How to Identify and Detect a Phishing Email – 10 Tips
Better than the average phsishing attempt by Rick Turoczy via Flickr. Licensed under CC BY 2.0
See Infosec IQ in action
A perennial favorite with cybercriminals because it is practically a dead certainty and a cheap and easy con, email phishing scams (91% of cyberattacks start with a phishing email) are evolving with the times. That’s one reason users punch drunk with attacks from fraudsters continue to get duped. According to Return Path, 97% of people around the globe cannot identify a sophisticated phishing email.
Some of the latest scams in the news highlight the red flags that can indicate a malicious email:
- Block.one (May 2018) – Released a statement to warn users and the EOSIO community that members of its community had received “a phishing email on May 27 that included a link to a scam website claiming to be able to register EOS Tokens ahead of the end of the EOS Token distribution. Some of these emails came directly from the Block.one Zendesk support system.” Block.one said it was investigating how the sender of the phishing email was able to mimic or utilize actual Block.one email addresses, making the email appear authentic and fooling even experienced computer users. Always check the URL in the location bar before you log into a website.
- IRS (May 2018) – The IRS warned tax practitioners not to fall for a phishing scheme involving emails from scammers posing as state accounting and professional associations and trying to get users to disclose their user names and passwords. A clue to the email being a scam could have been the odd wording: “This announcement has been updated for your kind information through our secure information sharing portal which is linked to your email server.” Be suspicious of bad grammar and spelling.
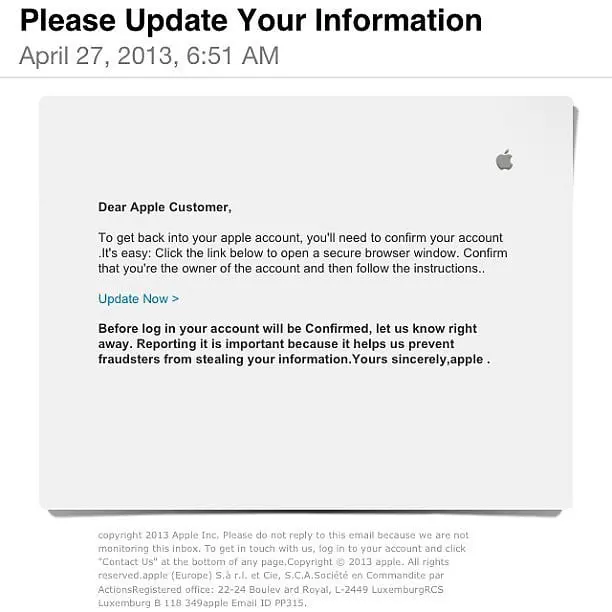
- GDPR (May 2018) – New EU data laws have attracted a rush of new email phishing scams. In the UK, customers of NatWest bank were among those targeted by phishing fraudsters who sent fraudulent emails claiming to be from the bank. The phishing emails warned customers their accounts could be terminated if they did not update their records, at which point they were directed to a site that stole their credentials. Be wary of emails that create a sense of urgency or invoke strong emotion, like fear or anxiety, even when it comes from an apparently authoritative source.
10 tips to avoid becoming a phishing email victim
- False credentials: Do not trust the name displayed as the email address of an organization. Look out for a sender's email address that is similar to, but not the same as, a company's official email address. An email address such as “important@yahoo.com” is not an official Yahoo contact email. Instead, go directly to a company’s website and conduct your business there, rather than replying to a dubious sender or clicking on links in an email.
- Malicious links: Never click on a link without first hovering over it to ascertain where exactly it is going. You can also right-click the link and select “Copy Hyperlink” from the context menu. Paste this into Notepad to see the real URL. Phishers use misleading domain names that to the untrained eye look, at first glance, genuine, e.g. genuinecompany.com.xyz.com. In this case, “genuinecompany” is a child domain and not the domain of a genuine company; xyz is the “real”, malicious domain. These URLs redirect you a phisher’s website that may look exactly like a site you know well. But, when you try to log in, the hackers steal your login details. Link manipulation techniques include:
- Misspelled URLs (e.g. bankofamerican.net)
- Typosquatting (www.trustedbank.com instead of trusted-bank.com
- IDN spoofing where characters are replaced with characters that look similar but are not the same, e.g. letters from the Cyrillic alphabet, and mean something different to a computer.
- Bad grammar and spelling: Emails from legitimate companies do not usually have spelling or grammar mistakes.
- Adding a personal touch: A red flag should go up when an email is addressed to a generic person, e.g. “Dear valuable client” or “Hello”. However, if a hacker already has your personal details – perhaps previously breached data sold on the Dark Web – they may address you personally. According to a Wombat Security report, emails personalized with a first name had click rates 19% higher than those with no personalization.
- Legitimate business practices: Legitimate businesses will never ask you for confidential information or credentials via email. That includes your password and social security number.
- Sense of urgency: Be cautious if an email sounds threatening or warns you to take immediate action otherwise your account will be closed, you will lose certain privileges, or your account will be compromised. This social engineering scam is even more popular than the “You have won a million” scam. The Wombat Security report mentioned above indicated that an urgent email password change request had a 28% average click rate.
- Threat of authority: Always check the sender’s contact details and Google them to check if they are a legitimate business. Phishers like to use law enforcement and government agencies to scare users who are often so intimidated they react instinctively to do what they are asked.
- Reliance on coincidence: Never click on attachments you are not expecting. If you think a company may have sent you an attachment because you are a customer, first make sure the sender is indeed the legitimate company of which you are a customer.
- Appeal to greed: If it seems too good to be true, it probably is. Most companies do not go around handing out fistfuls of dollars to anyone who clicks on a link. If you are asked for money in an email, it is probably a phishing scam. The most common ones come from princes and princesses in far off lands who are apparently sitting on a small fortune they wish to share with you, but only if you send them enough money for them to fly to a neutral country where the loot is stashed.
- It is a confirmed phish: If in any doubt, Google “scam” + some details of the email, e.g. “scam IRS urgent warning tax details out of date.” Often you will find that other users have already reported the phishing email as bogus. Remember, you cannot win a competition you did not enter; you cannot be locked out of an account you do not have; and rich foreigners are unlikely to pick you, Jo Ordinary, to manage their billions.
Where to next?
Phishers stop at nothing and their cunning is often ingenious. Ironically, as Lawrence Abrams of Bleeping Computer learned, there is no honor amongst thieves. Abrams was astonished to read in a phishing email he unearthed in his Spam folder a list of names associated with other phishing scams. In the email, the phisher warned the recipient, in this case Abrams, to avoid the listed people, clearly wishing to keep him as a client to themselves.
Phishing simulations & training
Users at all levels of an organization must learn how to recognize phishing emails and the cunning social engineering exploits phishers employ; even experts are sometimes fooled. Infosec Institute can help with its special learning modules in its AwareED and Security IQ learning portals.