How to scan email headers for phishing and malicious content
Phishing emails are one of the most common attack vectors used by cybercriminals. They can be used to deliver a malicious payload or steal user credentials from their target.
Spearphishing emails are designed to be more specifically targeted and more believable to their intended victims. By crafting a pretext that is extremely personal to their target, a phisher increases their probability of success. Spearphishing attacks can be extremely effective, and 65% of cybercrime groups use them as their primary infection vector when attacking an organization.
See Infosec IQ in action
However, a phishing email needs to be plausible to be believable. If the email looks phony, then no one will click the malicious link or download and open the attachment.
Part of making a phishing email is creating the right tone for the pretext. When masquerading as a well-known institution, like PayPal or Apple, it is important to get the tone of voice and stylistic details correct.
The other part of a successful spearphishing attack is making the email look like it came from a trusted person. This is where spoofed email headers come in.
Inside email headers
When you look at an email in Outlook, Gmail, or the email client of your choice, you probably only see a fraction of the data that the email contains. [CLICK IMAGES TO ENLARGE]
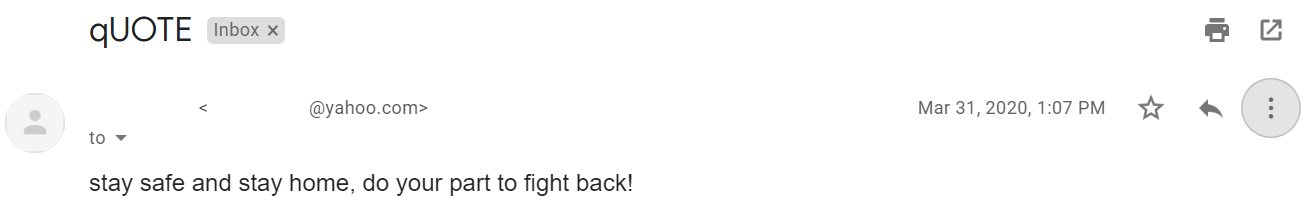
In Gmail, most emails look similar to the screenshot shown above. It contains the subject line, date, sending address and message body.
By clicking on the down arrow next to the word “to,” you can see additional details about how the message was sent.
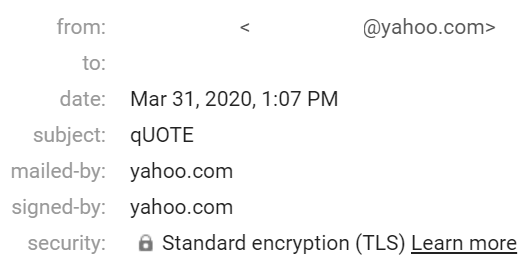
Looking at this, the lack of an email address in the to: field is suspicious, since it probably indicates a mass-mailer. However, this is not all of the information available. In Gmail, clicking the More menu (three dots) and selecting “Show Original” opens the source of the email.
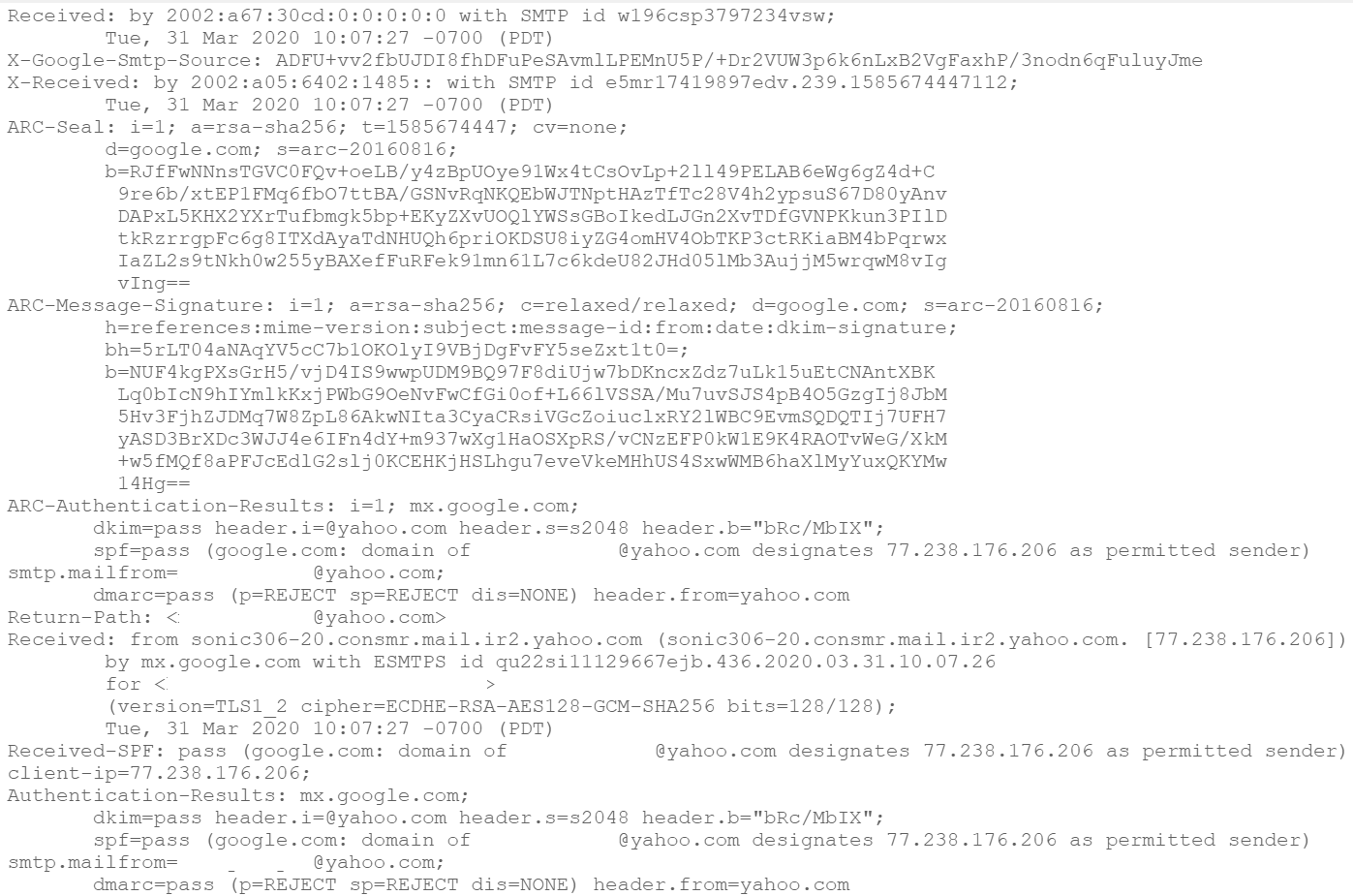
The screenshot above is a subset of the headers for this email. It includes information about the route taken by the email to reach its destination and the results of authentication testing. Examination of these headers can help to detect phishing emails.
Indicators of potentially malicious content in email headers
Email headers provide a great deal of information that can be used in identifying potential phishing emails. Some of these are easy to read and interpret, like the sections saying that DKIM and SPF verification passed in the screenshot above.
Other headers require some understanding of their purpose to be useful in analysis. Three potential signs of a phishing email are mismatches in the sender’s address, a suspicious path between sender and recipient and the use of an unusual email client.
Mismatched sender addresses
A common part of cybersecurity awareness and anti-phishing training is teaching employees to check the sender’s address before trusting an email. However, the display name in an email is easily faked, and over 90% of phishing emails spoof their display name.
Comparing the various email headers associated with the sender’s address can be helpful in identifying this technique. However, not all emails with spoofed display names are malicious.
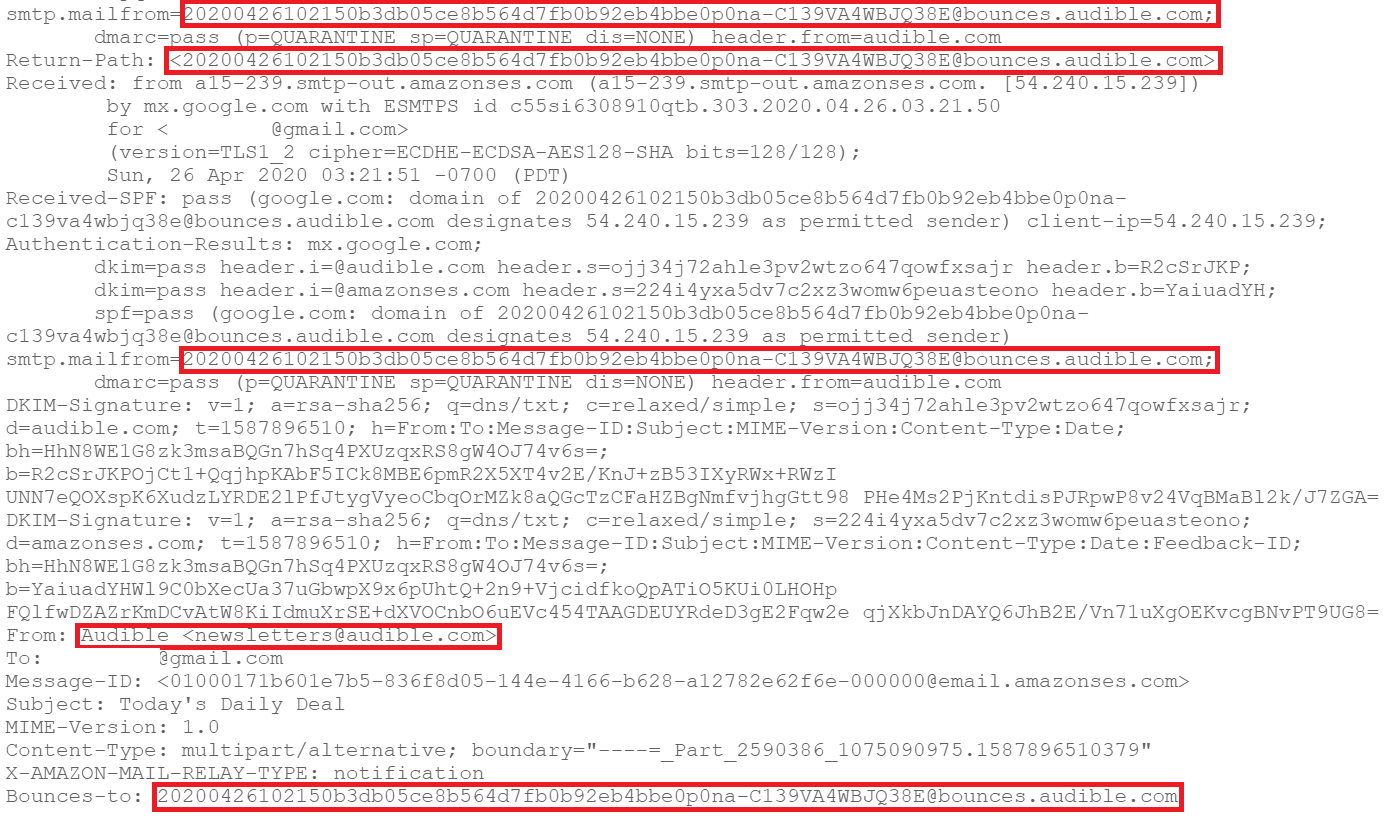
The screenshot above is from a mailer from Audible, Amazon’s audiobook company, listing the day’s daily audiobook deal. A number of different header values in this email should display the sender address, including:
- smtp.mailfrom
- Return-Path
- From:
- Reply-to/Bounces-to
Looking at the screenshot above, all of the headers are the same except for the From: one, which is what would be displayed to the email’s recipient. Comparing these headers for inconsistencies can help to identify phishing emails; however, as shown above, not all emails spoofing their display name are malicious.
Email travel path
Between the sender and the destination, an email moves through multiple email servers. The number of servers depends on the email, but it should always have at least two: the sending and receiving server.
A record of these email servers is stored in the email headers, as shown in the screenshot above. This email originated from a yahoo.com address, so it makes sense that its sending server would be a yahoo.com server.
Examining these email servers can help to identify inconsistencies regarding an email’s supposed origins. For example, an email claiming to originate from the United States may have an initial server in China or the UK, which would be suspicious.
When examining these headers, it is also important to keep in mind that they are not entirely trustworthy. At each stage of the journey, an email server has the ability to modify email headers. If DKIM and SPF are enabled, this should result in a failed verification.
However, the original sender of the email may have included spoofed headers to try to hide that they are the original sender of the message (instead of just a waypoint). The only Received: headers that can be trusted are the ones generated by trusted internal infrastructure.
Email client
When sending an email, most people do not connect directly to the email server and type in an email in the command line. Instead, they use an email client, like Outlook or Gmail.
The mail client used by an email’s sender is included in an email’s headers. If this header looks unusual in any way, it could be a reason for suspicion. However, as with other email headers, this header can be spoofed by the email’s sender.
Conclusion: Header-based detection of malicious emails
Email headers provide a great deal of information about the sender of a particular email and the path that it took between the sender and its destination. This information can be used to identify potential inconsistencies that point to malicious content or phishing attacks.
When configuring an internal email server, setting up SPF, DKIM and DMARC can help to protect against someone spoofing your domain. For protecting against spoofing attacks, many email providers can be configured to mark emails originating from external addresses as untrusted or to flag emails with mismatched From, Reply-to and Mailed-From headers.

Get six free posters
Reinforce cybersecurity best practices with six eye-catching posters found in our free poster kit from our award-winning series, Work Bytes.
Sources
- Phishing - Email Header Analysis, mlhale.github.io
- Internet Security Threat Report, Symantec
- Email Fraud Continues to Rise as the Number of Attacks Grew 36% in Q2, Proofpoint
- Reviewing X Sender Headers: How to Prevent Email Spoofing From Fake Senders, AT&T Business