Cyber risks for Industrial environments continue to increase
ICS Attacks continues to increase worldwide
Industrial control systems (ICS) are a privileged target of different categories of threat actors. According to IBM Managed Security Services, the number of cyber-attacks increased by 110 percent in 2016 compared to 2015.
Researchers observed a significant increase of brute force attacks on supervisory control and data acquisition (SCADA) systems.

Figure 1 - Number of cyber-attacks (IBM Managed Security Services report)
Researchers at IBM observed an increase in ICS traffic caused by SCADA brute-force attacks, in many cases, operators exposed control system on the Internet with default credentials or weak passwords.
In December, IBM warned of the availability of a penetration testing framework named smod that was used in many attacks in the wild. The framework was published on the GitHub repository in January 2016, and according to the experts, it could be used to assess the Modbus serial communications protocol. Hackers abused the tool to power brute-force attacks.
"In January 2016, GitHub released a penetration testing solution that contained a brute-force tool that can be used against Modbus, a serial communication protocol. The public release and subsequent use of this tool by various unknown actors likely led to the rise in malicious activity against ICS in the past 12 months." states the blog post published by IBM Managed Security Services.
Attackers in the US accounted for the majority of ICS attacks in 2016 (60%), followed by Pakistan (20%), and China (12%). The United States also topped the list of the top 5 destination countries; this is normal considering that in the US there is the largest number of internet-connected ICS systems in the world.
The report mentions the following three notable ICS attacks occurred in the last years.
- The 2013 New York dam attack. Iranian hackers penetrated the industrial control system of a dam near New York City in 2013, raising concerns about the security of US critical infrastructure.
- The 2015 Ukrainian power outage. Experts speculated the involvement of the Russian Government. According to security experts, the BlackEnergy malware was a key element of the attack against Ukrainian power grid that caused the power outage.
- The 2016 SFG malware attacks. The Labs team at SentinelOne recently discovered a sophisticated malware dubbed Furtim specifically targeting at least one European energy company.
The report warns organization in any industry of cyber-attacks against ICS system and urges the adoption of necessary countermeasures.
"Organizations across all verticals must take full responsibility for protecting their own assets and consumers. There should be no exceptions, since the best way to keep adversaries out of an ICS is to implement simple safeguards, best practices and risk management solutions." states the report.
ICS Malware – the MIMICS project
The Stuxnet case is the most notorious attack against an ICS after its disclosure experts in the IT security industry started looking at ICS malware with increasing interest.
Stuxnet demonstrated that malware infecting an industrial control system could cause serious damages and put in danger human lives.
Ben Miller, Director of the Dragos Threat Operations Center, recently conducted an interesting research based on data regarding ICS incidents collected over the last 13+ years.
The project is based on completely public datasets to analyze modern industrial control systems (MIMICS).
"In this project the Dragos, Inc. team looked at public data sources such as VirusTotal to identify malware and (in many cases) legitimate ICS files being uploaded to encourage a more nuanced discussion around security in the modern ICS." explains Dragos CEO, Robert M. Lee.
Miller discovered roughly 30.000 samples of infected ICS files and installers dating back to 2003, among them dangerous threats like Sivis, Ramnit, and Virut.
The researcher highlighted that the infections of ICSs are not rare events. Anyway, his team discovered only three publicly showcased pieces of ICS tailored malware: Stuxnet, Havex, and BlackEnergy2. There have been rumors around another couple of ICS tailored malware exploited in active campaigns, some of them studied by researchers at IronGate.
The MIMICS project revealed that multiple variants of the same malicious code disguised as software for Siemens programmable logic controllers (PLCs) had been detected ten times over the last four years. The last time this specific ICS malware was discovered was early March 2017.
"Starting in 2013 there were submissions from an ICS environment in the US for Siemens programmable logic controller (PLC) control software. The various anti-virus vendors were flagging it as a false positive initially and then eventually a basic piece of malware." continues Lee. "Upon our inspection, we found that variations of this file and Siemens theme ten times over the last four years with the most recent flagging of this malicious software being this month in 2017. In short, there has been an active infection for the last four years of an adversary attempting to compromise industrial environments by theming their malware to look like Siemens control software. The malware is simply crimeware but has seemingly been effective."
Industrial environments under attack, which are major concerns?
On March 2017, the Kaspersky Lab's ICS-CERT published a report on the threat landscape for industrial automation systems (ICSs) related to second half of 2016.
The report confirms that the number of targeted attacks on the Industrial sector continues to increase.
On average, in the second half of 2016, the security solutions deployed by Kaspersky Lab across the globe blocked attempted attacks on 39.2% of protected computers being part of industrial enterprise technology infrastructure.
The targeted systems include machines running Windows OS and performing the following functions:
- Supervisory Control and Data Acquisition (SCADA) servers.
- Data storage servers (Historian).
- Data gateways (OPC).
- Stationary engineer and operator workstations.
- Mobile engineer and operator workstations.
- Human Machine Interface (HMI).
According to Kaspersky, every month, an average of 20.1% of industrial computers is targeted by malware, the most used attack vectors are known malicious and phishing web resources (22%), removable media (11%) and email (8%).
The devices typically used by network administrators, developers and contractors are more exposed to cyber-attacks because they are often freely connected to the Internet, meanwhile stationary workstations on the operational network (OT) are more secure because they do not typically have an always-on Internet connection.
Top 15 countries based on the percentage of industrial computers attacked are Vietnam, Algeria, Morocco, Tunisia, Indonesia, Bangladesh, Kazakhstan, Iran, China, Peru, Chile, India, Egypt, Mexico, and Turkey. According to Kaspersky, Western European countries and the US are less targeted by hackers.
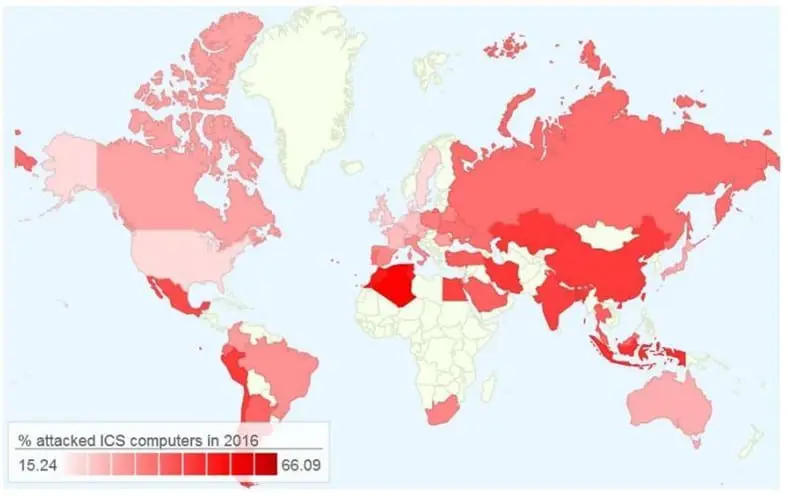
Figure 2 - Top 15 countries under attack (Kaspersky Lab's ICS-CERT)
Attackers leverage on both custom malware leveraging on zero-day exploits and widely available malicious codes to targeted ICS.
Kaspersky detected about 20,000 different samples of malware representing over 2,000 different malware families in the second half of 2016. Many malware were not specifically designed to target industrial automation systems; they include Trojan spies, financial malware, ransomware, backdoors, and Wipers (KillDisk).
"Remarkably, there is very little difference between the rankings of malware detected on industrial computers and those of malware detected on corporate computers. We believe that this demonstrates the absence of significant differences between computers on corporate networks and those on industrial networks regarding the risk of chance infections. However, it is obvious that even a chance infection on an industrial network can lead to dangerous consequences." reads the report.
According to Kaspersky, threat actors mostly leverage on spear phishing email to hit industrial companies such as metallurgical, electric power, construction.
Kaspersky Lab ICS-CERT detected a series of spear phishing attacks which began in June 2016 and that are still active.
"The attacks target primarily industrial companies – metallurgical, electric power, construction, engineering, and others. We estimate the number of companies attacked at over 500 in more than 50 countries around the world," reads the report issued by Kaspersky. "In all the cases that we have analyzed, phishing emails were sent on behalf of various supplier companies, customers, commercial organizations and delivery services, and contained offers to view updated pricelists, requests to check invoice information, review product prices, resend a supposedly damaged file or receive goods listed in a consignment note."
The attackers use to compromise corporate mail servers with spyware designed to steal account credentials, then exploit them to send out the spear phishing messages.
The weaponized documents used in the campaigns embedded RAT and backdoors, such as ZeuS, Pony/FareIT, Luminosity RAT, NetWire RAT, HawkEye, and ISR Stealer.
The hackers packed the above malware using VB and MSIL packers that were customized for the specific campaigns.
Kaspersky identified multiple vulnerabilities in ICSs in the last year; they reported 75 flaws, including 58 rated highly critical.
Analyzing the type of the flaws, we can see that the vast majority is DoS flaws (45), followed by RCE (16) and file manipulation issue (10).
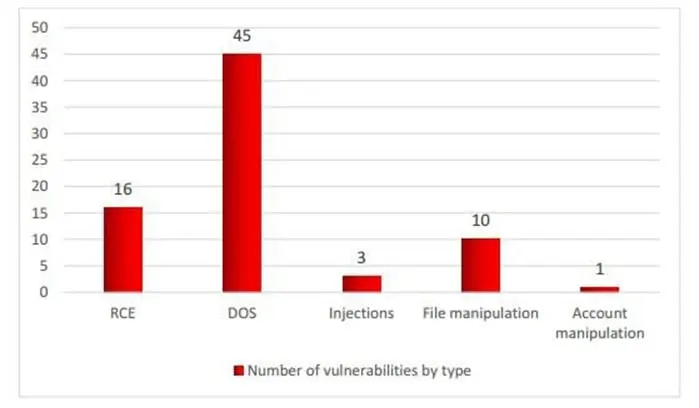
Figure 3 - Number of flaws in ICSs by type
Data included in the report published by Kaspersky CERT are confirmed by other studies and analysis shared by security firms and government organizations worldwide.
A few days ago, security firm FireEye published an interesting report on the attack surfaces of many industrial enterprise operations. The experts analyzed the systems used in several organizations in different industries, including energy and manufacturing.
The report outlines weaknesses affecting protocols, hardware, authentication, relationships, file integrity, and operating systems.
Unfortunately, many industrial environments are still too exposed to cyber-attacks, and despite the awareness on cyber threats, the problems highlighted in the report are not still present and not easy to fix.
The subversive six concerns for an industrial environment highlighted by FireEye are:
- Unauthenticated protocols
- Outdated hardware
- Weak user authentication
- Weak file integrity checks
- Vulnerable Windows operating systems
- Undocumented third-party relationships
Let's see each category:
Unauthenticated Protocols
According the experts from FireEye, communication protocols used in industrial environments to allow data exchange between sensor/actuator and the I/O of the PLC (e.g. Modbus, HART, CAN, Foundation Fieldbus, PROFIBUS), as well as the protocols used to communicate between PLCs and the management computers (e.g. DNP3, Modbus/TCP, BACnet, EtherNet/IP, etc.) often lack of authentication.
"When an ICS protocol lacks authentication, any computer on the network can send commands that alter the physical process, such as changing the set point or sending an inaccurate measurement value to the Human Machine Interface (HMI). This may lead to incorrect process operation, which damages goods, destroys plant equipment, harms personnel, or degrades the environment," states the report.
Experts suggest assessing any protocol used in the industrial environment, implementing bump-in-the-wire authentication solutions or VPNs, blocking unauthorized commands from certain IP addresses using deep packet ICS firewalls, configuring restrictive access control lists and firewall rules.
Outdated Hardware
The vast majority of organizations uses old hardware in their industrial environment that were not designed to be resilient to cyber-attacks.
"This hardware, such as PLCs, RTUs, VFDs, protective relays, flow computers, and gateway communicators, may operate too simplistically or lack the processing power and memory to handle the threat environment presented by modern network technology," the report says.
Experts suggest updating the hardware and minimize network connectivity of devices with outdated hardware by implement firewall rules.
Weak User Authentication
Authentication is the main problem for legacy systems that are exposed to serious risk. Default passwords, hard-coded passwords, and weak passwords are the most common problems in industrial environments.
"User authentication refers to the ability to ensure that only intended individuals can access a computer or use its programs. ICS users commonly authenticate by providing a password," states the report. "User authentication weaknesses in legacy control systems often include hard-coded passwords, easily cracked passwords, passwords stored in easily recoverable formats, and passwords sent in clear text. An attacker who obtains these passwords can often interact with the controlled process at will."
FireEye recommends that organizations should check that internal devices will not use credentials included in the lists of default and/or hard-coded ICS passwords.
Weak File Integrity Checks
One of the most important issues related to the systems in industrial environments is the integrity and the origin of data or code.
Integrity checks are usually implemented through cryptographic verification. FireEye identified the following problems for ICS:
- Weak software signing
- Weak firmware integrity checks
- Weak control logic integrity checks
Vulnerable Windows operating systems
Many systems in the industrial environments leverage on Windows OS, but often the OS versions they use are outdated exposing them to cyber-attacks.
"Engineering workstations and HMIs often run outdated and unpatched Microsoft Windows operating systems, leaving them exposed to known vulnerabilities. In some cases, this means that adversaries may access industrial systems without needing control systems specific knowledge," states FireEye.
In some cases, organizations cannot update or patch the systems, in this case, it is essential the adoption of compensating control to mitigate the risks of exposure.
Undocumented third-party relationships
"In our experience, ICS asset owners seldom document and track third-party dependencies in ICS software they operate. Many ICS vendors may not immediately know the third-party components they use, making it difficult for them to inform their customers of the vulnerabilities. Adversaries who understand these dependencies can target software the industrial firm may not even know it has," states the report.
Every time organizations acquire a software they need request that ICS vendors provide a list of third-party software and versions used in their products. In the past, vulnerabilities in open source libraries widely adopted have exposed applications using it. Vulnerabilities such as Heartbleed and Poodle impacted a significant number of ICS systems in industrial environments.
Vendors must provide timely notifications of vulnerabilities affecting their products.
Conclusions
According to security experts, cyber-attacks against industrial environments will continue to increase. Nation-state actors will launch some of the attacks, and their level of sophistication will be very high. However, most of the attacks will leverage on generic malware that wasn't specifically designed to target ICS systems.
The protection of ICSs is crucial, information shared by FireEye are very precious and highlights the importance of adopting simple countermeasures to improve the security of industrial environments.
Any security firm encourages asset owners and operators to implement these simple best practices to protect their environments.
References
http://securityaffairs.co/wordpress/54792/security/ics-attacks-2016.html
http://securityaffairs.co/wordpress/57412/malware/siemens-plc-ics-malware.html
http://securityaffairs.co/wordpress/57490/hacking/kaspersky-ics-cert-icss-attacks.html
https://securityintelligence.com/attacks-targeting-industrial-control-systems-ics-up-110-percent/






