, organizations and more.

What should you learn next?
What is OSINT?
OSINT refers to a collection of data from public sources to be used in an intelligence context, and this type of open source information is often missed by link-crawling search engines such as Google. As per the US Department of Defense, OSINT is “produced from publicly available information that is collected, exploited, and disseminated in a timely manner to an appropriate audience for addressing a specific intelligence requirement.”
Top 5 OSINT tools
Below are the Open Source Intelligence Tools most often used by penetration testers and even malware actors to gather information about the specified target. Information gathering plays an essential part in any penetration activity. The data that we get from the information-gathering phase reveals a lot about the target, and in the digital world, there are huge footprints of assets exposed to the outside world.
The challenge for penetration testers and malware actors is to make sense of these humongous chunks of data in order to know all the possible traits of intended targets. Below are some of the common Open Source Intelligence tools used by malware actors and penetration testers.
Note: We will only see one or two features for each OSINT tool mentioned below to see how much value they can bring in during the reconnaissance phase.
Maltego
Maltego is developed by Paterva and is an inbuilt tool in Kali Linux (ships with community edition). Maltego helps to perform a significant reconnaissance against targets with the help of several built-in transforms (as well as providing the capability to write custom ones). To use Maltego first, the user should be registered on the Paterva site.
After registering, the user can create a new machine or run machines to run transforms on the target. After configuring that, the configured machines need to be started. There are various footprints built inside Maltego which can be run against the target. Maltego will start to run all the transforms with the Maltego servers.
Expected results might be that domain-to-IP conversion has happened, netblock will be identified, AS number is also identified, locations and other phrases as well. These are all icons in Maltego, and it gives a detailed view of all these icons. Researchers can continue this process to dig more information about the target. It’s an absolutely fantastic tool to track the footprints of a single entity over the internet.
Recon-ng
Recon-ng is another useful tool to perform reconnaissance on the target. It is also built into Kali Linux. Recon-ng has various modules built in, and its usage somewhat resembles that of Metasploit. Below is the welcome screen of Recon-ng on Kali Linux.
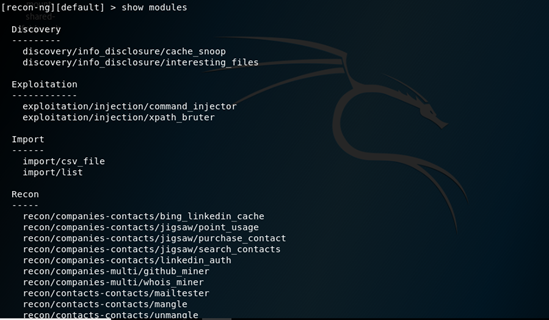
As mentioned above, Recon-ng has various inbuilt modules. A snippet of that is shown below.
Workspaces can be created to carry out all operations inside that. As soon as the workspace is created, the user will be redirected to that workspace. Once inside the workspace, then the domain can be specified using add domain <domainname>.
After the domains are added into Recon-ng, Recon-ng modules can be used to extract information about this domain. There are some excellent modules like bing_domain_Web and google_site_web to find additional domains related to the initial target domain. The output of these domains will be all indexed domains to these search engines. Another handy module is bing_linkedin_cache, which can be used to fetch the email addresses related to the domain which can further be leveraged to perform social engineering. So, with other modules, we can get additional information regarding targets. Thus, Recon-ng is a great tool and must be in the toolkit of researchers.
theHarvester
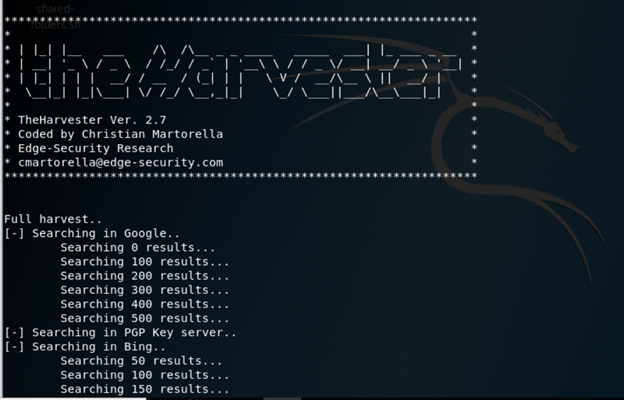
theHarvester is an excellent tool for collecting info from the specified target. theHarvester is inbuilt into Kali, is very fast and is much simpler to use than Recon-ng to collect basic information. Below is the welcome screen of theHarvester in Kali Linux.
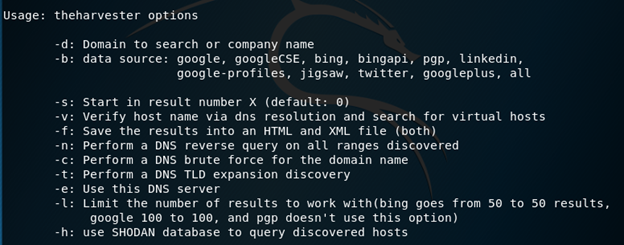
We can see it trying to fetch results from Google, Bing, PGP key servers and so on. These parameters (and others) are explained in the below figure.
Below are the details that we can get from theHarvester:
- Email address related to the domain
- Results of hosts and virtual hosts found in search engines
We can see that theHarvester is also very useful to extract information from the specified targets, and that it has a fascinating array of features.
Shodan
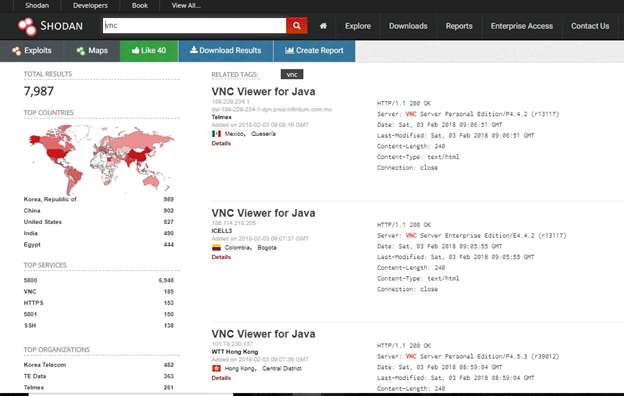
Shodan is touted as the “search engine for hackers” because it gives a huge footprint of devices connected online. It is a gold mine for researchers to see the exposed assets.
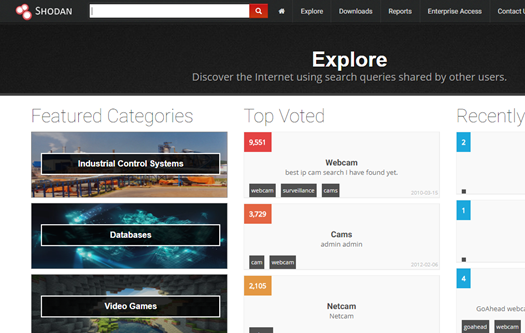
Shodan also gives the top most used searches by the community, like below:
For example, one can see the connected webcams, netcams, traffic lights and so on. Below are some of the use cases from Shodan:
So Shodan is an excellent tool for finding the fingerprint of connected assets; their details; their vulnerabilities and so on. Researchers can easily imagine how much they can push boundaries of this to gather the deep level of information.
Google dorks
Search engines provide us much information and index a great deal of information, too, which can be used to gather information about a target. Google dorks provide such information through the usage of some operators, which are otherwise difficult to extract using simple searches.
Below are some of the operators used in Google dorking:
- Intitle: Looks out for mentioned words in the page title
- Inurl: Looks out for mentioned words in the URL
- Filetype: This is used to find filetypes
- Ext: This is used to identify files with specific extensions. Think of using it for finding such files like .log, which are not supposed to be indexed
- Intext: This helps to search for specific text on the page
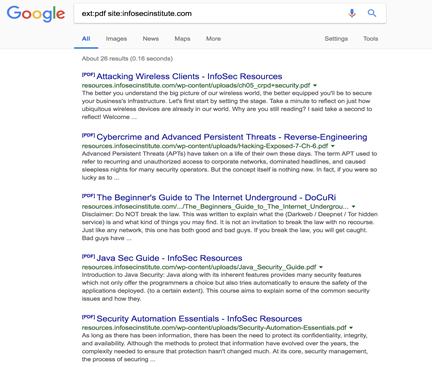
Below is an example of finding all indexed PDF files
Google dorks have been in place since 2002, and they still give good results and can prove very handy very performing reconnaissance.

FREE role-guided training plans
Conclusion
In this article, we have investigated some of the most common OSINT tools used by researchers. Their tools are very powerful when used alone but can be very lethal when used with each other.