Security+ domain #2: Technologies & tools [DECOMMISSIONED ARTICLE]
NOTE: This article reflects an older version of the Security+ Exam – please see the current Security+ Certification page for the most up-to-date information.
The CompTIA Security+ Exam SY0-401 exam is being retired in favor of the newly updated version, the SY-501 exam. The certification remains the same at its core, but there are some changes that you will need to know about if you are going to take the exam in 2018. In this article, we will look at Domain 2: Technologies and Tools, and what you will need to know for the exam in order to pass.
Changes to the domain structure
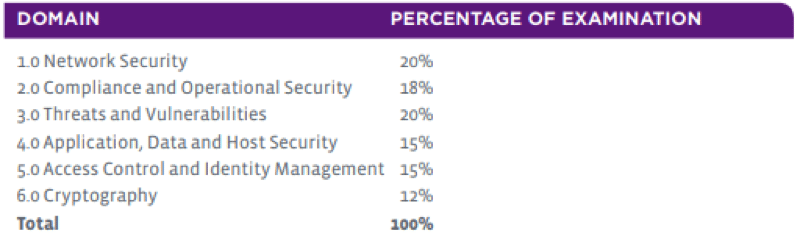
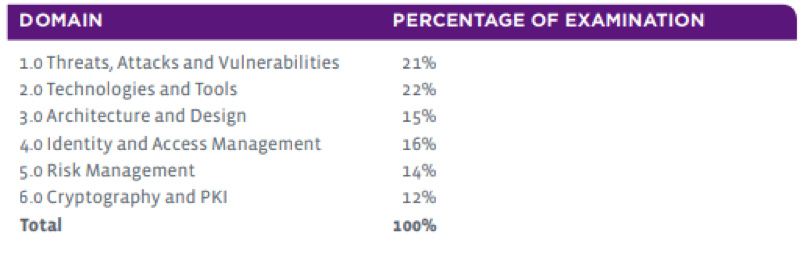
There has been a remodeling of the way the domains are laid out in the CompTIA Security+ exam. The information that you need to learn has not changed too much, but there are certain additional elements that need to be understood for candidates who wish to take the new SY0-501 exam. These changes are shown below:
SY0-401
SY0-501
Technologies and tools
With all of this in mind, we will take a look at Domain 2: Technologies and Tools. Hopefully, this will help you to understand what the exam seeks to test with regard to your knowledge in this area, and how you can improve your chances of passing the SY0-501 exam.
Exam objectives 2.1
Install and configure network components, both hardware and software-based, to support organizational security
This section of the exam objectives tests your knowledge of general hardware and software components, and how they are important to secure and manage. While you will not need to go into too much detail about each specific item, you should at least be familiar with what each item does, and how it works. These items include:
- Firewall
- VPN concentrator
- NIPS/NIDS
- Router
- Switch
- Proxy
- Load balancer
For the complete list of exam objectives you can download the CompTIA Security+ SY0-501 in PDF format from here.
Logging events and the importance of using a SIEM solution are other areas that candidates must be familiar with. You must also be familiar with the aggregation, correlation of log data. Syslog is an application that must be understood for the exam.
Exam Objectives 2.2
Given a scenario, use appropriate software tools to assess the security posture of an organization.
The Security+ exam expects you to understand how a protocol analyzer and network scanner works and how you would use one in a particular scenario. Users must be aware that nmap is a network scanner and they must understand how to use nmap and how to find hosts and computers on both local and remote computers. Protocol analyzers like Wireshark are also important for the Security+ exam. Users should understand that there are two parts to the protocol analyzer, the sniffer, and the analyzer itself, as well as how to use the application. TCP Dump is another sniffer that can be used on Linux systems.
Simple network management protocol (SNMP) is another important protocol that you will need to know for the Security+ exam. Understanding how host devices communicate via the agent software, as well as the individual ports that they use to communicate is also important. (These are UDP 161 and TLS 10161.) Devices like these are also known as managed devices. SNMP managers are also mentioned in the Security+, so being familiar with terms like network management systems is also a good idea.
Other important concepts to understand include:
- Protocol analyzer • Network scanners - Rogue system detection - Network mapping • Wireless scanners/cracker • Password cracker • Vulnerability scanner • Configuration compliance scanner • Exploitation frameworks • Data sanitization tools • Steganography tools • Honeypot • Backup utilities • Banner grabbing • Passive vs. active • Command line tools - ping - netstat - tracert - nslookup/dig - arp - ipconfig/ip/ifconfig - tcpdump - nmap - netcat
The Security+ SY0-501 exam deals with a lot of classic command line utilities and tools that it expects you to know. The exam doesn’t test your knowledge on how each tool works per se, but it does test your knowledge of when to use a specific tool in a certain scenario.
Some examples of these tools, as well as the scenarios that the exam expects you to be able to identify are:
- Ping—The exam will test your knowledge about how this utility is used to determine whether a device, host, or website is up and running, and whether or not you receive a valid response. Because ping operates on Layer 3 of the OSI model, the exam may ask questions indirectly that will test if you understand the concept, as well as where the ICMP requests exist within the OSI model. Ping is able to communicate with both IPV4 and IPV6 addresses as well, so be aware of the responses that you are receiving, and understand the command line switches that will help you to test both or how to run a ping consistently with the –t switch. Ping can also be used as a rudimentary DNS tool because pinging a website address will result in you receiving an IP address as a response. This means that the resolving of the ping has taken place and that DNS is indeed working. This all assumes that you are using a Microsoft Windows system, so familiarizing yourself with how Linux and Unix’s ping operation works is also a good idea.
- Netstat—Test-takers will need to know how to run netstat with the appropriate command line switch when trying to identify any unauthorized connections, such as netstat –n. Other scenarios that might require you to use netstat for the exam arise when you suspect that your PC is hosting a service. Running netstat –a will reveal all ports that are listening on your PC, thereby giving you a clue as to what could be happening on your machine. Knowledge of port numbers is important here, because you will need to know what services are associated with which port number, which will let you infer if your netstat results are revealing any malicious activity on your system in the exam scenario.
- Tracert—The exam will test your ability to check the path that data takes by using this troubleshooting tool and showing how you would use it for diagnosing connectivity issues. The use of tracert normally gives users an idea of the location of the system fault and whether it is local (fixable) or remote (service provider issue). Understanding how you would use the tool, and under which conditions, will help you with your exam.
- ARP—ARP is a diagnostic tool that helps to determine what is happening with network hardware on your network. You will need to understand that ARP resolves a MAC address to an Ethernet address and how this would help with troubleshooting suspicious behavior on the network. You should know how to reveal your ARP cache by running ARP –a, and other important command options.
Other tools that you will need to be familiar with include:
- Nslookup/dig
- Ipconfig/ip/ifconfig
- Tcpdump
- Nmap
- netcat
Exam Objectives 2.3
Given a scenario, troubleshoot common security issues
The exam tests your understanding of common security situations that you would encounter on a day-to-day basis within your organization and how you would proceed in each scenario.
- Unencrypted credentials/clear text • Logs and events anomalies • Permission issues • Access violations • Certificate issues • Data exfiltration • Misconfigured devices - Firewall - Content filter - Access points • Weak security configurations • Personnel issues - Policy violation - Insider threat - Social engineering - Social media - Personal email • Unauthorized software • Baseline deviation • License compliance violation (availability/integrity) • Asset management • Authentication issues
Exam Objectives 2.4
Given a scenario, analyze and interpret output from security technologies
For this section of the exam objectives, you should be familiar with the output from the following security technologies.
- HIDS/HIPS • Antivirus • File integrity check • Host-based firewall • Application whitelisting • Removable media control • Advanced malware tools • Patch management tools • UTM • DLP • Data execution prevention • Web application firewall
You must understand what data could be useful in a given scenario and what the most important information is, depending on what it is needed for. For example, if you detect malware on a system, what would the best way to analyze the damage that it did to the system that it infected and what would you be looking for in the logs? Each scenario is different, so finding examples of the above examples is a good idea leading up to the exam.
Exam Objectives 2.5
Given a scenario, deploy mobile devices securely
The rate at which mobile devices and personal electronics have entered the workplace has created many security issues for IT professionals to contend with. For the exam, candidates must have a basic understanding of the connection methods used by mobile devices, such as: Cellular, WiFi, SATCOM, Bluetooth, NFC, etc.
Understanding mobile device management concepts and how they can affect a modern organization is also very important. Some of these concepts include: application management, content management, remote wipe, geo-fencing, geolocation, and other mobile-related issues, such as screen locks, passwords and pins, and push notification services.
Deployment models are important to understand, as candidates will likely need to answer questions relating to their implementation in the exam. The Deployment models are: BYOD, COPE, CYOD, corporate-owned, and VDI.
Exam Objectives 2.6
Given a scenario, implement secure protocols
This section of the exam objectives requires candidates to understand secure protocols and how they would be implemented based on a scenario. The protocols would need to be matched with a use case to show that the candidate understands not only how the protocol works but what services it works in conjunction with. Examples of protocols are: - DNSSEC - SSH - S/MIME - SRTP - LDAPS - FTPS - SFTP - SNMPv3 - SSL/TLS - HTTPS - Secure POP/IMAP. Use cases for these protocols include: - Voice and video - Time synchronization - Email and web - File transfer - Directory services - Remote access - Domain name resolution - Routing and switching - Network address allocation - Subscription services.
Conclusion
Those wishing to take the CompTIA Security+ SY0-501 exam will need to follow the exam objectives closely and understand each of the points that are mentioned under each domain. There is a lot of work to go through and hopefully this article has helped you to look at how you could go about preparing for your exam. Infosec Institute is currently offering a fantastic Security+ Training boot camp for those wishing to get started with their Security+. More information can be found here about this fantastic hands-on learning experience.