Tabnabbing
What is Tabnabbing?
As described by Aza Raskin, tabnabbing goes like this: when a simple JavaScript detects that the user has moved to another browser tab or has been inactive for some time, a URL in an open tab of the browser is changed to a phishing site
Tabnabbing is a kind of phishing. It's basically a computer exploit which entices the user to submit his login details and password to a known website by imitating those sites. The attack takes advantage of the trust of victim and and the ability of modern web pages to rewrite tabs and their contents for a long time after the page has been loaded.
Phishing simulations & training
Most of us who are webmasters, i.e. people who do website development stuff, know how Google indexing is done. Others might not have that information, though, so let me explain first.
How does any website results appear in Google search results? You've made the website, but how does Google know about it? Search engines use spider and crawler software over the web to index the new websites or latest changes in the existing websites in order to give users the best, latest results. The indexing of the website depends on a file which is at the root level of all web hosting websites. If it's not present, Google treats it as full index.
Most people think that the robots.txt file is used to tell Google to index your website, but actually the robots.txt file is used to tell Google what you want to index from your website and what you don't want indexed. The robot file allows full indexing, i.e. all files are indexed, even password and database files. Woo!
Now here comes the interesting part. Most of the hackers use free web hosting websites to run the phishing pages, and all free web hosting websites have default robot.txt files. This means that when the hacker uploads their phishing page, it's indexed by Google. And we all know what we use to extract smart information from Google? Of course, it's Google Dorks.
Google Dork to Extract a Phishing Page's Password File
Now we'll learn how to make our own dorks to extract a hacker's phishing page information.
What the hackers do is edit the redirects of the form of a login page and change the request mode from POST to GET in order to retrieve passwords in plain text, which they then store in text files. You can exploit that.
The Dork you can use to extract the password file:
inurl:"passes" OR inurl:"pass" OR inurl:"passwords" OR inurl:"credentials" -search -download -techsupt -git -games -gz -bypass -exe filetype:txt @yahoo.com OR @gmail OR @hotmail OR @rediff
Process of Tabnabbing
This is a small attack implemented on a LAN level. Follow the given steps:
-
Download and install ngrok, which is required for port forwarding.
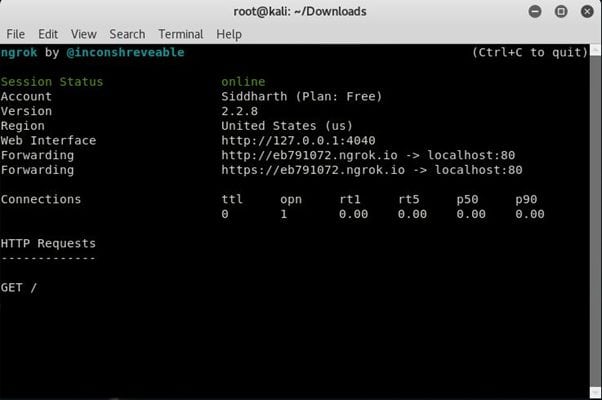
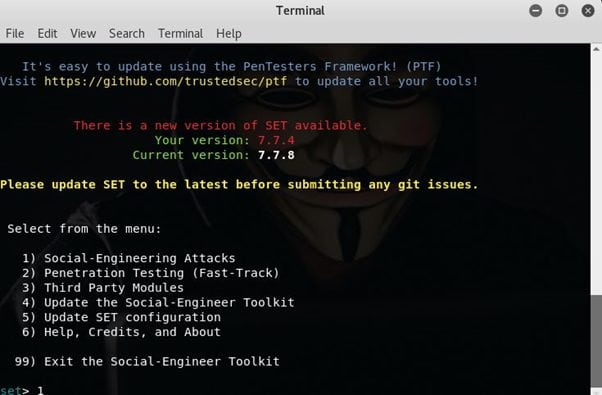
- Open the social engineering toolkit in your Kali Linux.
-
Select Social Engineering Attack first, then Website Attack Vectors. Then select option 4 or 3, and afterwards, Site Cloner.
- Copy the ngrok address as shown above.
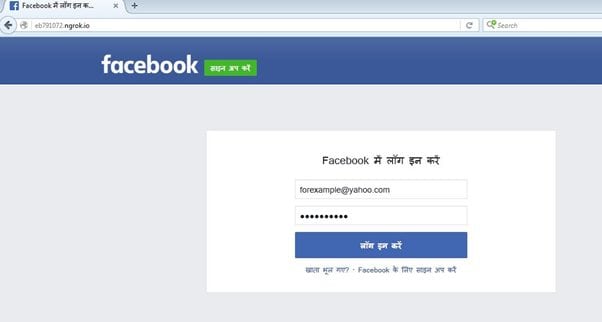
- Enter the URL to clone, in this case http://www.facebook.com.
-
If all was done right, open ngrok link on some other device on the same network. The Facebook login page will appear as shown below.

-
Once the user has entered their details (as shown below), all the information will appear in your terminal as shown above.
Real-Life Case Study of an Attack
The APT 28 group committed cyberattacks against government organizations' email accounts. The DNC hackers were suspected of targeting the French presidential candidate Emmanuel Macron.
The technique which was used by attackers was to swap the inactive open tabs with an illegitimate site. In this way, the attackers tricked victims into providing their credentials while thinking they were visiting a legitimate website.
The pawn Storm is using a variant of tabnabbing. In this type of attack, the target gets mail from a website in which he may be interested — maybe from a conference he is going to visit or a website he has subscribed to. The email has a link to a URL that looks legitimate. As soon as the target reads his email and clicks on the link, it will open in a new tab. This tab, when opened by the victim, will show the legal site of a conference or a provider after being redirected from a site which is under the attackers' control. The target will surely spend some time reading the info or browsing this legal site. Once distracted, he probably did not notice that just before the redirection, a simple script was run, changing the original email tab to a phishing site.
As the victim finishes reading the news article or any important information on the legal site, he returns to the tab of his email. He is informed that his session has expired and the site needs his username and password again. He will probably reenter his username and password, and that information is sent to the attackers.
Preventing Tabnabbing
Before you log into any website or provide sensitive data to any website, look at the address bar of the browser. Make sure that the URL is not illegal or fake, and the website uses proper digital certificates like SSL.
Do not allow scripts on a webpage if it is not trusted. Use plugins like NoScript, which can be effective in preventing tabnabbing. It will prevent JavaScript from running on an untrusted website.
Conclusion
Tabnabbing is purely a social engineering attack. It all depends on the victim's brain and the ability of the hacker to con the victim into believing in his malicious site. The site may ask you to give your account and password details and win a prize or fool you into believing that you are the lucky guy to win a big sum.

Get six free posters
Reinforce cybersecurity best practices with six eye-catching posters found in our free poster kit from our award-winning series, Work Bytes.
But no matter how hard the hacker may try, if the user is familiar with this kind of attack and knows how to differentiate a real website from a fake one he will never become a mark. Therefore, your security is ultimately in your own hands.








