Phishing attacks in the banking industry
Not surprisingly, the banking industry is one of the top targets of hackers using phishing attacks to breach security. And, while safety protocols are built into both internal and consumer-facing banking websites and apps, it is often the human element that fails to detect the scam, resulting in thefts large and small.
For our purposes, the “banking industry” not only means traditional banks that offer checking and savings accounts, but also credit cards such as Visa and MasterCard as well as payment processing companies like PayPal and web e-tailers such as Amazon, Apple, or eBay. With the rise of Bitcoin and other so-called cryptocurrencies that are being used instead of traditional monies, e-wallets are also being targeted by thieves.

Strengthen security awareness with human risk management
Infosec HRM, powered by Right-Hand Cybersecurity, provides alert-based training nudges to minimize human risk at your organization.
Why target banking?
One word: money. Access to a bank account or to the internal network of a financial institution is akin to striking gold. Unlike the “old days,” where breaking into a bank involved digging tunnels and having a highly skilled team that included a safecracker, cyber-thieves can do much more damage remotely with very little skill and much less risk; now there are groups operating in the dark web that create malware or password-cracking apps and share or sell them to others.
Similarly, robbing people of their money used to involve using weapons and/or making threats; now, instead of hearing “this is a stickup,” you are more likely to receive an innocuous-looking email that asks you to “reset your password.”
In 2016, 1.09 million banking Trojan attacks were detected by Kaspersky Labs, a 30.6% increase over the previous year. They report that almost half (47.48%) of all phishing attacks involved redirecting users to a phony banking website or page created to steal credentials.
All it takes is one mistake and a user can quickly be cleaned out of money. And, while most credit card companies and banks have fraud detection services that can possibly help limit the damage, those that use Bitcoin are not so lucky. The irreversible, anonymous, decentralized nature of these transactions – part of their appeal as a universal currency – means that once the money is taken, it cannot be found or returned.
How is the banking industry targeted?
Financial institutions are attacked in methods both general and specific. Increasingly, sophisticated hacking groups are targeting the banks themselves instead of individual customers, thereby potentially receiving a greater windfall. In 2014, a group called Carbanak was able to access banking networks in Russia, reportedly stealing over a billion dollars; they were said to have instructed ATMs to disperse cash at specific times to awaiting associates.
In another instance, an unknown group created a banking trojan program called Dyreza, which, when installed on a user’s machine, appeared to give them a secure connection to their bank. In fact, the devious malware bypassed traditional SSL security and was able to send the secure information to their own servers; Dyreza was said to have been spread to 100,000 machines worldwide.
When it comes to a big financial scam, even more elaborate methods are implemented. This is sometimes referred to as “spear-phishing” or, if a C-level exec is targeted, whaling. In one recent whaling attack, Belgian bank Crelan lost €70 million ($75.8 million) when a hacker posed as the CEO and convinced someone in the finance department to wire the funds overseas.
What do all these attacks have in common? They all involved standard email communications that upon first glance seemed legitimate. They had official looking logos and email addresses or were personalized in some way. Yet, a trained employee could have easily spotted these emails as scams or at least questioned their authenticity and brought them to the attention of IT or other security professionals.
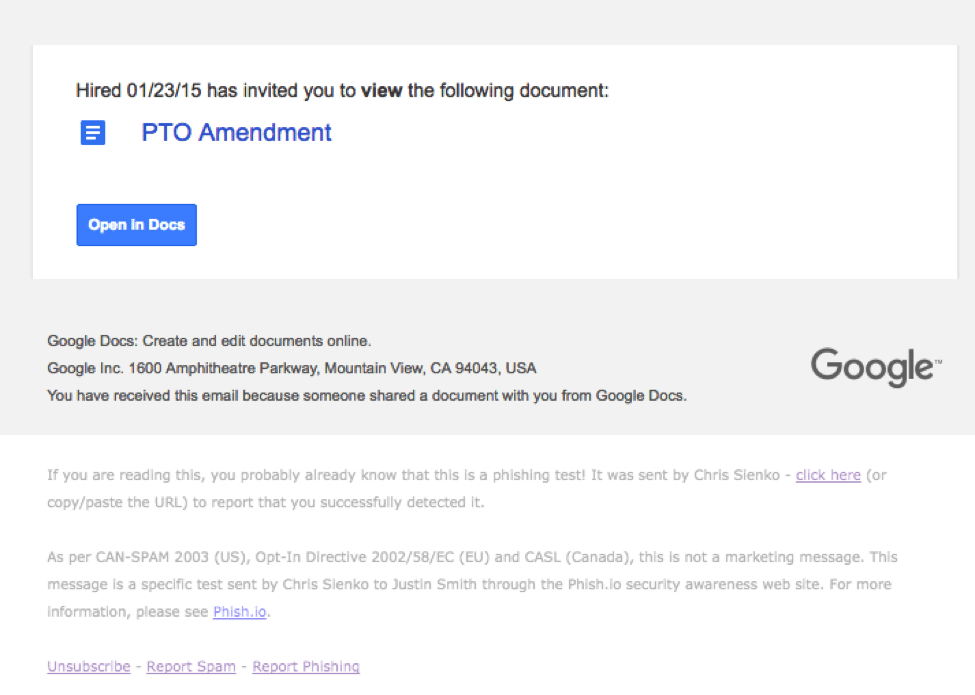
This realistic Google Docs invite might fool your CFO, but AwareEd modules can teach him to be more careful in future
It is estimated that over 90% of all successful hacking scams start with a phishing attack. IBM Threat Intelligence 2017 states that the number of phishing emails has quadrupled in just one year. There are approximately 15 billion spam/phishing emails sent per day, nearly half of which target or impersonate financial institutions. While many companies utilize spam filters that catch 99% of it, the more clever iterations are the most dangerous.
What you can do to increase security
The only practical, reasonable way to stop phishing is by training your entire team on the proper protocols. This can be implemented automatically by using Infosec’s Infosec IQ platform. Security IQ consists of two separate modules, AwareED and PhishSIM.
AwareED, as the name implies, focuses on awareness and education about phishing scams. It is a series of configurable learning modules that include videos and short tests. Individuals can be enrolled automatically and their progress monitored by the administrator.
There are courses designed for various departments including customer support, management, and new hires. They each contain modules that focus on essential topics such as password security and malware. In addition, you can create your own custom modules that easily integrate with the AwareED platform.
AwareED is a great way to get everyone on board with keeping your financial institution secure. Learners can be reminded to enroll and follow through on their tasks; those that fail or don’t participate can be required to take more intensive courses.
PhishSIM, again as the name implies, is a phishing simulator. This robust program lets you create and send a wide variety of phishing emails to workers. However, instead of containing a link to a phony banking website, unsuspecting users who click on the enclosed link will be redirected to a safe web page that informs them of their mistake (called an Education). You can choose from many different messages or create your own Education.
PhishSIM also comes with a variety of email templates you can use as bait. These include ones that look like corporate communications, personal messages, or security notices; you can also create your own phishing email.
PhishSIM allows you to send out a series of phishing emails (called Batteries) over a period of time (called a Campaign). You can use default Batteries or Campaigns and you can customize them. Any time a recipient clicks on an email, you are notified in the dashboard and can require them to take further training.
Infosec is constantly updating and upgrading Infosec IQ. There are now modules specifically for managers and developers as well as phishing campaigns for international companies.
Don’t wait until it’s too late. Sign up for a free 30-day trial of Infosec IQ and keep your employees vigilant about the never-ending threat of phishing attacks.
Check out more articles about phishing attacks:

Get six free posters
Reinforce cybersecurity best practices with six eye-catching posters found in our free poster kit from our award-winning series, Work Bytes.
Sources