ICS/SCADA threats and threat actors
Industrial control systems (ICS) and Supervisory Control And Data Acquisition (SCADA) systems play a critical role in critical infrastructure and industrial sector.
The term ICS is used to refer a broad range of systems, including SCADA systems, engineering workstations (EWS), and programmable logic controllers (PLCs).
Cybercrime gangs and nation-state actors could target them causing interruption of operations and consequent financial losses, and potentially posing a threat to human lives.
Learn ICS/SCADA Security Fundamentals
These systems are high-value targets for threat actors that aims at disrupt business operations and processes for extortion or sabotage purposes.
Over the past years ICS systems have passed through isolated systems to connected platforms based on open architectures and standard technologies. The connection to intranets and communication networks has increased their surface of attacks.
Most of them lack of security by design and are vulnerable to a broad range of attacks. Vulnerabilities in the operating systems and software, improper network segmentation, misconfigurations, are some of the most common attack vectors.
Other factors that have fuelled cyber attacks against ICS/SCADA systems include:
- The lack of device inventory and assessment;
- The use of legacy systems and devices running outdated hardware and software;
- The lack of network segmentation
- Limited access control and permission management
- Inadequate security policies for the ICS
- The lack of ICS specific configuration change management
- The lack of formal ICS awareness program and security training
- The lack of adequate password policy
- Unsecure remote access of ICS components
Security experts agree that the root cause of most of successful attacks against ICS systems are unpatched vulnerabilities in their software and the difficulty to mitigate the bug in critical environments without impacting the operations.
According to a report published by the industrial cybersecurity firm Claroty that provides data on the second half of 2020, the number of vulnerabilities discovered in industrial control system (ICS) products in 2020 (893 flaws) was 24,72% higher compared to 2019.
The researchers revealed that 449 vulnerabilities were disclosed affecting ICS products from 59 vendors during 2H 2020. The situation is worrisome if we consider that over 70% of the issues were rated as high or critical Common Vulnerability Scoring System (CVSS) scores.
“The number of ICS vulnerabilities disclosed in 2020 increased by 32.89% compared to 2018 and 24.72% compared to 2019. The primary factors for the increase are likely heightened awareness of the risks posed by ICS vulnerabilities and increased focus from researchers and vendors on identifying and remediating such vulnerabilities as effectively and efficiently as possible.” reads the report published by Claroty.
Fortunately, the number of high or critical flaws decreased compared with data in H1 2020, likely because researchers and vendors have spent a significant effort in searching for vulnerabilities in ICSs and address them. It is interesting to note that the majority of the vulnerabilities discovered in ICS systems (71.49%) are exploited through a network attack vector (i.e. remotely exploitable), and 89.98% of them don’t require special conditions to be triggered.
Most of the critical vulnerabilities reported in the ICS systems could be exploited by attackers to achieve remote code execution (RCE), while a third of the issue could also be exploited to trigger a denial-of-service condition or to disable the host network. Remote connectivity has become essential especially during the COVID-19 pandemic, in many cases engineers and employees of organizations managing ICS and SCADA systems would require remote access to interact with devices deployed in field avoiding to visit in person.
Anyway experts also warn of an increasing number of ICS vulnerabilities that are exploitable via local attack vectors, in this case the most common attack scenario sees organization’s employees being targeting with social engineering attacks such as phishing and spear-phishing campaigns.
Claroty researchers remarked the importance of sharing knowledge in the cyber security community and promote bug bounty programs, 60.8% of issues, in fact, were reported by third-party researchers.
“Among all third-party companies, there were 22 that reported their first disclosures, further evidence of growth in the ICS vulnerability research market. continues the report.
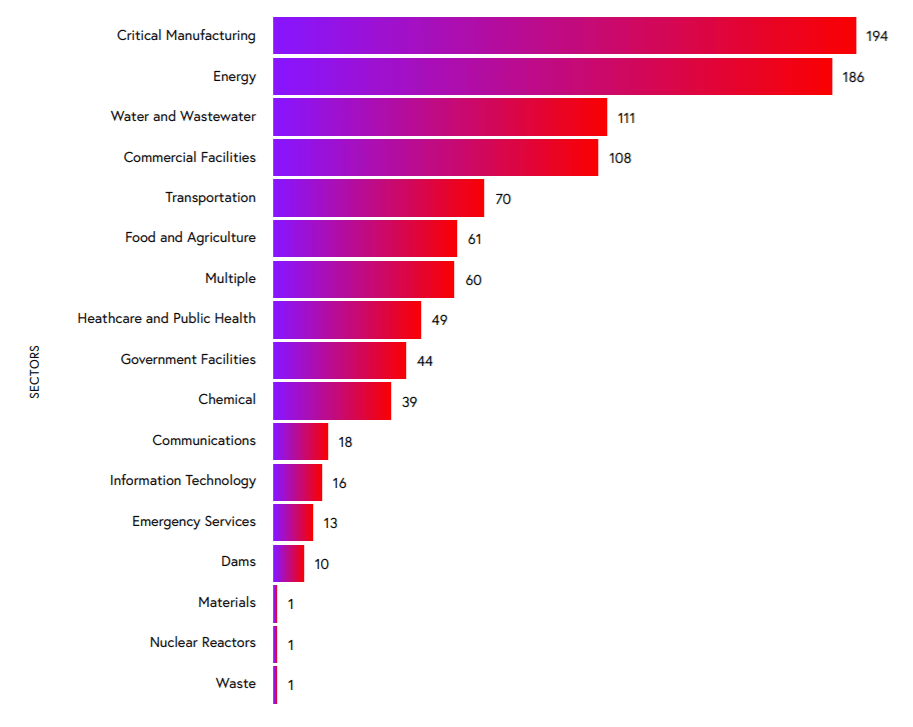
Top impacted infrastructure sectors in the second half of 2020 critical were manufacturing (194 vulnerabilities), energy (186), water and wastewater (111), and commercial facilities (108) were most impacted industries. The majority of the products with disclosed and patched flaws in the 2H of 2020 belong to Schneider, Mitsubishi and Siemens.
“Compounding the risk is the fact that attacks against ICS devices and OT networks tend to be targeted. While ICS and SCADA vulnerability research is maturing, there are still many decades-old security issues yet uncovered.” concludes the report. “For the time being, attackers may have an edge in exploiting them, because defenders are often hamstrung by uptime requirements and an increasing need for detection capabilities against exploitable flaws that could lead to process interruption or manipulation.”
To better understand the threat landscape for ICS engineering and integration sector let’s analyze data provided by researchers from Kaspersky ICS CERT in a report titled “Threat landscape for the ICS engineering and integration sector. 2020.”
Kaspersky shared data on cyberthreats that were blocked on computers used to manage industrial control equipment and targeting software used in ICS engineering and integration industry, including human-machine interface (HMI), OPC gateway, engineering, control, and data acquisition software.
"A key aspect in which of the ICS engineering sector is different from other industries is that an ICS engineering computer often has direct and indirect connections to various industrial control systems, some of which may even belong to other industrial enterprises. And while an ICS engineering computer has more access rights and fewer restrictions (such as application control, device control, etc.) than the average ICS computer, it also has a wider attack surface." reads the report published by Kaspersky.
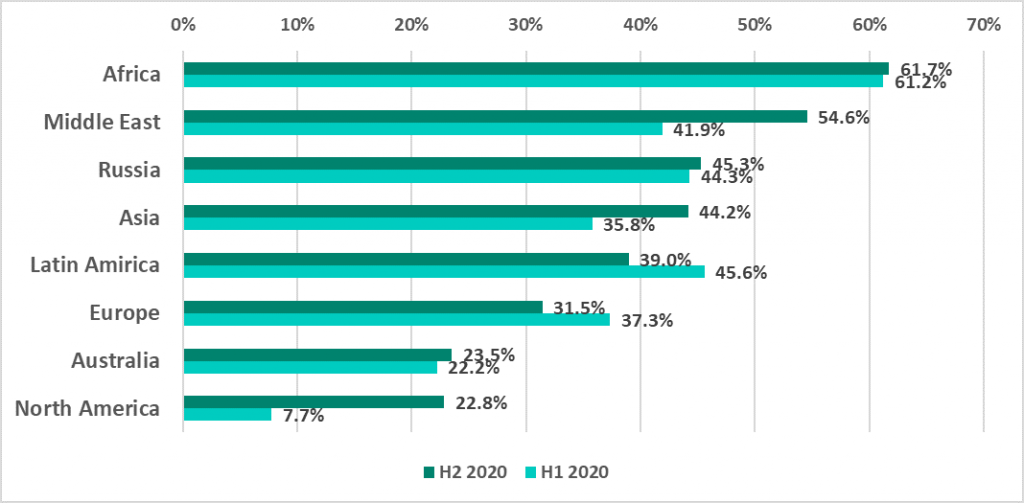
In H2 2020, 39.3% of computers in the ICS engineering and integration sector protected by Kaspersky were targeted by malware, an increase compared with detections for H1 2020 (31.5%). Building automation, automotive manufacturing, energy and oil & gas, suffered major increases in the ICS engineering sector.
The regions with the highest number infections attempts blocked by Kaspersky security solutions in H2 2020 are Latin America, the Middle East, Asia and North America. On the other end, the number of blocked malware attacks in Africa, Russia and Europe decreased in H2 2020 compared to H1 2020.
The highest percentage increase in H2 2020 (22.8%) was observed in North America, the majority of the attacks observed by the experts involved crypto-currency miners. The second region with the highest increase was the Middle East due to an outbreak of Fast-Load AutoLISP modules that spread within infected AutoCAD projects and other self-propagating worms that spread via USB.
Researchers reported that European ICS engineering organizations were mainly targeted by phishing campaigns attempting to deliver spyware and cryptocurrency miners.
The majority of computers in the ICS engineering sector are represented by desktop systems, but laptops remain more exposed to attacks via the internet, removable media devices, and email.
Computers that use VPN software are less exposed to online threats, but unfortunately, they represent only 15% of the total.
Computers with remote access software (64.6% of the total) are less exposed to internet threats, especially when VPN software is used, but these systems are exposed to attacks leveraging network services, such as SMB, MS SQL and RDP.
Who is targeting ICS/SCADA systems?
Industrial control systems (ICS) environments are a privileged target for threat actors, especially state sponsored hackers. Over the years, multiple groups launched attacks against oil and gas firms, water facilities and organizations in the energy sector.
One of the groups that focuses on organization in the oil and gas is tracked as HEXANE. The Hexane group has been active since at least the middle of 2018, it intensified its activity since early 2019 with an escalation of tensions within the Middle East.
The group targeted third-party companies, like telco service providers, to hit the final target in a classic supply chain attack. HEXANE leverages on weaponized documents used to drop the malware and compromise the target network.
The threat actor shows similarities with other groups such as Magnallium and Chrysene, both active since at least 2017 and involved in attacks on oil and gas companies. Anyway, experts pointed out that the Hexane group has different TTPs and has its own arsenal.
According to the experts at security firm Dragos who discovered Hexane, the group has not yet developed destructive capabilities.
Another group that focused on the oil and gas sector is tracked as XENOTIME, which is considered responsible for the 2017 Trisis/Triton malware attack that hit oil and gas organizations. In December 2017, the Triton malware (aka Trisis) was discovered by researchers at FireEye, it was specifically designed to target industrial control systems (ICS) system.
In 2019 the group expanded activity to Europe, the US, Australia, and the Middle East. In October 2018, FireEye experts discovered a link between the Triton malware, tracked by the company as TEMP.Veles, and the Central Scientific Research Institute of Chemistry and Mechanics (CNIIHM), that is a Russian government research institute in Moscow.
In 2019, according to security firm Dragos, the group targeted electric utilities in the United States and the Asia-Pacific (APAC) region.
Xenotime has been active since at least 2014, its activity was discovered in 2017 after it caused a shutdown at a critical infrastructure organization somewhere in Saudi Arabia.
The group used the Trisis malware (aka Triton and HatMan) in attacks aimed at Schneider Electric’s Triconex safety instrumented systems (SIS) through a zero-day vulnerability. The attack was discovered after a SIS triggered a shutdown of some industrial systems, which experts believe hackers caused by accident.
Dragos experts revealed that the attacks against entities in the United States and the APAC region were similar to ones that targeted organizations in the oil and gas sector. The good news is that all the attacks carried out by the Xenotime group failed into breaching the targeted organization.
Dragos warns that Xenotime poses a serious threat to electric utilities that uses ICS-SCADA systems similar to the ones in the oil and gas industries.
In 2018, security experts from the industrial cybersecurity firm Dragos warned of another threat actor tracked as Allanite that was targeting business and industrial control networks at electric utilities in the United States and the United Kingdom.
The experts linked the campaigns conducted by the Dragonfly APT group and Dymalloy APT, aka Energetic Bear and Crouching Yeti, to a threat actors they tracked as ‘Allanite.’
Allanite has been active at least since May 2017 and it is still targeting both business and ICS networks at electric utilities in the US and UK.
The APT group was conducting reconnaissance and gathering intelligence for later attacks.
For those that are unaware of Dymalloy APT, the threat actor was discovered by Dragos researchers while investigating the Dragonfly’s operations. The Dragonfly APT group is allegedly linked to Russian intelligence and it is believed to be responsible for the Havex malware.
The TA17-293A alert published by the DHS in October 2017 suggests a link between Dragonfly attacks with Allanite operations
Learn ICS/SCADA Security Fundamentals
Dragos experts highlighted that Allanite operations present similarities with the Palmetto Fusion campaign associated with Dragonfly by the DHS in July 2017. At the same time, the experts believe the threat actor is different from Dragonfly and Dymalloy.
Another group targeting ICS networks is a North Korea-linked APT tracked as COVELLITE, which has been linked to the Lazarus APT Group. The group is not involved in sabotage operations, it focuses on information gathering and reconnaissance activities. It has been observed targeting networks associated with electric energy in Europe, East Asia, and North America.
The above groups are just some examples of threat actors targeting ICS/SCADA, experts believe that many other organizations are focusing their attention on ICS systems, including cybercrime gangs.