Top tools for red teaming
Cyberattacks make headlines every day. The pathways utilized by criminals are vast, sometimes sophisticated and stealthy, a clear sign of constant improvement and a lot of research to think and find the best way to do it.
This article is not compiling an extensive list of red teaming tools but lists those used often by criminals in the wild. In contrast, it’s also intended to provide valuable information for red and purple teams to proactively detect and track threats with more exactness in real-time.

FREE role-guided training plans
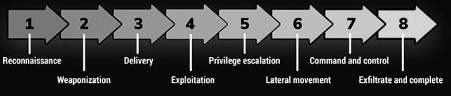
To create a short index and group the tools into single blocks, we will present them according to the red teaming attack approach proposed below.
Reconnaissance
This is the start-point when we perform a red teaming assessment. Some online (passive recon) and offline (active recon) tools can be used to collect intel and sensitive information about a person, company, or nation.
Shodan
Shodan is a search engine to identify IoT devices over the Internet. Due to the large deployment of IoT devices on the Internet networks and, in general, with poor security, these devices are a privileged starting point from the attack's point of view.
Google-dorks and Google Hacking Database: Search engines are the best friend to find something gathered and indexed by automatic bots. We can define single queries, so-called “google dorks” that can reveal compromised and sometimes sensitive information about a targeted search.
Crt.sh
crt.sh is a useful distributed database with a web interface to find SSL certificates and certificate transparency logs. Using this tool, we can discover domain names, internal certificates with internal names/domains, emails, or other sensitive information exposed to the external surface.
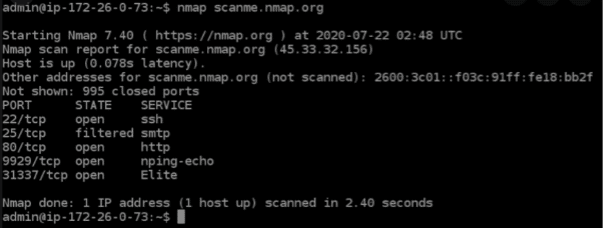
Nmap
Nmap is one of the well-known tools for active reconnaissance. It is very intuitive and is a potent scanner with many features capable of discovering assessments, associated information, and even running a panoply of exploits (nse scripts).
Weaponization
This phase is the moment of using the information collected on the reconnaissance step and attacking the target. In this phase, we need to perform some research to find the best payload and evading techniques to bypass defenses. Weaponization involves the creation of payloads, infecting malicious documents, preparing social engineering schemas before targeting the victim.
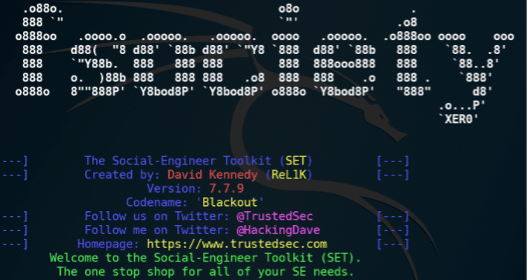
SET
Social Engineering Toolkit (SET) is an open-source tool that copulates many pre-computed attacks and techniques for social engineering purposes. This tool includes the clone of legitimate websites, delivery of social engineering campaigns, sending mass emails, and so on.
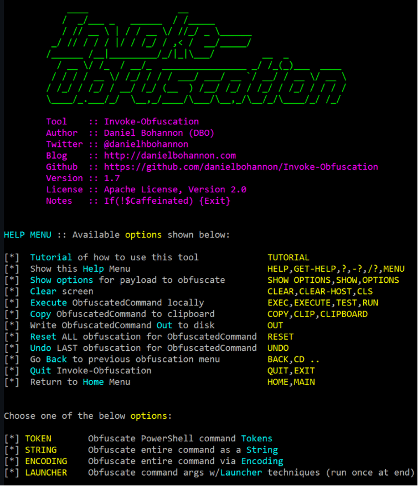
Invoke-Obfuscation
Invoke-Obfuscation is a tool capable of obfuscating power shell scripts and commands. Red teamers can create custom and obfuscated scripts to evade AV and EDR detection with this tool in place.
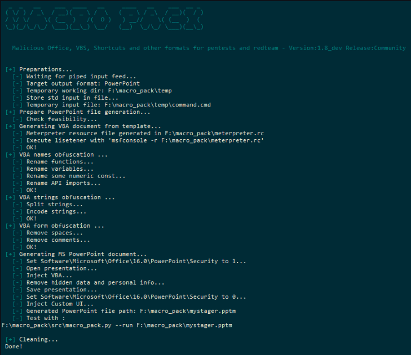
Macro_pack
Macro_pack is a tool used to automatize obfuscation and generation of MS Office documents, VB scripts, and other formats for red teaming purposes. For example, this tool can be useful for launching a CobalStrike beacon directly from a Word document — the usual modus operandi of Emotet malware.
Delivery and exploitation
Delivery and exploitation are two phases grouped into a single task because it is here that the execution of an attack is started. This phase involves obtaining a foothold on the target, and many techniques are executed to deliver the payload cleverly created in the previous step.
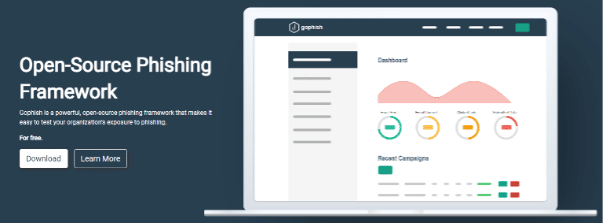
Gophish
Gophish is an open-source phishing toolkit that can set up and execute phishing engagements and security awareness training.
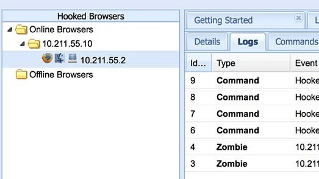
The Browser Exploitation Framework
BeEF is the short name for The Browser Exploitation Framework. It is a security framework that allows client-side attack vectors. BeEf bypasses the perimeter and allows access to the target by taking advantage of a simple web browser.
Privilege escalation
After executing the previous phases with success and obtaining a foothold, it’s time to escalate our privileges on the target machine (privesc). The most used scenario on privesc landscape is to escalate from user rights to admin or root.
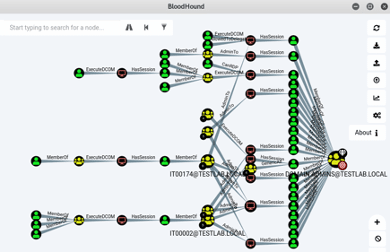
BloodHound
BloodHound is the most famous dog within the offensive side of cybersecurity. This tool is useful for both red and blue teams and is used to visualize active directory (AD) networks reveal access control lists, users, and relationships. To use BloodHound, a valid AD user is needed. It can be obtained from leaked databases or by poisoning the internal network, for instance, taking advantage of the Responder tool.
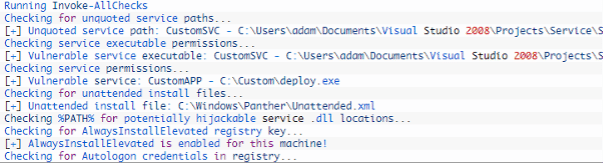
PowerUp
PowerUp is a PowerShell tool capable of checking for misconfigurations and executing many Windows privilege attacks to escalate privileges on Windows systems. This tool offers modules and techniques to abuse vulnerable services and other escalation opportunities on the target.
PEASS - Privilege Escalation Awesome Scripts SUITE
PEASS is a tool capable of finding privilege escalation opportunities for Windows and Linux/Unix* and MacOS operating systems. The tool prints the results with nice colors, so it’s easy to recognize the misconfiguration easily.
Lateral movement
In this phase, it’s time to move internally over the network to find the most valuable assets and access other networks depending on the initial scope.
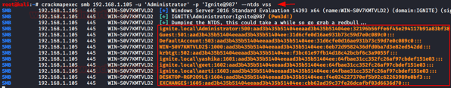
CrackMapExec
CrackMapExec is “the swiss army knife for pentesting networks.” It is a “machine-gun” that evaluates and exploits vulnerabilities in an active directory environment. Leveraging Mimikatz to obtain credentials, it moves laterally through the active directory.
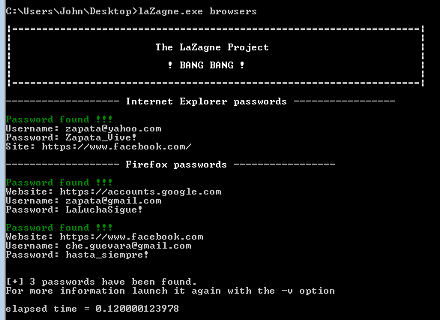
LaZagne
The LaZagne project is a password recovery tool capable of extracting passwords from everywhere. With these secrets, a red teaming professional can move laterally, accessing another system available on the network.
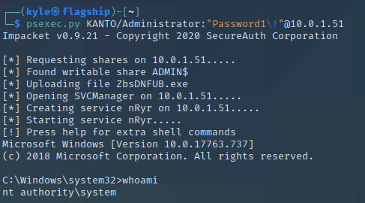
Impacket is a collection of Python classes for working with network protocols. Impacket is focused on providing low-level programmatic access to the packets and has a lot of standalone scripts for various escalation and access scenarios.
Command and control
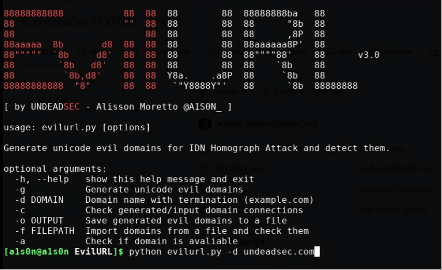
EvilURL
EvilURL is a script capable of generating unicode domains for IDN Homograph Attack and detecting them.
CobaltStrike
Cobalt Strike is a powerful suite for post-exploitation and to emulate a long-term actor via malleable C2 to evade detection.
Metasploit
Metasploit Framework is a tool that provides information about security vulnerabilities and is used to exploit vulnerabilities and escalate privileges in a target machine. This tool can generate a lot of customized payloads, control victims (bots) via its C2 server and many other features.
Exfiltrate and complete
The final step of a real-life cyberattack and red team assessment is to gain access and then exfiltrate the obtained data with sensitive secrets from the target network/host.
Become a Certified Ethical Hacker, guaranteed!
Get training from anywhere to earn your Certified Ethical Hacker (CEH) Certification — backed with an Exam Pass Guarantee.
DNSExfiltrator
DNSExfiltrator allows for transferring (exfiltrate) a file over a DNS request covert channel. This data leak testing tool allows exfiltrating data over a covert channel.
Red teaming tools
This article presented the essential list of tools and phases of a red teaming assessment. Although an extensive list was not delivered, we can now identify activities and techniques for each part of the process and use them to our benefit.
With this in mind, it’s important to reinforce that a red teaming assessment and following the process in detail can expose the vulnerabilities of the target systems that we are not aware of and help fix them.
Sources:
- Red teaming, Varonis
- Red teaming toolkit, 0x1 gitlab
- Red teaming tools, SecurityTrails