Security+ Domain #6: Cryptography (SY0-401) [DECOMMISSIONED ARTICLE]
NOTE: This article reflects an older version of the Security+ Exam – please see the current Security+ Certification page for the most up-to-date information.
Introduction
Cryptography falls into the sixth and last domain of CompTIA’s Security+ exam (SYO-401) and contributes 12% to the exam score. The Security+ exam tests the candidate’s knowledge of cryptography and how it relates to the security of networked and stand-alone systems in organizations. To pass the Security+ exam, the candidates must understand both symmetric and asymmetric cryptography, as well as in-band vs. out-of-band key exchange, encryption methods and their differences, and cryptography attacks.
Cryptography Concepts
IT security experts employ cryptographic systems to meet various fundamental goals, including:
- Confidentiality: It’s the act of ensuring that the message is unavailable to unauthorized users.
- Integrity: Integrity ensures that a message isn’t manipulated or altered during the transit.
- Authentication: It verifies the claimed identity of users and has paramount importance in cryptosystems.
Symmetric vs. Asymmetric
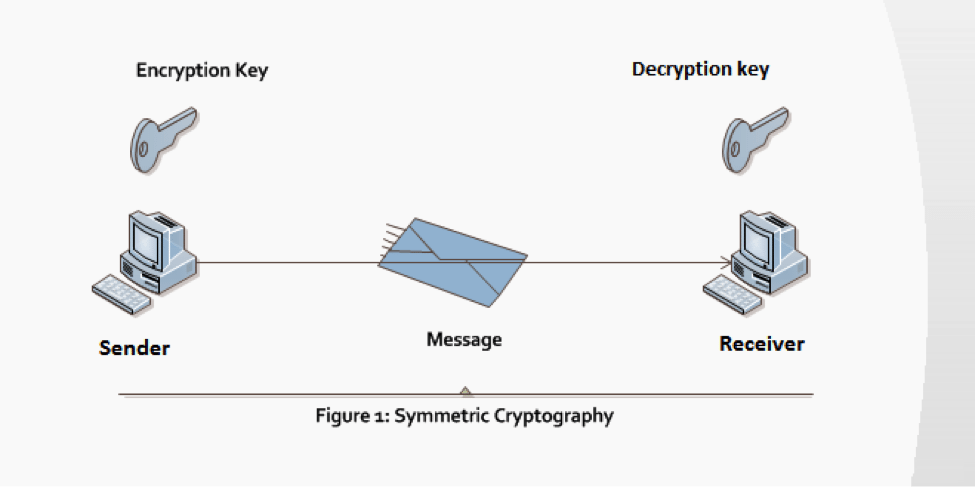
Symmetric cryptography, also called secret-key or private-key cryptography, is an encryption scheme in which both parties (sender and receiver) use the same key for encryption and decryption of the message (see Figure 1). The sender utilizes the private key to encrypt the message and transmits it to the receiver. The receiver, who is in possession of the same private key, employs it to decrypt the message successfully.
Symmetric cryptography is very fast compared to asymmetric cryptography. Its speed is due to straightforward and efficient algorithms and the fact that a single shared key is used to encrypt and decrypt the message. Symmetric cryptography is secure only as long as the shared key is kept private. If a shared key is stolen or compromised, true protection cannot be ensured. To make the key secure, the communicating parties should implement a preferred method, which is a public key infrastructure (PKI) solution. Some other solutions include advanced encryption standard (AES), triple data encryption standard (3DES), blowfish, twofish, and Rivest Cipher 6 (RC6). Another good approach for symmetric cryptography is to use the larger key.
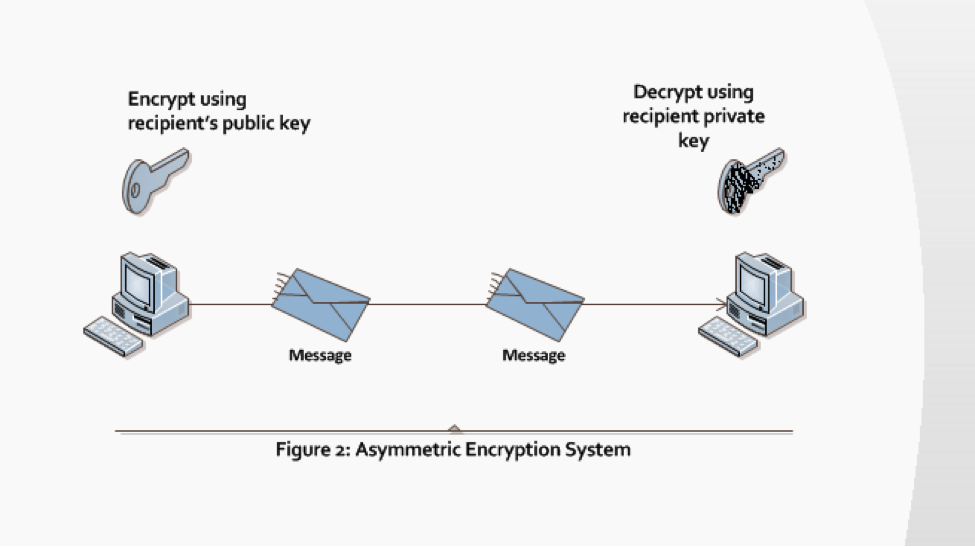
Asymmetric cryptography, also called public-key cryptography, is an encryption scheme in which the communicating parties use a different, but mathematically related, pair of keys to encrypt and decrypt the message (see Figure 2).
Although the keys are mathematically similar, they cannot be derived from each other. The key pairs consist of a public key and a private key. The use of the key pairs makes asymmetric cryptography much more scalable than symmetric cryptography. The public key is known and open. On the other hand, the private key must be kept private and secure, and only the recipient can possess it. The sender encrypts the message with the intended recipient’s public key and then the receiver decrypts the message with a private key that only he/she owns.
Because asymmetric cryptography is much slower than symmetric cryptography, it isn’t fit for the encryption of a large amount of data. In that case, symmetric cryptography will be the best fit. The common solutions for asymmetric encryption include the Rivest, Shamir, and Adelman (RSA), Diffie-Hellman, ElGamal, and elliptic curve cryptography (ECC).
Session Keys
Session keys are encryption keys used for a communication session. Session keys can be either symmetric or asymmetric and are randomly generated for a single session.
In-Band vs. Out-Band Key Exchange
An in-band key exchange is an exchange by two or more parties of a public key over the Internet or through an existing communication channel. The In-band is less secure because man-in-the-middle attack could intercept the data.
On the other hand, an out-of-band key exchange is an exchange by two or more parties of a private key outside the Internet and outside of the current communication channel. For example, smart cards, ExpressCard/PC Card technology, and USB drives can store the private keys for authentication and, when these keys are delivered outside of a network, the out-of-band key exchange takes place. It’s more secure than in-band exchange key because any attack trying to access the initial channel is less likely to have access to the alternate communications path.
Fundamental Differences and Encryption Methods
Block vs. Stream
Block and stream are two sub-forms of symmetric cryptography. A block cipher breaks the plain text into fixed-length segments called blocks and operates on each block separately. Encryption algorithms are also applied at the same time.
A stream cipher encrypts data one bit at a time, unlike block cipher, which works on blocks of plain text. Stream ciphers, in terms of design, are faster than block ciphers.
A block cipher uses the same key to encrypt each of the blocks, while a stream cipher uses different keys to encrypt each bit.
Hashing
Hashing is used to protect the integrity of a message by preventing it from being improperly accessed during transmits over a network. Hashing produces a unique identifier, which can be a hash, hash value, checksum, or fingerprint. A hash function is used to generate the identifier. The common hash algorithms include Message Digest 5 (MD5), MD4, MD2, and Secure Hash Algorithm (SHA-1). Hashing attacks are done by using reverse engineering. Furthermore, the hackers mostly use hashing attacks to crack the passwords.
Steganography
Steganography is a process of hiding a message in a communication medium, such as a digital audio file, video file, or image file. Steganography uses the least significant bit (LSB) method to hide the message. Another common form is to hide the text inside the graphics. If an attack occurs, the entire message can instantly be compromised. Brute-force attacks, in which the hackers try to extract the hidden message from the communication channel, are often used.
Digital Signatures
Digital signatures are used to prove that a message was sent from a particular user and that the message was not altered while in transit. A digital signature uses either an asymmetric or symmetric encryption solution and involves a hashing algorithm as well.
What Type of Cryptographic Attacks Do You Need to Know for Security+ Exam?
There are some common cryptographic attacks, including:
Birthday Attacks
Birthday attacks are examples of attacks targeted at the keys. A birthday attack takes place on a simple premise. For example, if there are 30 people in a house, there is some probability that three of them will have the same birthday. The probability would increase if the additional people enter the house. Probability doesn’t ensure the occurrence of something. Instead, it only guesses that something is more likely to take place. If the key is hashed, there is a possibility that, given enough time, the hacker can create another value that would give the same hash value. The birthday attack is so dangerous that even an MD5 hash is vulnerable to it.
Man-in-the-Middle Attack
A man-in-the-middle attack is an eavesdropping attack in which an attacker positions himself in the communication channel between a client and server or any two communicating entities. With this attack, the attackers can secretly modify the communication channel.
To prevent man-in-the-middle attacks, security experts can take some countermeasures, including secure encryption techniques, such as IPsec, and the use of the strong authentication methods, such as multifactor authentication, mutual authentication, certificates, and Kerberos.
Side-Channel Attacks
Side-channel attacks are based on data obtained from the physical infrastructure of cryptosystems, rather than theoretical deficiencies in the algorithms. For instance, power consumption, timing information, electromagnetic leaks, or even sound can provide useful information that can be exploited to break down the system.
A side-channel attack can be further classified as:
- Electromagnetic attack
- Timing attack
- Power-monitoring attack
- Cache attack
- Software-initiated fault attack
Mathematical Attack
A mathematical attack focuses on an encryption algorithm or any weak area in it, and the key mechanism. Mathematical attacks use statistical analysis and mathematical modeling to determine how the systems operate.
Security+ Boot Camp
The InfoSec Institute offers a Security+ Boot Camp that teaches you information theory and reinforces theory with hands-on exercises that help you learn by doing.
InfoSec also offers thousands of articles on all manner of security topics.