Your 2020 tax scam training guide
Hold on to your W-2s and returns because tax season is here! As if deductions, exemptions and return distribution wasn’t enough, tax season becomes open season for cybercriminals hunting for sensitive information, credentials and even a direct deposit of your employees’ tax returns.
To help you prepare your employees and protect your organization from the upcoming tax season scams, we compiled our top tax season phishing templates and training recommendations plus a free phishing poster and email template to help you communicate the importance of tax season security for every employee at your organization.
Phishing simulations & training
Is your organization susceptible to phishing attacks? Find out today with a free Phishing Risk Test!
Jump ahead
- Phishing templates
- Training recommendations
- Phishing attack type poster
- Internal communication template
Tax season phishing templates
Each of the following phishing templates are available in the Infosec IQ security awareness and training platform, allowing you to launch a simulated phishing campaign to test employees and deliver training to those who need it most.
1. W-2 attachment attack
Attack type: Attachment
Attack objective: Deliver malware
Infosec IQ template option: Tax forms - Attachment w/ drive-by link (Attachment)
W-2 phishing attacks come in many shapes and sizes and often strike in January, when employees are waiting to receive their W-2 from their employer. In this phishing email, the attacker baits the victim into clicking a malicious link or downloading a malicious attachment to install malware on their machine.
2. W-2 business email compromise (BEC) attack
 Attack type: BEC
Attack type: BEC
Attack objective: Steal employee or organization information
Infosec IQ template option: W-2 Request (BEC)
In this W-2 attack, the scammer poses as a manager or executive and targets HR staff to steal the W-2s and personal information of employees. With this BEC attack, the scammer doesn’t need access to a network or business systems. Instead, they only need the victim to reply to the email with the requested information.
3. Free online access to tax forms
Attack type: Drive by or data entry
Attack objective: Steal employee information or credentials
Infosec IQ template option: Tax Form Management Access (Drive by)
Generic offers to access your tax documents are another popular phishing tactic used to redirect victims to a malicious website. These attacks may also redirect the victim to a spoofed login page to steal the victim’s personal information such as their social security number.
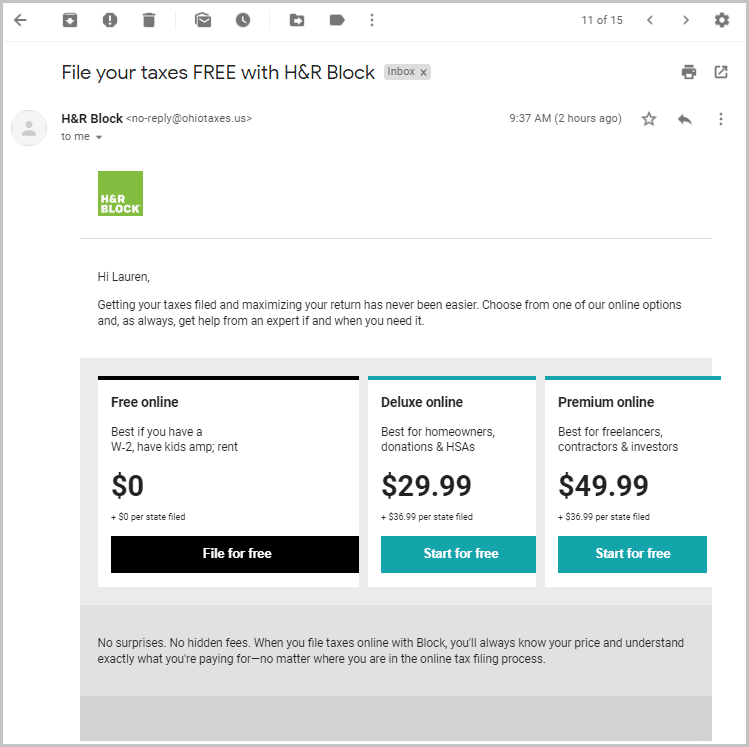
4. Tax preparation software drive by
Attack type: Drive by
Attack objective: Redirect to malicious site
Infosec IQ template option: H&R Block - File Your Taxes (Drive by)
Some scams approach tax season from the opposite direction by impersonating tax preparation software, services or CPAs. These attacks work like most common drive by attacks, but leverage tax season to create urgency with short-term or extravagant offers.
5. Tax return credential theft
Attack type: Drive by or data entry
Attack objective: Steal employee information or credentials
Infosec IQ template option: TurboTax - Return Accepted (Drive by)
In an even more sinister variation to tax preparation scams, some hackers attempt to steal login credentials to access victims’ tax software accounts. Once gaining access, attackers can retrieve personal information and documents or interfere with the victim’s filing process or tax return.
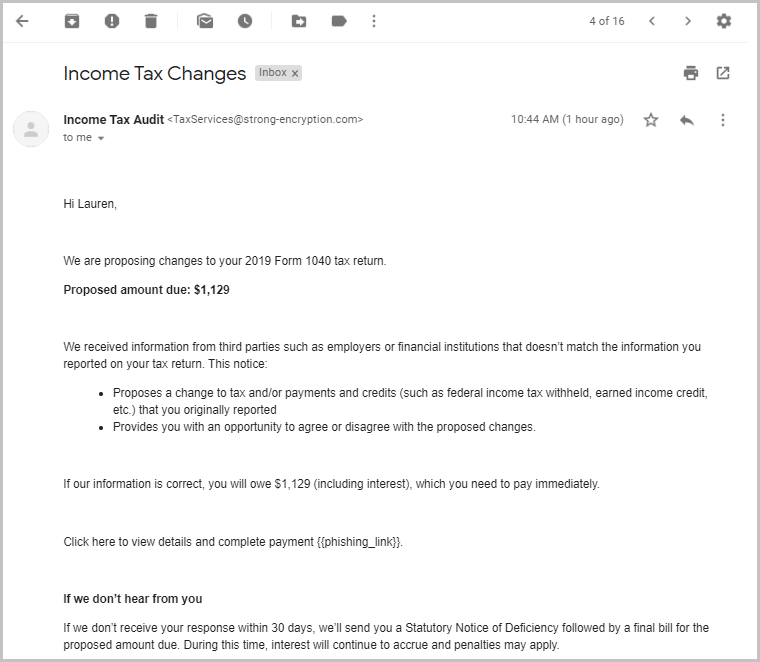
6. IRS tax notice
Attack type: Attachment, drive by or BEC
Attack objective: Steal employee information or credentials
Infosec IQ template option: Tax Notice (Drive by)
Although the IRS insists it will never contact taxpayers via email, text message or social media, scammers continue to use these tactics to trick victims into clicking malicious links, downloading attachments or even sending payments. Although these attacks peak during tax season, they are frequently used year-round.
Training recommendations
An abbreviated version of our core phishing training, this module will introduce learners to the concept of phishing, teach them how to quickly identify phishing messages and show them how to verify whether or not a message is legitimate.
This module walks learners through the key components of social engineering and how to recognize and respond to suspicious requests.
This interactive training module covers voice phishing, or vishing, a simple but effective technique cyber criminals and scam artists use to collect confidential information.
Spearphishing occurs when phishing messages are tailored for targeted individuals. This interactive module will help teams identify and avoid spearphishing attempts.
An abbreviated version of our core malware training, this module focuses on three key ways to prevent malware infections, details common sources of malware infections and discusses methods to help users avoid unsafe files.

Phishing attack type poster
Reinforce phishing training offline with this free poster covering common phishing attack types including tax scams.
Internal communication template
Communicate the importance of cybersecurity during tax season to every employee with this email template.

Get six free posters
Reinforce cybersecurity best practices with six eye-catching posters found in our free poster kit from our award-winning series, Work Bytes.
Together, let’s stay cybersecure this tax season!









