CompTIA Security+: SY0-301 Study Guide excerpt
NOTE: This article reflects an older version of the Security+ Exam – please see the current Security+ Certification page for the most up-to-date information.
Get Certified - Get Ahead
The CompTIA Security+ SY0-301 certification validates foundation-level security knowledge and skills and is recognized by organizations around the world. As an example, the U.S. Department of Defense requires personnel to have this certification to retain administrative access.
The CompTIA Security+: Get Certified Get Ahead: SY0-301 Study Guide (ISBN 978-1463762360) covers all six domains of the Security+ exam. At the beginning of the book, you'll find a listing of all the objectives along with the specific chapter where the objective is covered. Each chapter includes a list of the specific objectives covered in the chapter and Remember This blocks are sprinkled throughout to remind you of key information you'll need for the exam.
It includes a pretest at the beginning of the book, practice test questions at the end of each chapter, and a post test at the end of the book.All of the practice test questions include detailed explanations so you'll know why the correct answer is correct, and why the incorrect answers are incorrect.
Of course, there are also some great courses that many people find valuable to help them prepare. Infosec Institute hosts a five-day CompTIA Security+ Boot Camp taught by an expert security instructor. They also have Security+ Online Training in two separate formats depending on your needs.
The following is a partial excerpt from Chapter 1 "Mastering the Basics of Security"to give you an idea of how the book is laid out.
Chapter 1 Mastering the Basics of Security
CompTIA Security+ objectives covered in this chapter:
1.2 Apply and implement secure network administration principles
- 802.1x
- Implicit deny
2.4 Explain the importance of security related awareness and training
-
User habits
- Password behaviors
2.8 Exemplify the concepts of confidentiality, integrity, and availability
3.6 Analyze and differentiate among types of mitigation and deterrent techniques
-
Hardening
- Password protection
5.1 Explain the function and purpose of authentication services
- RADIUS
- TACACS
- TACACS+
- Kerberos
- LDAP
- XTACACS
5.2 Explain the fundamental concepts and best practices related to authentication, authorization, and access control
- Identification vs. authentication
- Authentication (single factor) and authorization
- Multifactor authentication
- Biometrics
- Tokens
- Common access card
- Personal identification verification card
- Smart card
- Single sign on
- ACLs
- Access control
- Implicit deny
5.3 Implement appropriate security controls when performing account management
-
Account policy enforcement
- Password complexity
- Recovery
- Length
- Lockout
6.2 Use and apply appropriate cryptographic tools and products
- CHAP and PAP
**
Before you dig into some of the details of security, you should have a solid understanding of core security principles. This chapter will present many of these core principles as an introduction. The second part of the chapter will cover authentication—how systems and users provide credentials to a system to verify their identity— including authentication used in remote access systems.
Exploring Core Security Principles
Security starts with several core principles that are integrated throughout an organization. These principles drive many security-related decisions at multiple levels. Understanding these basic concepts helps to give you a solid foundation in security.
Confidentiality, integrity, and availability together form the security triad. Each element is important to address in any security program. Additionally, several other core security principles, such as non-repudiation, defense in depth, and implicit deny, are addressed in any well-designed security program.
Confidentiality
Confidentiality helps prevent the unauthorized disclosure of data. It uses multiple methods, such as authentication combined with access controls, and cryptography. Authentication is presented later in this chapter, and access controls are covered in chapter 2.
Cryptography provides confidentiality by encrypting data. Many different encryption algorithms are available to provide confidentiality. Chapter 10 covers the relevant algorithms (such as AES and RSA) that you'll need to understand for the CompTIA Security+ exam.
Two of the key concepts related to confidentiality are:
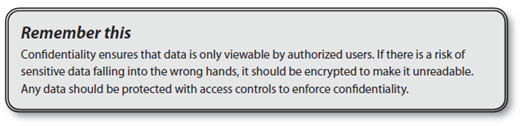
- Confidentiality ensures that data is only viewable by authorized users. Unauthorized personnel are unable to access the information.
- Encryption also enforces confidentiality. You can use various encryption algorithms to encrypt or cipher the data to make it unreadable. If the encrypted data falls into the wrong hands, the unintended recipient will not be able to read it.
Many elements of security help to enforce confidentiality beyond encryption. These include elements such as authentication, access control methods, physical security, and permissions that combine to ensure only authorized personnel can access the data. This book presents all of these methods.
Integrity
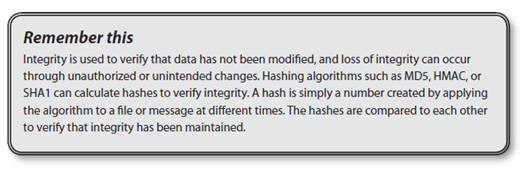
Integrity provides assurances that data has not been modified, tampered with, or corrupted. Ideally, only authorized users modify data. However, there are times when unauthorized or unintended changes occur. This can be from unauthorized users, or through system or human errors. When this occurs, the data has lost integrity.
You can use hashing techniques to enforce integrity. Chapter 10 presents the relevant hashing algorithms, such as MD5, SHA, and HMAC. Briefly, a hash is simply a number created by executing a hashing algorithm against data such as a file or message. As long as the data never changes, the resulting hash will always be the same. By comparing hashes created at two different times, you can determine if the original data is still the same. If the hashes are the same, the data is the same. If the hashes are different, the data has changed.
For example, a simplistic hash of a message could be 123. The hash is created at the source and sent with the message. When the message is received, the received message is hashed. If the hash of the received message is 123 (the same as the hash of the sent message), data integrity is maintained. However, if the hash of the received message is 456, then you know that the message is not the same. Data integrity has been lost.
Hashes can be applied to messages such as e-mail, or any other type of data files. Some e-mail programs use a message authentication code (MAC) instead of a hash to verify integrity, but the underlying concept works the same way.
Hashing techniques are also used to verify that integrity is maintained when files are downloaded or transferred. Some programs can automatically check hashes and determine if a file loses even a single bit during the download process. The program performing the download will detect it by comparing the source hash with the destination hash. If a program detects that the hashes are different, it knows that integrity has been lost and reports the problem to the user.
In other instances, a website administrator can calculate and post the hash of a file on the website. Users can manually calculate the hash of the file after downloading it and compare the calculated hash with the posted hash. For example, the md5sum.exe is freeware to calculate MD5 hashes, and sha1sum.exe is freeware to calculate SHA1 hashes. Chapter 10 shows how to do this in the "Providing Integrity with Hashing" section. If a virus infected a file on a file server, the hash on the infected file would be different from the hash on the original file (and the hash posted on the website).
It's also possible to lose data integrity through human error. For example, if a database administrator needs to modify a significant amount of data in a database, the administrator can write a script to perform a bulk update. However, if the script is faulty, it can corrupt the database, resulting in a loss of integrity.
Two key concepts related to integrity are as follows:
- Integrity provides assurances that data has not modified, tampered with, or corrupted. Loss of integrity indicates the data is different. Unauthorized users can change data, or the changes can occur through system or human errors.
- Hashing verifies integrity. A hash is simply a numeric value created by executing a hashing algorithm against a message or file. Hashes are created at the source and destination or at two different times (such as on the first and fifteenth of the month). If the hashes are the same, integrity is maintained. If the two hashes are different, data integrity has been lost.
Availability
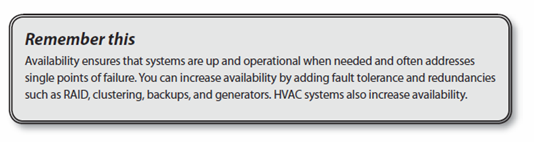
Availability indicates that data and services are available when needed. For some companies, this simply means that the data and services must be available between 8 a.m. and 5 p.m., Monday through Friday. For other companies, this means they must be available twenty-four hours a day, seven days a week, 365 days a year.
Chapter 9 covers many fault tolerance and redundancy techniques in more depth. A common goal of fault tolerance and redundancy techniques is to remove single points of failure (SPOF). If an SPOF fails, the entire system can fail. For example, if a server has a single drive, the drive is an SPOF since its failure takes down the server.
From a broad perspective, availability includes:
- Disk redundancies. Fault-tolerant disks such as RAID-1 (mirroring) and RAID-5 (striping with parity) allow a system to continue to operate even if a disk fails.
- Server redundancies. Failover clusters can be implemented that will allow a service to continue to be provided even if a server fails. In a failover cluster, the service switches from the failed server in a cluster to an operational server in the same cluster. Virtualization (covered in chapter 5) can also increase availability of servers by reducing unplanned downtime.
- Site redundancies. If a site can no longer function due to a disaster, such as a fire, flood, hurricane, or earthquake, the site can move functionality to an alternate site. The alternate site can be a hot site (ready and available 24/7), a cold site (a location where equipment, data, and personnel can be moved to when needed), or a warm site (somewhere in the middle of a hot site and cold site).
- Backups. If important data is backed up, it can be restored when it is lost. Data can be lost due to corruption, deletion, application errors, human error, and even hungry gremlins that can randomly eat your data. If data backups do not exist, then when it is lost, it will be lost forever.
- Alternate power. Uninterruptible power supplies (UPSs) and power generators can provide power to key systems even if commercial power fails.
- Cooling systems. Heating, ventilation, and air-conditioning (HVAC) systems improve the availability of systems by reducing outages from overheating.
Balancing CIA
It's possible to ensure the confidentiality, integrity, and availability of data equally. However, an organization may choose to prioritize the importance of one or two of these based on the goals of the organization, or the goals of a specific system. In other words, an organization can spend less money on ensuring confidentiality if confidentiality isn't as important.
One way of prioritizing these is with simple values such as low, medium, and high. For example, if a system holds proprietary secrets, confidentiality is of primary importance and the value of confidentiality is high. If the information is shared anonymously with the public, the importance of confidentiality is low. Medium indicates the confidentiality of the data has some importance to the organization.
As an example, imagine that you decided to host an online forum for users to share information about IT security-related concepts. Users can read data anonymously and post data after logging in. In this example, the importance of confidentiality is low, since anyone can read the data anonymously. You'd want to ensure the integrity and availability of the data, but it wouldn't be life shattering if data was modified or the site went down. The importance of integrity and availability is medium.
On the other hand, imagine an online gaming site that holds accounts for hundreds of thousands of users, including their credit card data. Users pay for the time they're online playing the game. If confidentiality of data is lost, customers will lose confidence in the company and may even sue. If the system data is not available when users want to play, users may not return. If users can modify other users' data, such as deleting their treasures, or the user's game data is not consistent, users could get frustrated and not return. In this example, the importance of confidentiality, availability, and integrity is equally high for all three. While this costs more to ensure, a data breach may result in higher losses for the online site in the end.
If you understand the concepts of confidentiality, integrity, and availability, and you understand the goals of a system, you should be able to match the concepts with the needs.
Non-repudiation
While non-repudiation isn't one of the core principles in the security triad, it is closely related and specifically mentioned in the objectives, making it an important core concept to understand. Non-repudiation provides proof of a person's identity and can be used to prevent individuals from denying they took a specific action.
In commerce, non-repudiation is commonly used with credit cards. If I buy something with a credit card and sign the receipt, I can't later deny making the purchase. My signature can be used to repudiate me if I deny making the purchase. In other words, my signature is used for non-repudiation.

Some common examples of non-repudiation within computer systems are:
- Using digital signatures to verify someone sent a message. If I send you an e-mail that is signed with a digital signature, you know that I sent it and I can't later deny doing so. Chapter 10 will cover how digital signatures work in detail, but, as an introduction, digital signatures provide authentication, integrity, and non-repudiation.
- Logging activity in an audit log. Audit logs will log details such as who, what, when, and where. The "who" in the audit log provides non-repudiation.
Defense in Depth
Defense in depth refers to the security practice of implementing several layers of protection. You can't simply take a single action, such as implementing a firewall or installing antivirus software, and consider yourself protected. You must implement security at several different layers.

As an example, if I drive my car to a local Walmart, put a five-dollar bill on the dash, and leave the keys in the car and the car running, there is a very good chance the car will not be there when I come out of the store. On the other hand, if I ensure nothing of value is visible from the windows, the car is locked, and it has an alarm system and stickers on the windows advertising the alarm system, it's a lot less likely that my car will be stolen. Not impossible, but less likely.
You've probably heard this as "there is no silver bullet." If you want to kill a werewolf, you can load your gun with a single silver bullet and it will find its mark. The truth is that there is no such thing as a silver bullet. (Of course, there is no such thing as a werewolf either.)
Applied to computers, security must be implemented at every step, every phase, and every layer. IT professionals can never rest on their laurels with the thought they have done enough and no longer need to worry about security.







