[Updated] Top 9 coronavirus phishing scams making the rounds
Coronavirus phishing attacks just won’t go away. As the COVID-19 pandemic outbreak continues to spread, cybercriminals have intensified their phishing attacks, adding fuel to the global crisis.
Beyond the devastating effects of COVID-19, the outbreak is producing a perfect storm for cybercriminals. Cybercriminals are feeding on public anxiety and preying on victims using scare tactics and urgent calls to action to entice an ill-advised click. And to make matters worse, the global reach of COVID-19 means virtually everyone is a relevant target for a coronavirus scam.
See Infosec IQ in action
We collected nine coronavirus phishing attack examples to shed light on the top tactics cybercriminals are using so you can prepare your employees for the threats they are facing now and in the foreseeable future.
Is your organization susceptible to phishing attacks? Find out today with a free Phishing Risk Test!
1. Consumer relief package
As the economic fallout of the COVID-19 pandemic continues, attackers are leveraging consumer anticipation of tax relief and government-issued economic stimulus plans. These attacks trick victims into dropping their guard and clicking a malicious link.
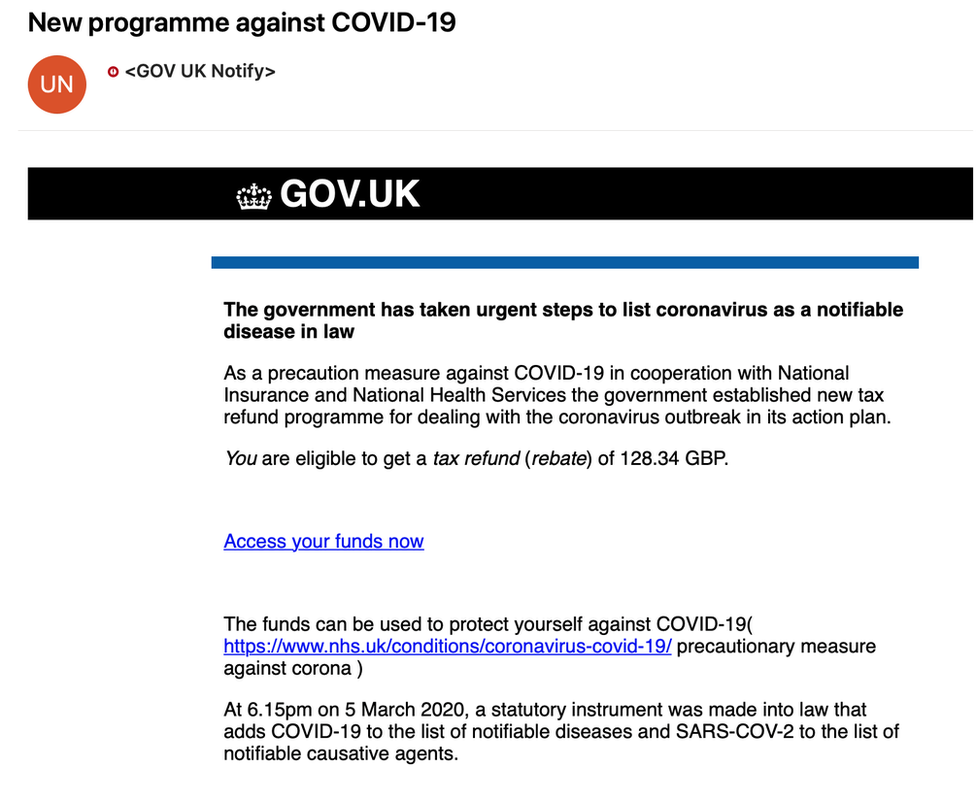
Image courtesy of Mimecast
Similar attacks have been spotted in the United States.

Use this phishing template in Infosec IQ
2. Help desk impersonation
At a time when technical support teams are helping employees transition to remote workstations, cybercriminals are impersonating IT help desks to take advantage of their increased visibility and communication.
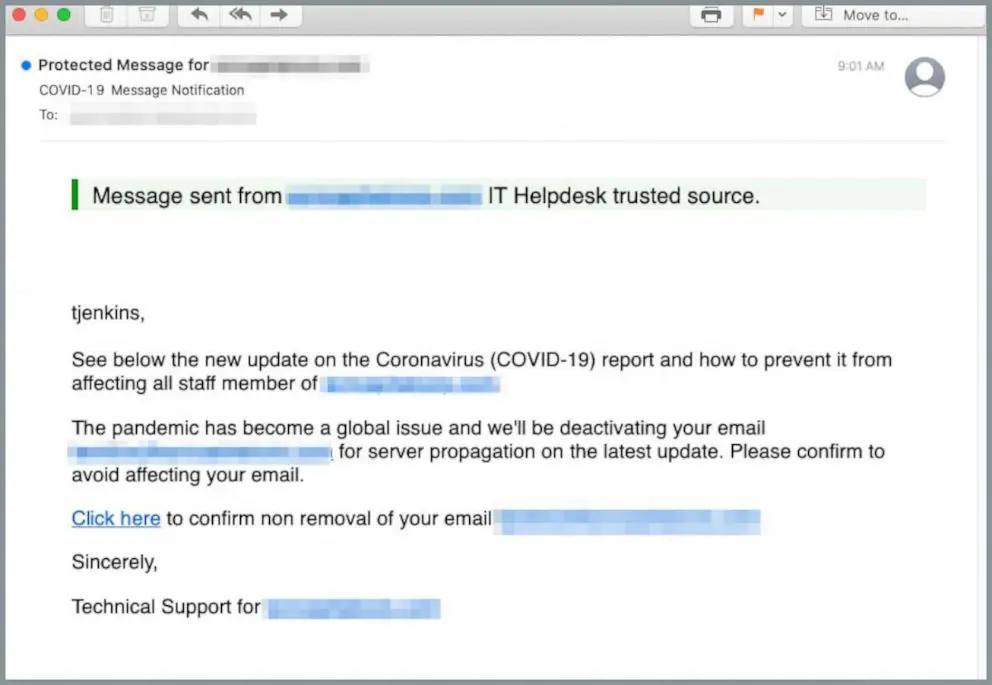
Image courtesy of INKY
Employees working remotely for the first time are likely in contact with IT and security teams more than ever before. Employees anticipation communication from your help desk may be more susceptible to clicking a malicious link in this type of attack.
3. Safety measures turned malicious
This phishing attack impersonates a coronavirus specialist from the World Health Organization to trick victims with two malicious options. The email urges the victim to download a malicious file disguised as a safety document.
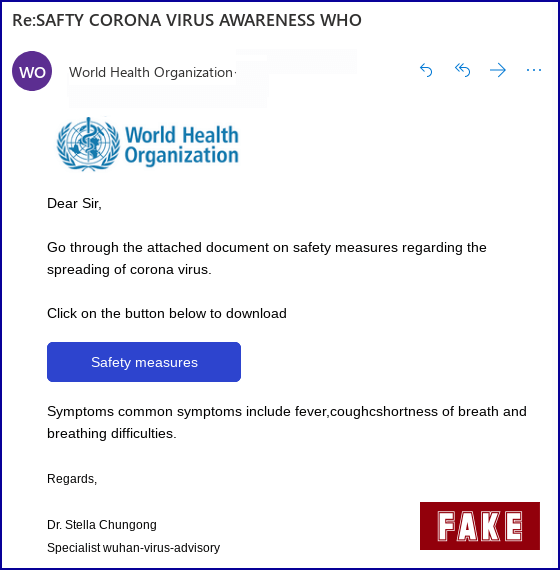
Image courtesy of Sophos
The same attack was spotted without the World Health Organization branding, but instead targeted to the victim’s region.
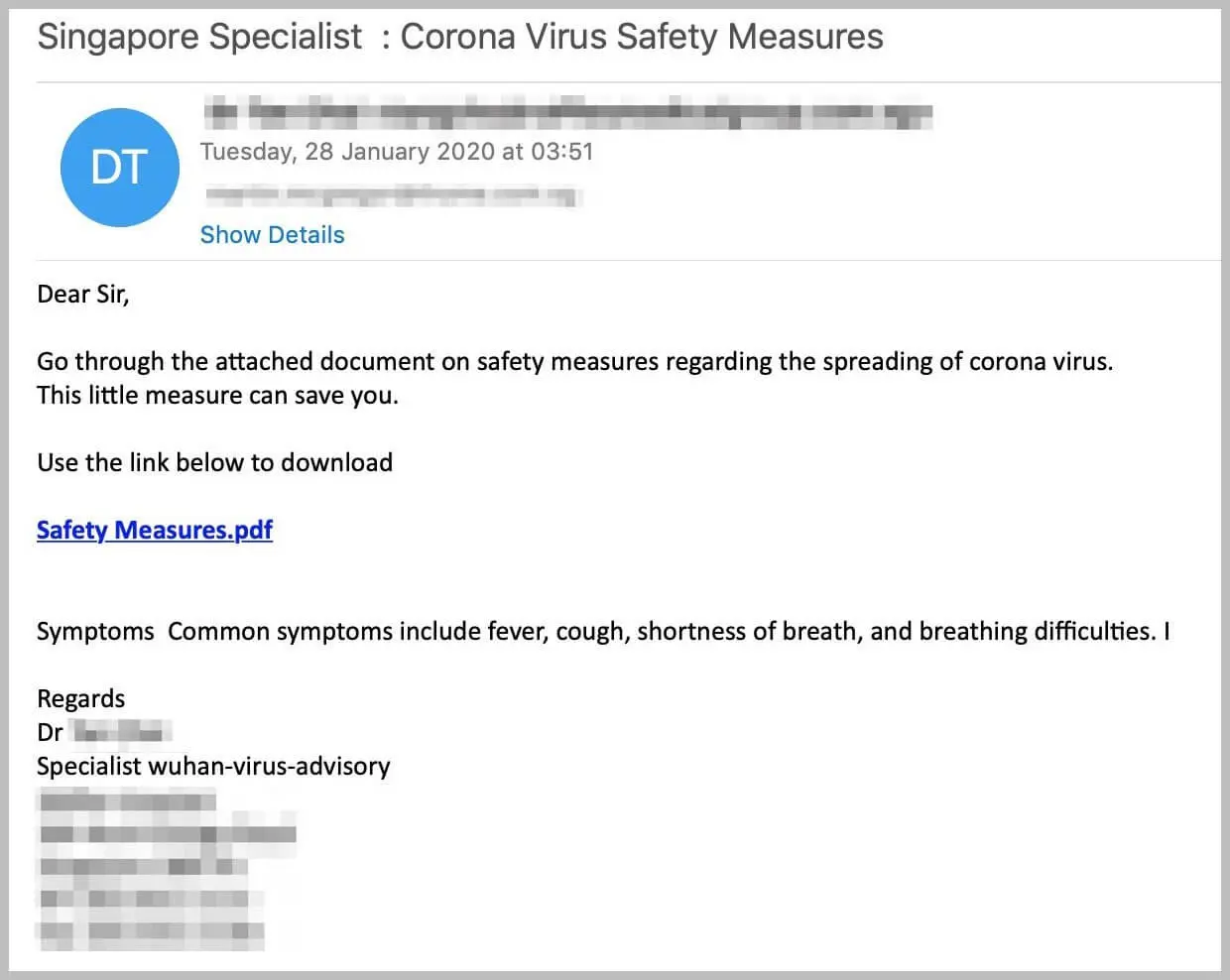
Image courtesy of Wired
The attack also gives the victim the option to click a "Safety Measures" button. If the victim clicks the link, they are redirected to a spoofed World Health Organization site and prompted to provide their email address and password.
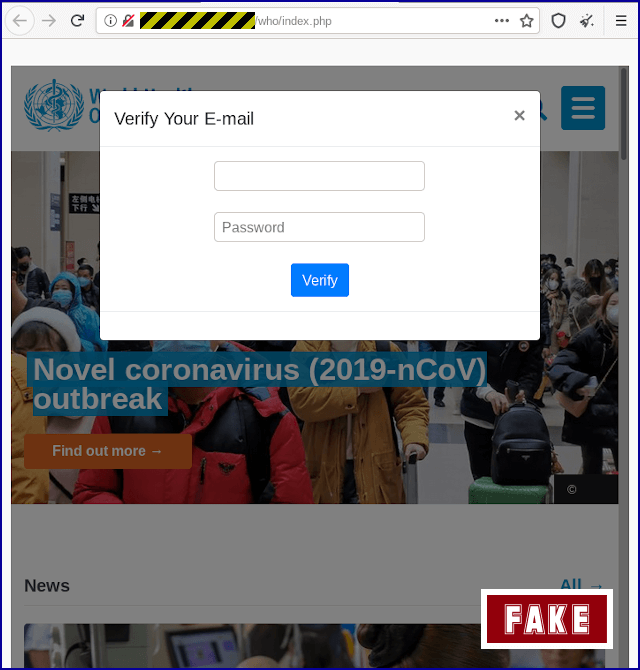
Image courtesy of Sophos
4. Internal organization alert
This phishing attack takes a corporate approach by impersonating a company’s president to deliver an attachment disguised as tips to prevent infection. The attachment is designed to infect an employee’s machine with malware.
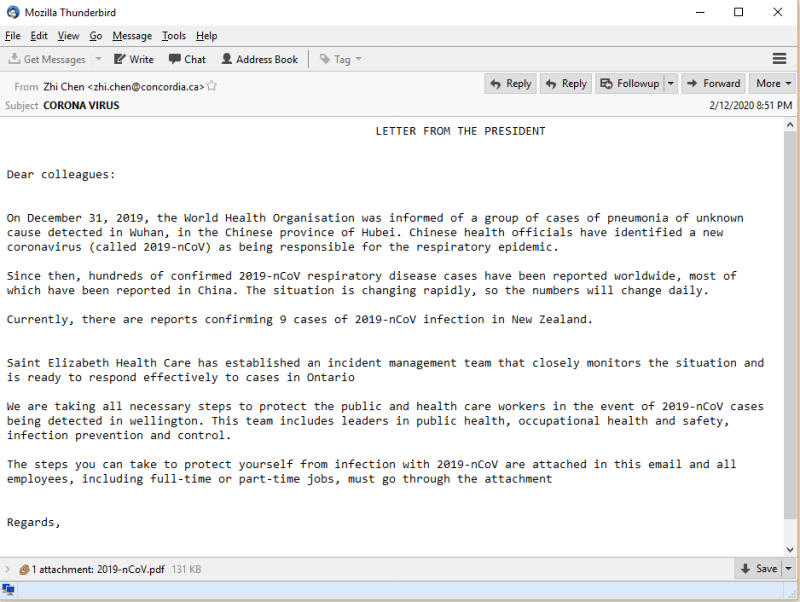
Image courtesy of Trustwave
5. New cases in your area
This attack preys on the fears of Coronavirus spreading near the victims’ location. Disguised as a CDC alert, this phishing email tricks victims into clicking a malicious link by offering an updated list of new cases of the virus documented near them.
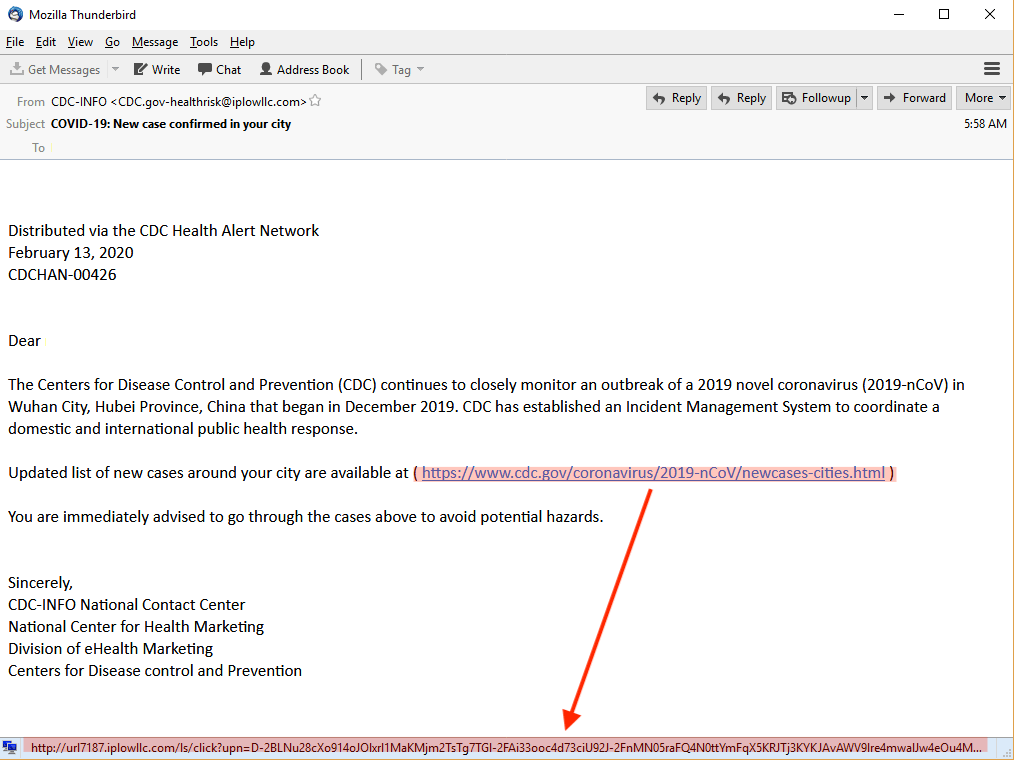
Image courtesy of Trustwave
6. The donation scam
Like the tried-and-true donation scams used after natural disasters, this phishing attack solicits donations to fight the spread of the coronavirus. The attack imitates a CDC emergency outreach email and asks victims to deposit money into a Bitcoin account.
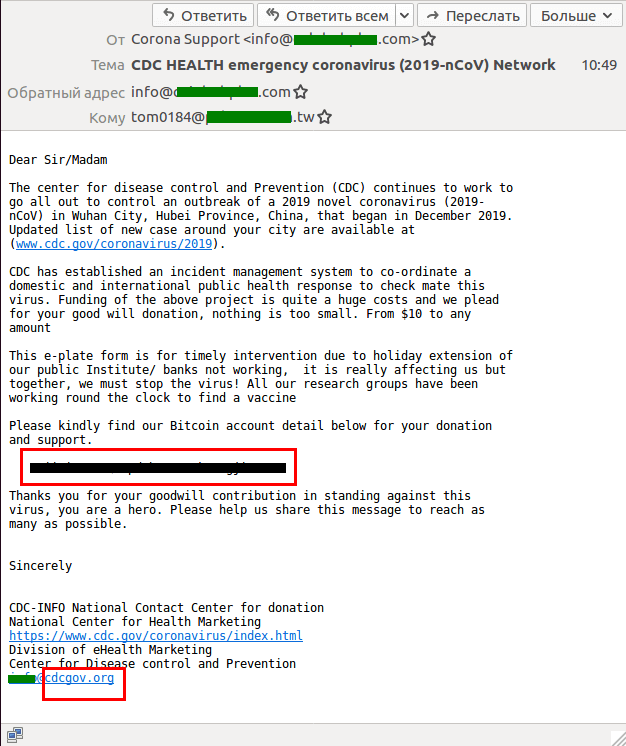
Image courtesy of Kaspersky
7. Information from the source
In this coronavirus phishing attack, the cybercriminal impersonates a doctor from The Central Hospital of Wuhan to play on victims’ fears, lend credibility to the email and convince the victim to download a malicious attachment.
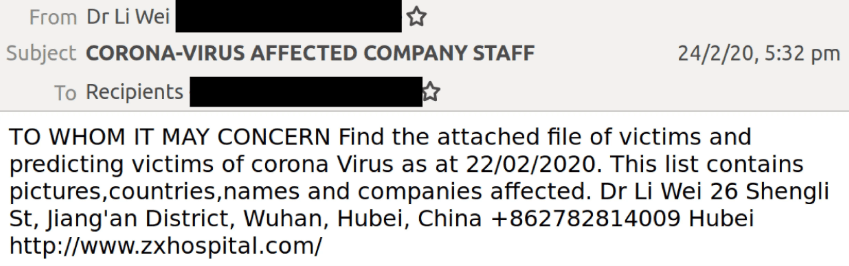
Image courtesy of Mailguard
8. Coronavirus domains
Along with the phishing tactics above, one of the largest concerns facing cybersecurity researchers is the massive increase in coronavirus-themed domain registrations. Many suspect that these coronavirus-related domains will be used for phishing attempts like those listed above.
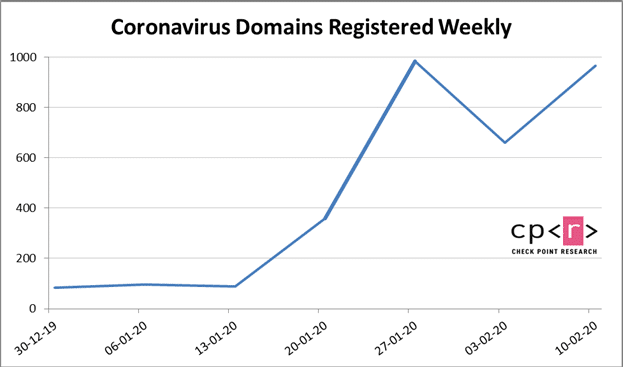
Image courtesy of Checkpoint
9. Fake product scam
Beyond the coronavirus phishing threats listed above, the SEC is warning consumers of investment scams related to products claiming to prevent, detect or cure coronavirus. Future phishing attacks may leverage this same tactic.
Prepare your employees for coronavirus phishing attacks
Coronavirus phishing attacks show no signs of slowing down. We’ve already seen a wide range of tactics cybercriminals are using to scam victims, infect their devices and steal information. By providing your employees with simulated phishing training, you can not only help them detect these phishing attacks at work to keep your organization secure, but also help them develop more secure habits to stay secure at home.
Security awareness and simulated phishing platforms like Infosec IQ come loaded with topical phishing templates (including templates for the attacks above) to help you prepare your workforce and keep your organization secure.

Get six free posters
Reinforce cybersecurity best practices with six eye-catching posters found in our free poster kit from our award-winning series, Work Bytes.
Run a free phishing risk test to see how it works!









