Phishing Attacks in the Education Industry
Reading, writing, and… ransomware? The education industry (which includes public and private schools from kindergarten to universities) is increasingly under attack from cybercriminals. This includes not only identity theft or money transfer fraud, but also ransomware—the holding hostage of computers or networks for a fee.
According to a report by security analysts Bitsight, 13% of educational institutions they examined had been affected by ransomware in 2016. While ransomware attacks on healthcare institutions made headlines in 2016 (most notoriously Hollywood Presbyterian Medical Center paid $17,000), overall the sector had comparatively fewer attacks at 3.5%.
See Infosec IQ in action
Why Target Education?
Educational institutions are often known for their diversity, inclusiveness, and openness. For learning, these ideas are paramount; however, when it comes to security, these concepts make a school especially vulnerable because of insecure networks, outdated equipment, and a lack of established protocols. Students are often allowed full access using their own devices, which may contain insecure or malicious apps.
Education networks not only store the data of all their teachers and staff, but also of their students. This information can be used for financial crimes or sold on the black market. In addition, higher education networks may have cutting-edge research in their files that could be targets for blackmail (ransomware) or theft by hostile states.
While many colleges and universities have stepped up their security efforts, smaller schools with younger students also make tempting targets. This is because they usually have very little money set aside for security, relying mostly on antivirus software or spam filters.
Also, those working in the education sector, ironically, seem to be less educated about phishing. A 2016 security survey found that those working in education were twice as likely (30% vs 15%) to fall for a phishing email that looked like a corporate communication.
This means hackers can breach the firewalls of an educational institute much easier than, say, a bank or government entity yet still reap similar rewards in terms of information or money. School districts often have data on thousands of employees as well as tens of thousands of students, all with lucrative identity information that can be used or sold on the black market.
Criminal networks seem to have discovered the inherent vulnerability of the education industry, as the frequency and intensity of attacks appear to be increasing.
How Is the Education Industry Targeted?
As with most industries, the main tool in phishing is email. A recent wave of attacks specifically targeted education: Thieves send an email request posing as a principal or other official asking for W-2 records to be forwarded to them.
In many cases, an unsuspecting administrator or assistant not familiar with phishing techniques has forwarded the information. In 2016, a school district in Olympia, Washington gave up the W-2 forms for more than 2,100 employees. This type of attack can lead to fraudulent tax return filing or identity theft and has been repeated all over the country.
In 2017, an email sent to employees of the Denver Public School System asking employees to change their user/password was convincing enough that at least 30 people clicked on the link. This resulted in thieves being able to change direct deposit information and make off with $40,000.
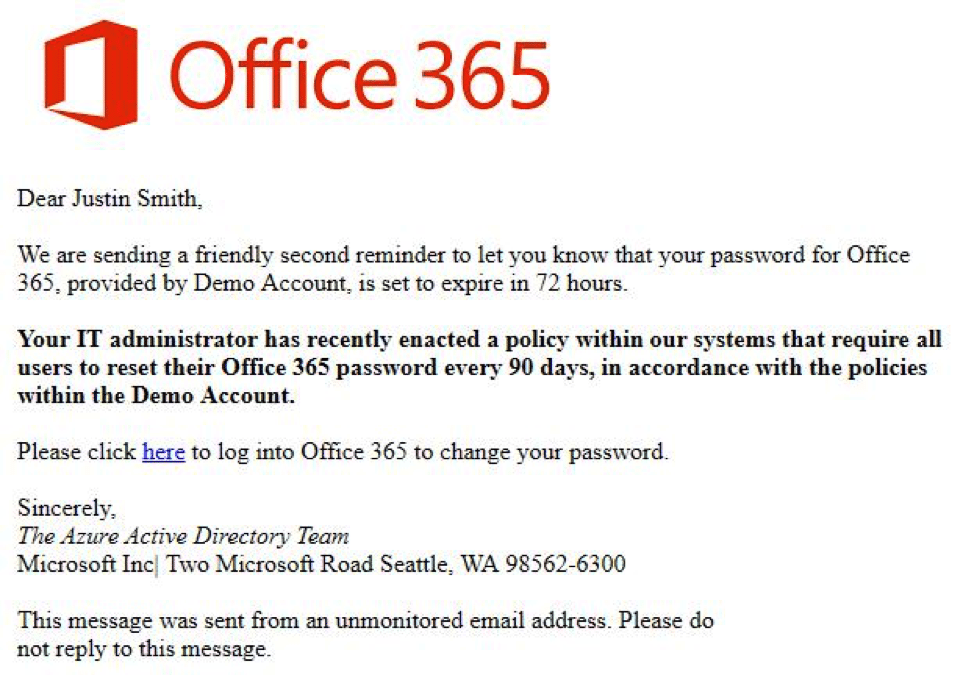
An example of PhishSim’s realistic, but completely safe, phishing templates available to users
Fraudsters are also continuing to get more sophisticated with their scams. An attack using Gmail accounts was discovered that primarily targeted educational institutions and journalists. An email that seemed come from a trusted Gmail contact appeared in user inboxes and it contained what purported to be a link to a Google Doc; users were then taken to a page where they were told to re-enter their usernames/passwords, which were then stolen. Although the attack was caught within an hour, roughly one million users were affected.
Then there are ransomware attacks, which lock users out of systems or files until a fee is paid. As mentioned earlier, these attacks gained notoriety when a group extorted $15,000 from Hollywood Presbyterian Medical Center. Because of the life-or-death nature of restoring access, healthcare has been seen as a lucrative target with an especially cruel twist.
However, ransomware attacks are more prevalent in education. In December 2016, Los Angeles Valley College’s servers and voicemails were encrypted in a ransomware attack. After discussing with authorities and third party security experts, they decided to pay the ransom of $28,000 (LAVC did not have backups of their data).
School districts all over the United States continue to reel from attacks, some paying ransomware (Brewer School District in Maine, $1,400) others refusing (Riverdale School District in New Jersey). All in all, the estimated take is at least a billion dollars.
Educate Your Educators
InfoSec Institute has developed a special program to help keep educational institutions safe from phishing attacks. It’s called SecurityIQ and consists of two intertwined components: training and real-world simulation.
The first component should be no stranger to anyone in education: it’s called AwareED and is a series of customizable courses about phishing and how to detect and prevent them from breaching your systems.
There are individual modules that contain informative videos as well as short quizzes. Topics include password safety as well as introductions to malware and phishing. You can also create your own courses and modules that integrate seamlessly with AwareED.
Employees (called “learners”) can be invited to enroll automatically by sending them an email. Once enrolled and in the course, administrators can monitor the progress of learners to make sure they complete it successfully and understand the importance of staying vigilant against hackers.
The other component is just as crucial: a real-world simulation of a phishing attack. This is called PhishSIM, short for phishing simulator. This allows you to choose from dozens of templates that represent typical phishing attacks (security alerts, social media messages, and even contest winner notices). These can be assembled in a group of attacks (called Batteries) and sent over a period of time (called Campaigns).
Any time a recipient clicks on one of these emails, they are diverted to an educational page that informs them of their mistake (you are also alerted on the dashboard). These educational pages are completely customizable, including adding your own images or school logo.
InfoSec Institute is constantly evolving SecurityIQ. We have recently added learning modules specific to management and to telecommuters. Our mission is to keep every type of institution protected and its employees informed. To date, we’ve won over 42 awards for our training platforms.
Don’t let your educational institution be compromised because someone accidentally clicked on a link that they shouldn’t have. Get everyone on the same page and up to speed about the dangers of phishing. Right now, InfoSec Institute is offering a free 30-day trial of SecurityIQ which allows unlimited campaigns for both AwareED and PhishSIM. Take advantage of this offer before someone takes advantage of you.
Sources
http://www.bbc.com/news/education-40288548
http://ptac.ed.gov/sites/default/files/W2%20Phishing%20Scam.pdf
https://www.nbcnews.com/tech/security/massive-phishing-attack-targets-millions-gmail-users-n754501
Phishing simulations & training
https://www.natlawreview.com/article/increasing-ransomware-attacks-higher-education