Security+: Technologies and tools - VPN concentrators [DECOMMISSIONED ARTICLE]
NOTE: This article reflects an older version of the Security+ Exam – please see the current Security+ Certification page for the most up-to-date information.
In the world of Cybersecurity today, there are of course many options that can be used to help secure network connections. This of prime importance for any business or corporation, as the probability that they will have remote employees is quite high. With this, there must be assurances that whatever shared resources, corporate information, and data, etc. that is transmitted back and forth is safe and secure and cannot be easily hijacked by a malicious third party.
This is where the role of the Virtual Private Network comes into play. A VPN can be specifically defined as follows:
“A virtual private network gives you online privacy and anonymity by creating a private network from a public Internet connection. VPNs mask your Internet protocol (IP) address, so your online actions are virtually untraceable. Most important, VPN services establish secure and encrypted connections, guaranteed to provide greater privacy than even a secured Wi-Fi hotspot.” (SOURCE: 1).
It is important to note that this definition assumes just a one-way connection has been established. For example, this would be from where the remote employee is working to where the physical location of the corporate server, and vice versa. However multiple VPN connections must be made, and this is where the role of the “VPN Concentrator” comes into play.
The VPN concentrator
The VPN Concentrator can also be defined as follows:
“A VPN concentrator is a type of networking device that provides secure creation of VPN connections and delivery of messages between VPN nodes. It is a type of router device, built specifically for creating and managing VPN communication infrastructures.” (SOURCE: 2). Thus, as one can see, this sort of device is not meant to be used for just a few VPN connections; rather, it is meant to be used for many, many VPN connections. This is an issue which will be addressed in this article.
As a Security+ Cert holder, it is important for you to understand exactly what the functionalities of a VPN Concentrator are, which are as follows:
- It establishes secure networking tunnels;
- It authenticates remote users who are attempting to access the central server(s);
- It negotiates and defines the tunnel permutations and parameters;
- It can encrypt as well as decrypt the information and the data that is transmitted across in it;
- It can manage the security keys that are associated with the VPN network that you are using;
- It can optimize the flow of Data Packet traffic across the various tunnel connections that have been established;
- It can also manage inbound and outbound network traffic at the endpoints.
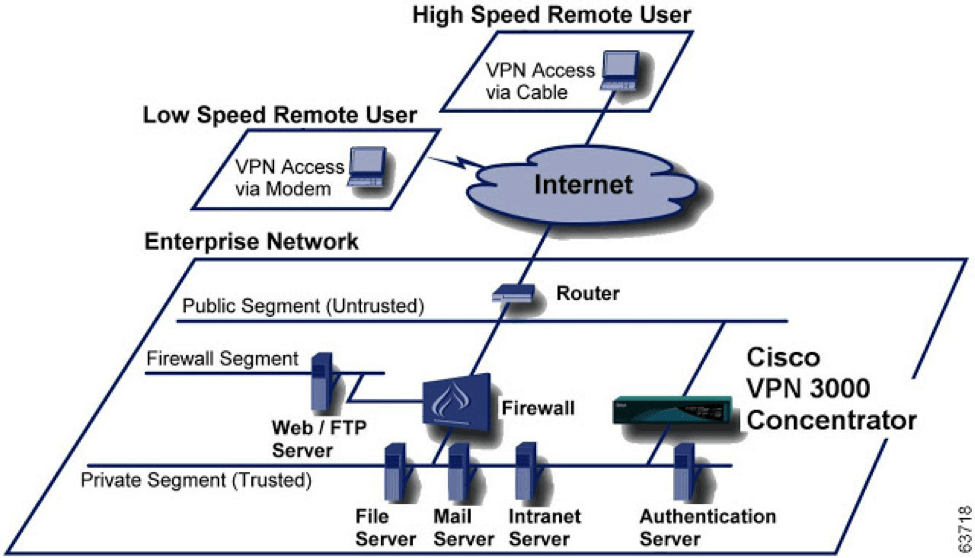
Also, you need to be aware that VPN Concentrators can be configured in many different ways and formats, depending of course upon the total number of remote users, and the security requirements of the business entity that is deploying it. The diagram below illustrates a typical configuration, in which the VPN Concentrator is situated just right next to the Firewall (it can also even be situated just behind it as well):
Key deployment issues with a VPN concentrator
Also, as a Security+ Cert holder, you need to be aware of the major issues, or considerations that are involved when deploying a VPN Concentrator. The following are the most typical kinds of scenarios that you could encounter:
- Using a VPN Concentrator using a VPN Router:
Before you can decide what, you need to go with, it is important first to conduct an assessment of the Security requirements, and the total number of users that are involved. If the entity is small enough, then going with a VPN Router would be the optimal choice. The costs of implementing a VPN Concentrator can be quite high, especially for a small business. Therefore, it is most optimal to have this set up in a medium to large sized enterprise, where there are many more remote employees that will constantly be needing access to shared resources and files. However, also, maintaining a VPN Router for a small business can also be somewhat expensive, as there will be extra staff that will be needed to maintain it and making sure that it is functioning daily.
- A VPN Concentrator vs. a Site to Site VPN:
It is important to keep in mind that a VPN Concentrator is typically used in those scenarios where there is a One to Many (1: N) set up. This simply means that many remote employees are logging into just one physical location, where the server resides at. However, there are also those instances where there will be many remote employees logging into multiple corporate locations (for example, that of a Fortune 100 company). In these instances, a solution is known as the “Site to Site VPN” will be required. Further details on this can be seen here.
- Using Secure Sockets Layer (SSL) or IPSec:
To establish a secure connection, the VPN Concentrator typically makes use of either SSL or IPSec. However, there are careful considerations that must be made in this regard. For example, using IPSec requires that a separate client software package to be installed onto the computer of the remote employee. Although this networking protocol does offer some of the highest levels of Security that are available, this typically requires extra IT staff to set up and deploy. Because of this, IPSec is the choice to be used where a majority of the remote employees remain in a fixed location. However, if your employees are constantly traveling, then using SSL becomes the network protocol of choice. By using this, the VPN Concentrator can be accessed from virtually anywhere around the world; there are fewer implementation costs, and extra client software does not have to be installed. SSL is also much more preferable to use with a VPN Concentrator if the remote employee must constantly access many Web-based shared resources and files.
Conclusion
Overall, this article has reviewed the important concepts and key issues that you, the Security+ cert holder must be aware of (in particular Remote Access, Site to Site, IPSec, Tunneling, etc.). Alternatively, if you are the candidate that is considering taking this particular exam, then the following resources will be of use to:
- Free mock exams:
http://comptiaexamtest.com/Security+SY0-401/tag/vpn-concentrator/
http://comptiaexamtest.com/Security+SY0-401/tag/vpn-concentrator/
http://comptiaexamtest.com/Security+SY0-401/tag/vpn/page/2/
- Free online training resource:
https://www.professormesser.com/security-plus/sy0-401/vpn-concentrators-3/
In the end, deploying a VPN Concentrator does take careful consideration and planning, as there are both Security and financial aspects that need to be considered. One of the greatest assets that a VPN Concentrator has to offer is that it makes use of Dynamic IP Addresses, where new ones are being constantly assigned. This makes it that much more difficult for the Cyber attacker to penetrate the actual VPN Network. This is in stark comparison to that of a Static IP Address, where only one is issued. Therefore, it can be easily guessed and thus be a grave Security vulnerability.
Sources
- Internet security privacy
- VPN concentrator
- How VPN concentrator works
- VPN concentrators
- VPN types
- Security+ 501 cert prep