Phishing techniques: Asking for sensitive information via email
Introduction
Email has been a critical part of our everyday communications since the 1990s. Thanks to its affordability and ease of use, email allows users to conduct business deals, stay in touch with their family and friends, and receive promotional materials from their favorite brands. However, the use of this messaging medium isn’t risk-free.
Phishers often use email while attempting to gain access to sensitive information. They’ll use fraudulent but legitimate-looking messages to convince users into supplying their email addresses, passwords, social security numbers, credit card information and more. The sensitive information can then be used to:

Two year's worth of NIST-aligned training
Deliver a comprehensive security awareness program using this series' 1- or 2-year program plans.
- Scam people in an email user’s business and personal network
- Purchase expensive resalable products and services with the individual’s credit card
- Misuse a victim’s identity by accessing their social networking profile
The truth is that no email user is safe from phishing attempts. The moving parts of email leave open windows for phishers to exploit, no matter how good your efforts to protect your information are.
Let’s take a look at email phishing in a bit more detail. We’ll look at what makes email people for it, what steps a phishing victim should take and some red flags associated with this type of phishing.
How do hackers collect sensitive information via email phishing?
It works like this: an attacker will send out thousands of fraudulent emails with the aim of collecting sensitive information. The emails often overwhelm the recipients by creating a sense of urgency or, ironically, loss of security. For instance, an email could threaten to freeze a recipient’s bank account if they do not re-supply their Social Security number. Pressurizing recipients causes them to be less diligent.
The sender could pretend to be someone from your bank or a site where you store your sensitive data, such as Dropbox. The phisher will put a lot of effort into designing templates that mimic real emails from spoofed businesses. Using the same logo, typeface, signature and language makes these emails look legitimate.
Attackers could also cite a user’s name, position, number and everything they can find to pretend as if they’ve spoken to the person in the past. Some even build up a rapport over several weeks or even months in cases where specific individuals are targeted for certain details which they would only share with the people they trust.
Despite widespread sources to make users aware of the risks of such attacks, data collection via email phishing is surprisingly successful. Based on industry research, 30 percent of phishing emails are opened by targeted recipients and 12 percent of those users check out the malicious link in the message (which typically redirects them to a webpage where they’re asked to enter their sensitive details). Because attackers usually send out thousands of emails at a given time, they can gather plenty of information even if only a small percentage of recipients share their sensitive information.
What makes people fall for it?
The problem is that people use emails as part of their crucial, everyday processes. Therefore, they are not so wary when someone pretending to be a trusted contact asks them for sensitive information.
Phishers play on the relationship, invoke a sense of fear and get in. Saying things like “Hey, it’s me again. I’m writing to inform you that your data is at risk of being deleted if you don’t update your date of birth” provokes a gut reaction, making users spontaneously hand over the information the phisher wants.
The reciprocity factor
Another reason why people fall for phishing emails that ask for sensitive information is reciprocity. Research reveals that people feel more obliged to do something for a person who does something for them. Phishers tend to piggyback on this indebtedness to elicit the sharing of information from their victim.
For instance, someone trying to save a user’s credit card from getting blocked could be regarded as someone doing them a favor. This, in turn, makes the user want to react in a positive way, which could be something as simple as supplying them with the details they’re after. Research published in the International Journal of Human-Computer Studies actually indicates that phishing emails relying on reciprocity and consistency delivered the best results in a case-based phishing study of 985 participants.
Overconfidence is a phisher’s best friend
Finally, phishers capitalize on the fact that employees are overconfident when it comes to their threat identification capabilities. Webroot’s survey of 4,000 working professionals found that 92 percent of employees claim to check for symptoms of phishing in email messages, but only 43 percent will verify that that email links redirect to their intended destinations. In addition, most personnel aren’t trained to identify phishing variations, and so often become a victim to emails asking for company-related credentials.
The reality is that if organizations aren’t investing in the right security training programs, their efforts to educate users about phishing are probably not going to work.
What should email users do when they realize they’ve been phished?
Users who find that they’ve provided sensitive information to someone with malicious intent can take the following steps to prevent harm to their data or the company they work for:
- File a report with the FTC: The Federal Trade Commission will inform users about the measures to take whether the sensitive data was related to their checking and savings, credit card account, or utilities. (Report an identity theft here)
- Create new passwords: Users should consider generating new passwords for the accounts and platforms that have been compromised as well as activating two-factor authentication
- Follow the organization’s policy: Users who’ve shared sensitive information about their company should follow the mitigation policy prescribed by their firm. Additionally, they should tell coworkers to watch out for similar emails to prevent the attack from spreading further
- Get in touch with the person, vendor or company that was spoofed: Whether it was the company CEO, a close friend or the cloud storage provider, the victim should let them know that someone is sending out emails with their name. It’s also a good idea to ask them for advice on what to do next
- Make a record: Capturing screenshots of the phishing message and noting down things like the content of the email, the sender’s address and so on is also a smart tactic. Users can then attach these materials as evidence when they report the attack to the Anti-Phishing Working Group
How can users train themselves to identify the red flags associated with this phishing technique?
With phishers becoming smarter and more brazen, it’s a good idea to learn about the red flags associated with email phishing. Below are some things that users should be paying attention to:
- Many recipients in the “To” field: Users should ensure the email is from a person they actually know. Even if it was sent by a familiar name, it’s crucial to examine the “To” line to see if they are the only recipient. Phishers typically send emails to as many people as possible. If the user is one of several recipients, and they don’t recognize others, they should be suspicious
- A random or misspelled domain name: When phishers set up a bogus email address, they often get the option to choose a display name, which can be almost anything. For instance, they can display a name like PayPal in an attempt to spoof a certain organization. However, they can’t replicate the official domain name that comes after @ in the email address. Phishing emails include random or misspelled domain names like “PayPal@termination-alert-684.com” or “customer service@paypall.com”
- Asking for confidential information: Users should keep in mind that no legitimate service provider or company asks for things like credit card number or account passwords via email. In case they’re redirected to a website where they’re asked to enter their information, they should Google the company or institute to find the official site instead of writing their details on the site they opened via email
- Urgent requests: If the sender is unexpectedly asking the user to provide sensitive information in a short frame of time, the user should be suspicious. Phishers intimidate or rush email users with the hope that they won’t spend a lot of time scrutinizing the email for malicious intent. It is, therefore, important to be aware, alert and thorough while going through the email
Real-world examples of email phishing
Here are a few emails that consist of some of the red flags mentioned above:
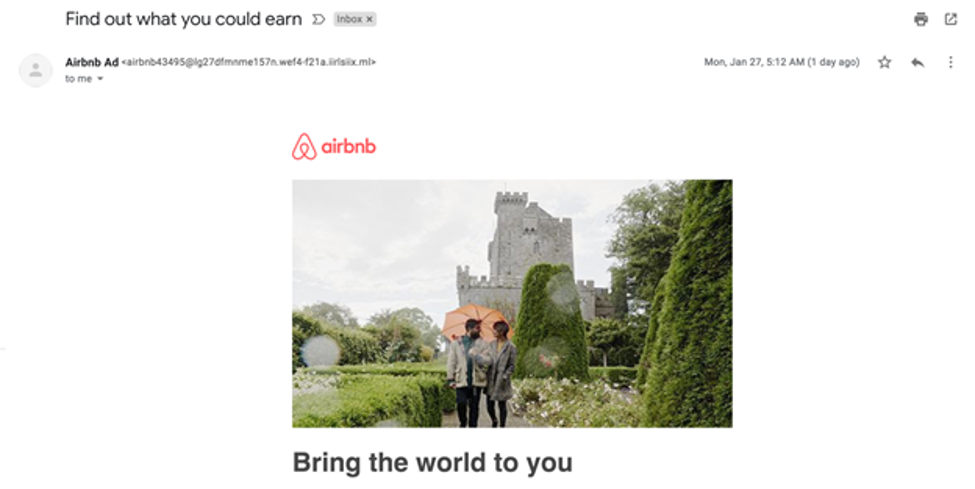
Email that spoofed Airbnb
This email looks like it was sent by Airbnb, but if the recipient takes a closer look at the domain name after @, it doesn’t look anything like Airbnb’s official email ID, i.e. Airbnb.com. Airbnb users who aren’t skilled at detecting phishing emails could easily fall for it and provide their account information to an adversary.
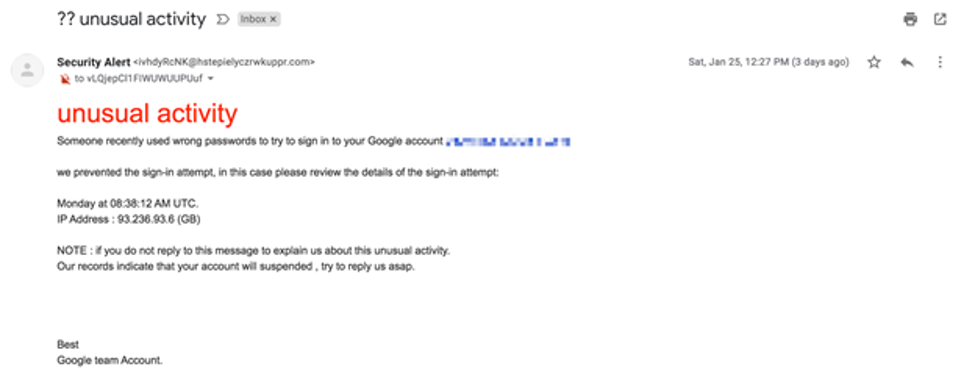
Email asking for an urgent response
In this example, the sender is asking the user to submit an explanation for unusual activity on their account on an urgent basis. If he or she doesn’t, the account will be suspended.
Novices might easily panic when reading such emails. However, the email address used by the sender and grammatical errors like the lowercase “W” indicates that this is a phishing email asking for sensitive information and should be marked as spam.
Conclusion
Here’s a fact: Most people learn best through experience. Hence, the most effective way to understand phishing methods that ask for sensitive information via email is to experience them yourself in a controlled environment.
See Infosec IQ in action
Sources
- The history of email, Nordic IT
- ‘You Have a New Dropbox Message’ Scam Emails, Hoax-Slayer
- 2019 Phishing Statistics and Email Fraud Statistics, Retruster
- Kathryn Parsons, Marcus Butavicius, Paul Delfabbro, Meredith Lillie, "Predicting susceptibility to social influence in phishing emails," International Journal of Human-Computer Studies, 2019
- Webroot Report: Nearly Half of Employees Confess to Clicking Links in Potential Phishing Emails at Work, PR Newswire