Introduction to Reverse Engineering
In computing, reverse engineering is the process of understanding how things work and reusing the information to do something. This is applicable even to Android apps. You might reverse engineer Android apps for many reasons.
- Read another's code
- Find vulnerabilities in the code
- Search for sensitive data hardcoded in the code
- Malware Analysis
- Modifying the functionality of an existing application

Become a certified reverse engineer!
Decompilation v/s Disassembly
Decompilation is the process of converting software binaries to clear text format in a high-level language in which the source code is written so that developers can read it.
Disassembler, on the other hand, won't convert the binary to a high-level language text. It is only a one-to-one translation of bytes to text and gives us instruction mnemonics, which again can be understood by humans, but it is a little difficult when compared to reading original source code.
Generating DEX files from Java
In order to understand the reverse engineering process of Android apps, we should understand how apps are built.
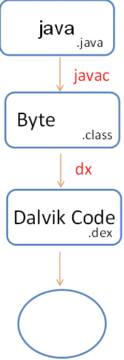
As shown in the above figure,
- Developers write their source code in the Java programming language. These files will have an extension ".java".
- These java files are given to the "javac" compiler, which generates ".class" files.
- These class files are given to the "dx" tool in order to generate ".dex" files.
- ".dex" files along with other resources are packaged as an".apk" file and run inside Dalvik Virtual Machine.
If you want to see the structure of the generated dex file, we can use 010 editor.
Before we proceed, download the following tools:
- 010Editor
- dex template
You can download 010 editor from the following link:
http://www.sweetscape.com/010editor/
You can download "dex template" here:
[download]
1. Unzip an APK file. We can use the unzip command in *nix based machines.
2. Open classes.dex using the 010 Editor.
3. Load the downloaded dex template.
4. Below is the figure with 010editor showing a dex file.
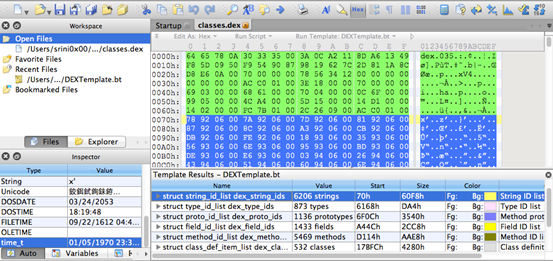
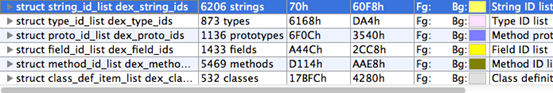
To understand more about the dex file format and how it works, please refer to the link below.
https://source.Android.com/devices/tech/dalvik/dex-format.html
Reversing Android Apps:
Let's now discuss how to reverse engineer Android apps.
1. Disassembling Android Apps
It is possible to get the smali version of code using a tool known as APKTOOL. This is discussed in some of our previous articles in this series.
Below are the steps to perform reverse engineering on Android apps to get smali code using APKTOOL.
Step 1. Download APKTOOL from the following link
http://ibotpeaches.github.io/Apktool/
Step 2. Run the following command to get the smali version of the code.
apktool d [app].apk
Step 3. In order to re-compile the application, we can simply change the switch to "b" by specifying the path to the folder where your modified code is placed.
apktool.bat b [path to the target folder]
A more detailed version of this is already discussed in this article.
2. Decompiling Android Apps
In this section, we discuss two ways to decompile Android apps.
Decompiling Android Apps using dex2jar and jad:
First, let's see how to decompile Android applications using dex2jar and jad.
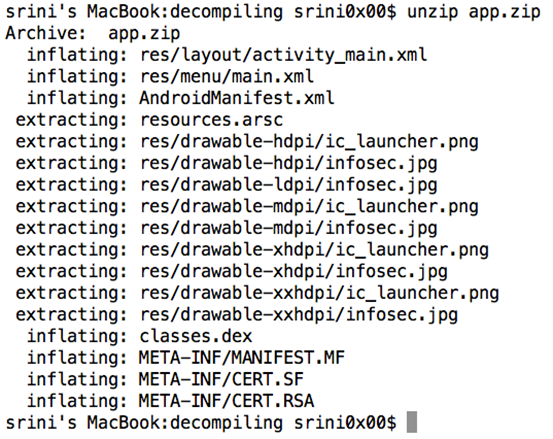
Step 1: unzip the apk file
As shown in the following figure, the target APK file is in my current folder.
Let's change the apk file's extension to ZIP as shown below.

Now, we can use unzip command as shown below.
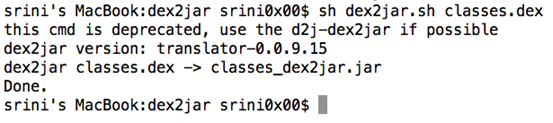
Step 2: dex2jar in action
Now, navigate to the folder where dex2jar is located and run the following command. This will generate a new jar file as shown below.
Step 3: Use unzip command to extract ".class" files from the newly generated jar file.
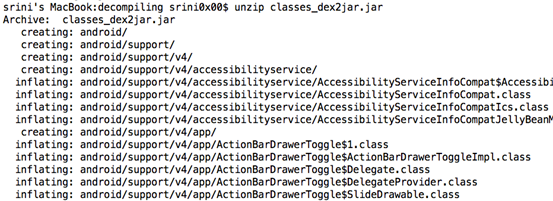
The above step creates some folders with the package name similar to what we get with APK tool.
In my case it is com.isi.securelogin
Navigate to that folder to see the .class files as shown below.
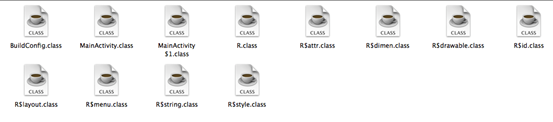
Now, we need to decompile them in order to get the .java files.
Step 4: Decompiling .class files to Java using JAD decompiler:
Jad is a popular java decompiler.
Download jad decompiler from the link below
Now, give all the class files we extracted to jad as input as shown below.

It will produce .java files in the same folder. This is shown below.
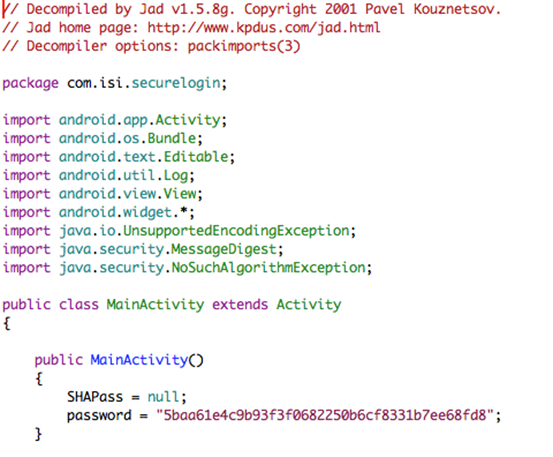
Decompiling Android apps using dex2jar and JD-GUI
This section shows how to decompile the apps using dex2jar and JD-GUI. The only difference between this method and the previous method is usage of JD-GUI as a replacement to JAD.
Download JD-GUI from the link below.
Step 1: unzip the apk file
Let's change the apk file's extension to ZIP as shown below.

Now, we can use the unzip command as shown below.
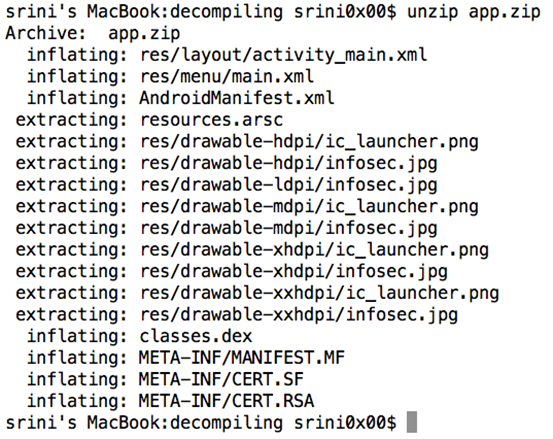
Step 2: using dex2jar
Similar to what we did earlier, navigate to the folder where dex2jar is located and run the following command. This will generate a new jar file as shown below.
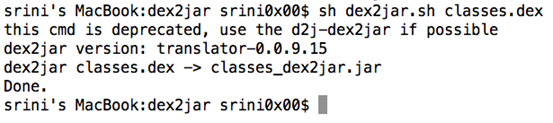
Step 3: Now, open this newly generated jar file using JD-GUI as shown below.
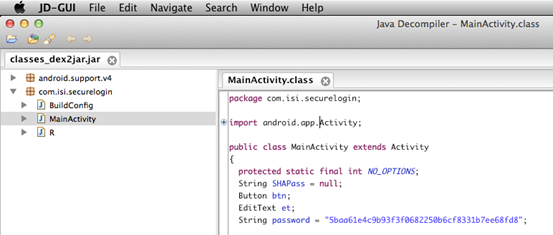
This will show us the decompiled Java code.