Spear-Phishing Case Study
Introduction
The power of information technology has been developing with speed unprecedented in human history. Research suggests that 90 percent of the whole world’s data has been generated from 2011 to 2013. According to this finding, it is reasonable to assume that the value of digital assets can considerably exceed that of physical assets. It is true that institutions depend increasingly on computer systems to store their data. Financial information, high technology design, and sensitive political documents are all kept in computer servers and networks. This new gold mine not only attracts organized cyber-criminal groups and delinquent juvenile hackers, but also nations. Governments in different countries participate actively in various cyberattack attempts such as industrial espionage, sabotage, and cyberwarfare. While nations can have their own law enforcement to deal with domestic network intrusions within their own territories, inter/trans-national state actors’ cyber-operations are complicated and difficult to investigate and pursue. There is not yet any effective and formal international agreement to regulate state behavior in cyberspace. Consequently, it is not uncommon to see state initiatives or involvement in distributed-denial-of-attack (DDoS), spear-phishing, computer virus development, etc. These state-funded endeavors in cyberspace are usually associated with the notion of advanced persistent threat (APT). APT groups specialize in continuous information security breach that allows them to reside on the victim’s network without authorization. This presence facilitates APTs intended operations, namely, stealing sensitive data, damaging the victim’s computer network or physical infrastructures, and spying on the victim’s activities.
APT1—People’s Liberation Army of China Unit 61398
The notion of APT has been introduced for a decade. Yet, it only came to public and media attention when a U.S. cybersecurity firm published an investigative report revealing the Chinese army’s cyber-espionage division, Unit 61398, in early 2013. The investigation unveiled a continuous worldwide data extraction and spying scheme initiated by the Chinese government between 2006 and 2013. This military division was named APT1 in the investigation report, implying the idea of the first identified APT group with clear national objectives throughout its missions. About 140 victim institutions have been identified. The victim list of APT1 ranged from government institutions to corporations in aeronautics, renewable energy, steel manufacture, information technology, etc., in English speaking countries all over the world. APT1 did not "invent" uncommon or novel techniques to compromise the victims’ computer networks. The group implemented primarily spear-phishing to gain initial access and eventually planted RAT and spyware to fulfill its objectives.
See Infosec IQ in action
The loss of intellectual property, digital assets, and classified information was particularly evident in the U.S. Over 80 percent of the victims were U.S.-based. (115 American institutions were recognized, according to the investigation.) As a matter of fact, most U.S. victims’ activities correspond to China’s political, economic, and industrial interests for the country’s development trajectory, which explains China’s motivations in carrying out the entire operation. Moreover, these figures also expose an alarming and uncomfortable truth about the U.S. victims’ information security level. If U.S. industry leaders in certain high-technology sectors that demand high-level secure computer systems to develop and store digital assets cannot resist first stage cyberattacks like phishing and consequently fall prey to a more complex cyber-operation trap, allowing the attacker to further his malicious attempts, how will the small and medium enterprises react and how much will they lose, given the same level of cyberattack?
While APT1 specialized in the Anglophone sphere, the investigation also indicated the existence of about 20 Chinese military units responsible for cyberspace operation around the globe. Therefore, it was suggested that APT1 could be only a glimpse, though a significant one, into the Chinese government’s national defense investment in cyberspace. APT1 is, besides its media reputation and activity scale, a vivid example showing the persistence, strategy and technical sophistication of carrying out a multiannual and international cyber-operation by a state actor. APT1 is a convincing scenario of a state’s willingness and determination to succeed and thrive in reality.
Attacking Techniques of APT1
It may be surprising, yet it is true that spear-phishing has played a crucial role in the success of APT1. U.S.-based corporations in high technology sectors such as U.S. Steel, Westinghouse, and SolarWorld, which are all listed as victims of APT1. APT1 is the schemer behind such an exhaustive, tireless and aggressive spear-phishing scheme. Gaining initial access to the victim’s system creates the first access point and lays the foundation for subsequent malware deployment. In order not to miss the shot, it requires well-crafted and socially engineered spear-phishing emails to target the victims’ personnel. The content of the spear-phishing-emails developed by APT1 was highly relevant to the recipients so as to seduce them to enter the trap. Moreover, these spear-phishing emails always contain disguised malware attachments that have common job-related fake file extensions, such as zip, jpeg, pdf, and doc, to lure victims to open them. Depending on the victim institutions’ background, APT1 created spear-phishing emails with themes regarding diplomacy, military, economic development, day-to-day workflow, etc., to phish the targets. As suggested, the state-funded APT1 has the resources and favorable conditions to test and persistently attack the victim institutions’ information security protection over a long period. One of the victims discovered APT1 after a period of more than four years. The personnel’s security awareness may not be able to catch up with the scenario improvement of spear-phishing emails and eventually fall victim to the scheme.
APT1 was able to establish a foothold following the initial system compromise and then uploaded various customized backdoors, depending on the victim’s security architecture and vulnerabilities. These tailor-made backdoors were mostly variants of remote access Trojan (RAT) that were hardly detectable by anti-virus software, as they were unlikely to be available in public. This step was to ensure APT1’s remote access to the victim’s computer system. APT1 was therefore capable of bypassing the victim’s firewall and conducting further cyberattacks within the victim’s network.
Spear-phishing permitted APT1 to take advantage to the fullest to expand its access laterally within the victim institution. The longer its malicious tools resided in the compromised network, the more digital assets APT1 could extract. All APT1 had to do was to repeat the same attack pattern: Conduct inter-departmental spear-phishing based on newly acquired information and plant more RATs to escalate its privileges to access wider and deeper the victim’s database. One of APT1’s victims lost 6.5 terabytes of digital assets in ten months.
Digital Assets Targeted by APT1
The vestige of China’s 12th five-year plan (2011-2015) was present throughout the victim list of APT1. Four of the seven most strategically important emerging industries in China were among the mostly targeted sectors on the victim list (information technology, renewable energy, new materials, and scientific development). APT1 was interested in many different sources of data, namely, international trade information in solar energy equipment, trade union activities, nuclear plant designs, aeronautic research findings, other scientific development projects, product parts, pricing, etc. These examples are of high value to both the victim and the beneficiary. The data theft often was intensified by the mismanagement of security priorities within the target institution. Nowadays, institutions, especially those with sensitive data and avant-garde technology, face not only traditional cyber-threats from non-state actors, but also state-funded APTs. In the example of APT1, it can be seen how devoted and devastating can it be when the attack initiative is supported by a state actor.
APT1 Significance
The high-profile media coverage of APT1 has attracted a great deal of international attention. CNN sent a team of reporters to China to approach the suspected headquarters of APT1 in Shanghai right after the publication. The two-minute video showed Chinese soldiers at the gate of the building trying to stop the reporters’ vehicle.
 Source: Youtube. https://www.youtube.com/watch?v=3d2gyydHwmY 12 Jun 2016
Source: Youtube. https://www.youtube.com/watch?v=3d2gyydHwmY 12 Jun 2016
More important, a year following the publication of the investigation's report, the U.S. Department of Justice issued an international indictment against five Chinese soldiers of APT1 for cybercrime acts ranging from spear-phishing and data theft to industrial espionage. APT1 is the first and only case of a state accusing another state of cyber-espionage in the world for now.
Source : FBI. https://www.fbi.gov/news/news_blog/five-chinese-military-hackers-charged-with-cyber-espionage-against-u.s 12 Jun 2016
APT1 is a recent, significant and appalling example revealing a new and very competent participant in cyberspace.
InfoSec PhishSim solution—Protect your institution against APTs
Very often, institutions underestimate the cybersecurity threat coming from their own employees. High-level management and decision-makers are considered to be exposed to more risks than entry to mid-level employees. Indeed, this assumption is not false, as high-ranking officers often have more privileges to access classified information. Nonetheless, to APTs, the difference is minimal between delivering a one-time spear-phishing email to one particular target and multiple evolving ones to multiple targets continuously. Many U.S.-based institutions are still not sufficiently informed about the risks originating from ubiquitous spear-phishing to complex APT attacks.
Certainly, establishing internal clearance and defining digital assets are both crucial to an institution’s cyber-defense policy. Yet security awareness training for personnel should be prioritized as the fundamental step. It is not a negligible procedure to improve the overall security of your institution. In the case of APT1, it is obvious how vulnerable the human factor is to attacks on the institution’s information security policy.
InfoSec Institute has a proven track record in providing effective cybersecurity solutions in the country. Since its establishment, hundreds of clients from diversified sectors ranging from governmental to corporate world have benefited from InfoSec Institute’s professional enrichment programs. InfoSec Institute delivers cybersecurity risk assessment, training, and other on-demand consulting services. Our emphasis is on training cybersecurity professional to deal with today’s fast-changing cyberspace threats has been widely recognized. You may visit the institute’s certification and security awareness programs here for more information.
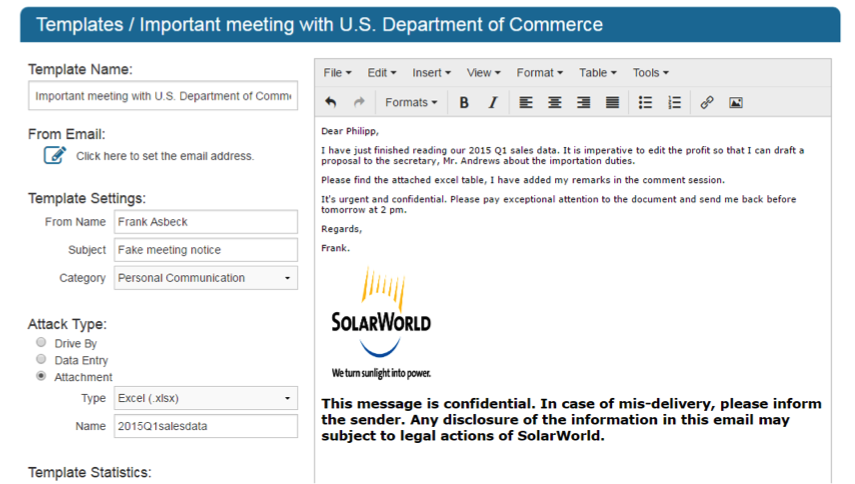
Tailor-made to identify APT-style spear-phishing, InfoSec Institute is proud to announce the new interactive phishing training platform, SecurityIQ. We believe the key to keep up with the evolving spear-phishing menace is to provide a service for both the trainers and trainees to communicate, share and test new phishing content and strategies. Users of SecurityIQ can manage and customize phishing training for specific personnel. The following image provides an example of an imagined APT1 phishing scenario and SecurityIQ’s user-friendly interface. You can start coming up your own phishing ideas, adding the bait and disguising your identity by setting up your free account here.
Very often, institutions underestimate the cybersecurity threat coming from their own employees. High-level management and decision-makers are considered to be exposed to more risks than entry to mid-level employees. Indeed, this assumption is not false, as high-ranking officers often have more privileges to access classified information. Nonetheless, to APTs, the difference is minimal between delivering a one-time spear-phishing email to one particular target and multiple evolving ones to multiple targets continuously. Many U.S.-based institutions are still not sufficiently informed about the risks originating from ubiquitous spear-phishing to complex APT attacks.
Certainly, establishing internal clearance and defining digital assets are both crucial to an institution’s cyber-defense policy. Yet security awareness training for personnel should be prioritized as the fundamental step. It is not a negligible procedure to improve the overall security of your institution. In the case of APT1, it is obvious how vulnerable the human factor is to attacks on the institution’s information security policy.
InfoSec Institute has a proven track record in providing effective cybersecurity solutions in the country. Since its establishment, hundreds of clients from diversified sectors ranging from governmental to corporate world have benefited from InfoSec Institute’s professional enrichment programs. InfoSec Institute delivers cybersecurity risk assessment, training, and other on-demand consulting services. Our emphasis is on training cybersecurity professional to deal with today’s fast-changing cyberspace threats has been widely recognized. You may visit the institute’s certification and security awareness programs here for more information.
See Infosec IQ in action
Tailor-made to identify APT-style spear-phishing, InfoSec Institute is proud to announce the new interactive phishing training platform, SecurityIQ. We believe the key to keep up with the evolving spear-phishing menace is to provide a service for both the trainers and trainees to communicate, share and test new phishing content and strategies. Users of SecurityIQ can manage and customize phishing training for specific personnel. The following image provides an example of an imagined APT1 phishing scenario and SecurityIQ’s user-friendly interface. You can start coming up your own phishing ideas, adding the bait and disguising your identity by setting up your free account here.