Top tools for mobile iOS assessments
The mobile landscape has become one of the main challenges for IT security teams from a security viewpoint in the last few years. With the digital evolution, a small device can access critical applications and sensitive data from organizations, with the BYOD (Bring Your Own Device) continuing to grow and create a new paradigm between the organizations and their employees. In this sense, the security and perimeter of risk of these devices should be properly managed.

What should you learn next?
Top tools for iOS assessments
Mobile security framework (MobSF)
MobSF is the short form to mobile security framework, and this is an automated framework to execute static and dynamic mobile assessments. This tool can perform tests under Android, iOS and Windows applications and find malicious content such as URLs, bad source-code, IP addresses, encrypted blocks and more.
This framework is equipped with a REST API for integration with DevSecOps pipelines. MobSF is capable of performing runtime security assessments and interactive and instrumented tests using its built-in dynamic analyzer.
URL: https://github.com/MobSF/Mobile-Security-Framework-MobSF
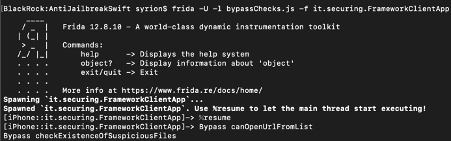
Frida toolkit
Frida is a toolkit designed to allow dynamic code instrumentation. This tool can inject custom JavaScript code into a process and modify its behavior in runtime.
By using Frida, injecting code to bypass execution restrictions (root detection, SSL pinning etc) and techniques that developers use to secure mobile applications is possible and easy.
Frida is also equipped with a set of standalone tools:
- frida-ps: command-line tool for listing processes
- frida-trace : a tool for dynamically tracing calls and methods
- frida-discover: a tool for discovering internal functions
- frida-ls-devices: command-line tool for listing attached devices
- frida-kill: command-line tool for killing processes
URL: https://frida.re/docs/home/
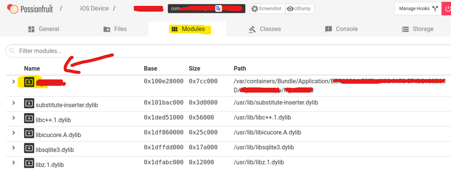
passionfruit
Passionfruit is a GUI webapp developed to interact with iOS applications and dump and analyze their content easily.
With this app, it’s possible to list all URL schemas, check signatures, list metadata, see if the app is encrypted, check loaded frameworks, log SQLite operations, bypass jailbreak detection, list Objectiv-C classes and so on. Dump keychain, binary cookies and user defaults are also possible.
This is, in fact, an application that should be part of your mobile arsenal for red teaming assessments.
URL: https://github.com/chaitin/passionfruit
Grapefruit
Grapefruit is a runtime application instrumentation tool for iOS. This tool is very similar to the passionfruit app but with a different layout and many new features. It is under development but is the next generation of passionfruit.
URL: https://github.com/ChiChou/Grapefruit
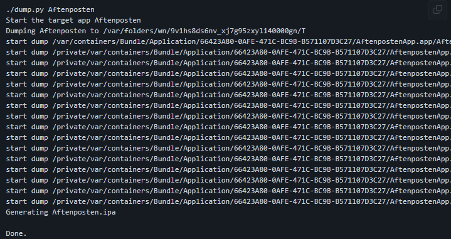
frida-ios-dump
This is a small script that can be the best friend when analyzing IPA (iOS) files. In short, it decrypts IPA files from jailbroken devices.
After that, the application source code can be analyzed and reversed by using radare2 or other tools.
URL: https://github.com/AloneMonkey/frida-ios-dump
radare2
Radare is a portable reversing framework, open-source and with a lot of features, including:
- Disassemble (and assemble for) many different architectures
- Debug with local native and remote debuggers (gdb, rap, webui, r2pipe, winedbg and windbg)
- Run on Linux, *BSD, Windows, OSX, Android, iOS, Solaris and Haiku
- Perform forensics on file systems and data carving
- Be scripted in Python, Javascript, Go and more
- Support collaborative analysis using the embedded web server
- Visualize data structures of several file types
- Patch programs to uncover new features or fix vulnerabilities
- Use powerful analysis capabilities to speed up reversing
- Aid in software exploitation
URL: https://rada.re/r/
Objection
Objection is a tool powered by Frida and built to help experts execute their mobile assessments without needing a jailbroken or rooted mobile device.
This tool is composed of a group of features, including:
- Root detection bypass
- SSL pinning bypass
- Dump Keystore
- Dump Android Heap
- Monitors Android copy/paste buffer cache
- Hook a method(s) of a class in runtime
- Execute custom Frida scripts; and
- Work with the Android intents
URL: https://github.com/sensepost/objection

What should you learn next?
Red teaming and IOS assessment
This article compiles considerations on the iOS landscape, and what red teaming tools should be selected to audit iOS mobile apps. Nonetheless, it’s important to notice that each tool has its features and goals, so the tools used must be selected depending on the priority and features to secure.
Other tools and practical examples how to reverse IPA applications here.
Sources
- IPA reversing labs, GitBook Segurança-Informática
- Mobile Pentest guide, GitHub