Lockphish phishing attack: Capturing android PINs & iPhone passcodes over https
Phishing attacks are a common tactic for gaining initial access to a system. If an attacker can convince their target to hand over their login credentials or install and execute malware on their machine, this provides an attacker with a foothold that can be used to expand their access and achieve their operational objectives.
The Lockphish toolkit is a bit different from many phishing toolkits because it specifically targets Android PINs and iPhone passcodes. If the attacker can convince the target to visit a malicious webpage, they’ll be presented with a screen that looks like their device’s lock screen. Entering a PIN or passcode into this screen will send the login information to the attacker.

Strengthen security awareness with human risk management
Infosec HRM, powered by Right-Hand Cybersecurity, provides alert-based training nudges to minimize human risk at your organization.
In this article, we’ll walk through the process of compromising a user’s mobile device credentials using Lockphish. This includes everything from initial installation through actually compromising credentials for a target device.
Installing Lockphish
The Lockphish toolkit is available for download from GitHub here. You can either visit the site and download it directly or pull a copy using Git with the following command:
git clone https://github.com/kali-linux-tutorial/lockphish.
Lockphish is written in PHP and requires it to be installed on the system to run. If you don’t already have PHP installed on your system, install it with apt-get install php. Lockphish also requires unzip to be installed (apt-get install unzip).
After the dependencies are installed, use cd to move to the directory where you have installed Lockphish. Inside this directory, set the Lockphish script to be runnable with the command sudo chmod +x lockphish.sh.
Generating a phishing page with Lockphish
After completing the installation of Lockphish, run it with ./lockphish. You should be greeted with the following screen.
For this walkthrough, we’ll use the default redirection URL of YouTube, but this can be set to any site on the web. To use the default, just press Enter, which produces the following screen.
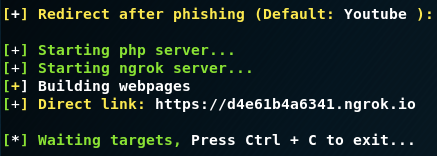
In this screen, Lockphish sets up its phishing server and generates a unique URL to use in the phishing attack. In this case, the URL is https://d4e61b4a6341.ngrok.io. This link needs to be delivered to the target in a way that encourages them to click on it (some form of phishing message).
Compromising a target device
Assuming that the link has been delivered successfully, we can see the impact of Lockphish on the target device. The image below shows what the target will be presented with once they open the Lockphish URL.
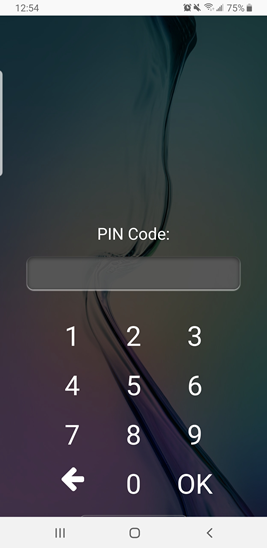
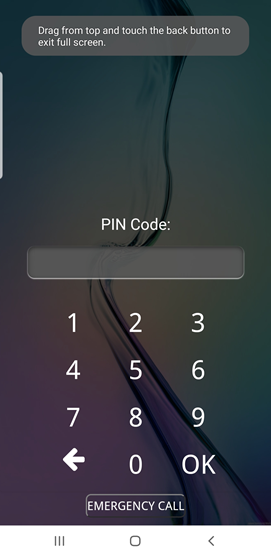
The screen above shows a redirect page. Clicking on the link to YouTube presents a screen like the following.
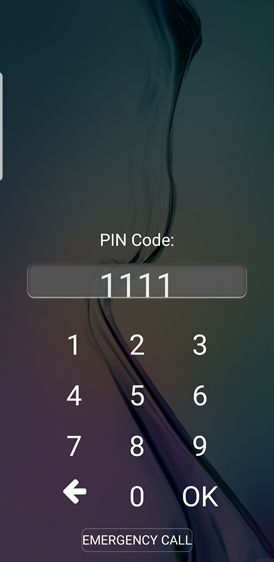
The screen above is intended to look like an Android lock screen. The attacker’s intention is that the user will enter their PIN number and click enter. If so, the PIN will be provided to the attacker, as shown below.
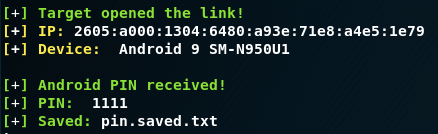
The screen above shows the Lockphish terminal. The PIN number entered by the user (1111) is shown and saved to a text file.
The pros and cons of Lockphish
Lockphish is an extremely versatile tool for collecting a target’s device login credentials. It supports Android, iOS and Windows devices. Additionally, it is very easy for the attacker to use, setting up its own phishing servers (using ngrok) and automatically storing device credentials in a file for future use.
That said, Lockphish is far from a perfect tool for phishing login credentials. Some limitations of Lockphish are:
- Odd landing page: The landing page for the phishing email requires a click on a redirect link on an otherwise blank page
- Click then lock: The user needs to take action on a webpage and then is immediately presented with a lock screen, presumably from a device timeout
- Static background image: The lock screen background image is static, making it unlikely that it actually looks like the user’s lock screen
- No PIN checking: Lockphish does not perform any verification of the user’s PIN number (the PIN on the device from the screenshots above isn’t actually 1111)
- Full-screen warning: Browsers on Android warn that they have entered full screen mode (as shown below)
- Inconsistent browser support: While Lockphish looks reasonably realistic on Chrome, it fails to mask password input on Firefox for Android (as shown below), which may cause suspicion
While all of these are limitations of Lockphish, it does not mean that it cannot be successful in a phishing attack. As past email scams have demonstrated, people will believe almost anything that comes with a good pretext.
Phishing simulations & training
Sources
- lockphish, GitHub
- LockPhish -- Phishing Attack on Lock Screen, KaliLinux.in