Improper Error Handling Exploitation Case Study
Introduction:
In the earlier articles about Improper error handling, we discussed how these vulnerabilities can occur. and how they can cause security issues. We discussed some improper error handling scenarios that can be used for successful exploitation.
Improper error handling often looks innocent, but it can sometimes lead to rather dangerous vulnerabilities. Apple’s goto fail vulnerability is one classic example of innocent looking error handling code bringing unexpected dangers. The Apple’s goto fail bug was caused due to a single line of insecure code used for validating invalid certificates incorrectly. This resulted in invalid certificates being quietly accepted as valid in apple software.
This article provides a case study of an improper error handling vulnerability using a custom vulnerable web application.
Learn Secure Coding
The target application:
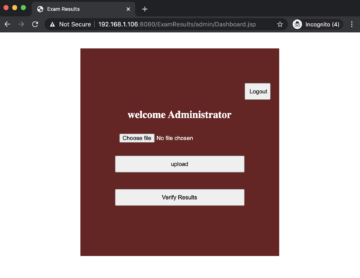
The target application has an admin panel, where the user can login and upload files onto the server as shown below.
This feature is vulnerable to arbitrary file uploads. In any arbitrary file upload vulnerability, successful exploitation depends on the location on the server, where the files being uploaded to. It may not always be straight forward as developers may choose an unpredictable location for storing the uploaded files. So, let us see how the target application has an improper error handling issue, which will lead to disclosure of the path, where uploaded files are being saved.
The attack:
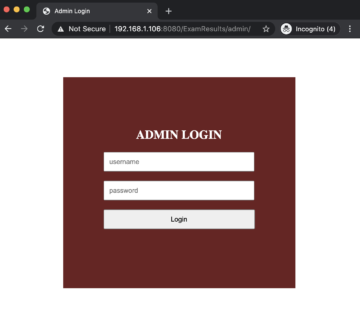
Let us login to the application’s admin panel, which is available at the following URL.
The login page looks as follows.
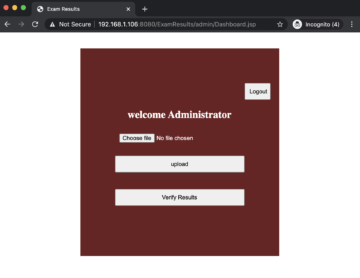
After logging in using the credentials admin:admin, we should see the following dashboard.
The dashboard has an improper error handling issue within the upload feature. The application handles the file uploads properly when there is a file attached, but if there are no files attached, the application responds back with a detailed stack trace.
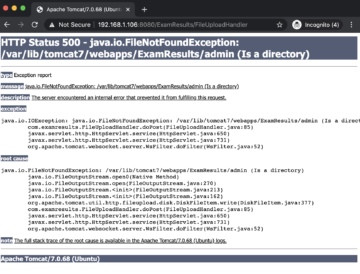
Click the upload button without choosing any file and we should observe the following error message.
This error gives a hint that the application is trying to upload the file into /var/lib/tomcat7/webapps/ExamResults/admin folder, which is the current directory for us. Since the filename is blank, an exception is thrown, which was not handled by the developer.
Learn Secure Coding
Clearly the application did not go through enough negative testing. This means the application was tested to see if the file upload functionality works fine, but there was no testing performed to check what happens if someone clicks the upload button without uploading any files. This issue would not have occurred if there was sufficient negative testing performed. Good error handling mechanisms should be able to handle any feasible set of inputs, while enforcing proper security. Simple error messages should be produced and logged so that their cause, whether an error in the site or a hacking attempt, can be reviewed.
This leaked information may look innocent but it is gold for an attacker, who needs to guess the directory in which the uploaded file is saved.
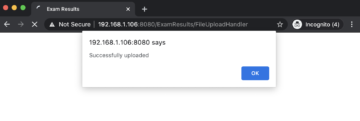
Now, upload a web shell and it should be successfully uploaded. In this case, a jsp webshell named cmd.jsp is uploaded.
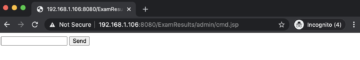
As we can see, the file is successfully uploaded. We can now access the uploaded webshell using the following url.
The following figure shows that the webshell is successfully uploaded and accessible from the current directory.
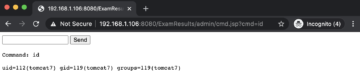
One can execute arbitrary system commands using the uploaded webshell.
As we can observe in the preceding figure, the command id was executed as the user tomcat7. This completes the successful exploitation of a file upload vulnerability by leveraging information disclosure through an improper error handling vulnerability.
Learn Secure Coding
Conclusion:
This article has provided a case study of how Improper error handling can help attackers chain multiple vulnerabilities. We have seen an application vulnerable to arbitrary file uploads, which could then be chained with an information disclosure vulnerability occurred due to improper error handling.The application’s file upload functionality works fine if there is a file uploaded, but an unhandled exception occurs if there is no file uploaded. Clearly, improper error handling vulnerabilities can be dangerous as they can help attackers to perform other dangerous attacks. In the next article of this series, we will cover how developers can prevent Improper error handling issues in their applications.