Why Improper Error Handling Happens
Introduction:
Improper Error Handling is one of the commonly seen issues in software. Web Applications are no different and they are susceptible to improper error handling issues, which can lead to information disclosure or other vulnerabilities. In this article, we will discuss why and how improper error handling happens in web applications with some examples.
Learn Secure Coding
Introduction to error handling
Handling errors is one of the important parts of programming. When programmers write code, they often come across situations where exceptions are expected and they will need to be handled appropriately. Let us consider an example where the application needs to read a file from the disk. The following code can do it.
Scanner scanner = new Scanner(file);
while (scanner.hasNextLine()) {
String content = scanner.nextLine();
System.out.println(content);
}
scanner.close();
As we can notice in the preceding excerpt, the code reads the file properties.txt from the current directory and reads the content from it and prints the content read. What happens if the file doesn't exist on the disk for some reason? It will result in an unhandled exception and the application may crash. This is where the exception needs to be properly handled. The following code snippet shows how this exception can be handled.
File file = new File("properties.txt");
Scanner scanner = new Scanner(file);
while (scanner.hasNextLine()) {
String content = scanner.nextLine();
System.out.println(content);
}
scanner.close();
}
catch (FileNotFoundException e) {
System.out.println("File not found");
e.printStackTrace();
}
This shows how errors can be handled in software.
Introduction to improper error handling
Let us consider a scenario, where these details exceptions are shown to the user who is using the application. Can it cause any problem? Yes. These messages reveal implementation details that should never be revealed. Such details can provide hackers important clues on potential flaws that can exist in the site.
Now, let us consider the following example with an SQL statement being executed.
boolean flag = false;
try {
statement = connection.createStatement();
String query = "SELECT * FROM users where username='"+username+"' AND password='"+password+"'";
resultSet = statement.executeQuery(query);
if(resultSet.next()) {
flag = true;
}
}
catch (SQLException e) {
// TODO Auto-generated catch block
e.printStackTrace();
StringWriter stringWriter = new StringWriter();
PrintWriter printWriter = new PrintWriter(stringWriter);
e.printStackTrace(printWriter);
ServletResponse response = null;
response.setContentType("text/plain");
response.getOutputStream().print(stringWriter.toString());
}
return flag;
}
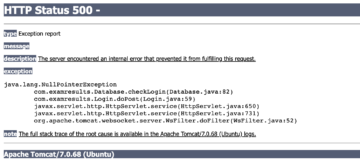
As we can notice in the preceding code snippet, when an SQL exception occurs the exception is properly handled in the code using a catch block. However, the stack trace is sent back to the user leading to potential information disclosure. When a user forces an SQL Exception in this page(by passing a single quote through a user controlled parameter), the stack trace will be displayed to the end user as follows.
Learn Secure Coding
As we can observe, the preceding figure reveals some internal only details. For instance the package name and file names used in the code and the exact line number causing the exception. In addition to these, it can also be seen that tomcat 7.0.68 is running on the target server. This information can be used by an attacker to find exploits associated with the version.
Showing too many details in the error pages is often dangerous and it can be a great source of information for attackers. The following examples, which are often seen from databases show how one can leverage exceptions to derive more details about the target application.
Example 1:
When an application throws this error, we can clearly see that it is using MySQL database. Moreover, this error also represents the possibility of SQL Injection vulnerability.
Example 2:
The above error clearly discloses the information that it is using SQL Server backend.
Example 3:
Fatal error: 1064:You have an error in your SQL syntax; check the manual that corresponds to your
MySQL server version for the right syntax to use near '' LIMIT 1' at line 1 :: SELECT * FROM category_master WHERE status = 1 AND category_id=3' LIMIT 1 in /home/site/public_html/includes/classes/db/mysql/ query_factory.php on line 120
The above error from the application is clearly showing the query executed by the application.This error includes the table name and column name, which can be useful for an attacker while mining the data from the database. Such errors are also often seen in web applications.
Errors from server software:
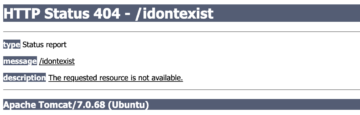
Although many exceptions are to be handled by the developers when writing code there can be scenarios, where the server software with default settings can cause errors, which can lead to information disclosure. The following figure from Apache tomcat shows an error that was returned when a non existing page was accessed.
As we can notice, instead of a custom error page a default error page was shown leading to disclosing the server version.
Inconsistent error messages:
While error messages can often lead to information disclosure, there can be scenarios, where the error messages in itself may not reveal any sensitive information but inconsistency in the error messages being displayed can give an attacker clues about the target application’s behaviour. One such example could be different error messages being shown on a Login page leading to issues like username enumeration.
Learn Secure Coding
Conclusion:
In this article, we have discussed how insecure error handling can happen in applications. We have seen a few examples to better understand how detailed errors may look like. In the next few articles, we will discuss how these improper error handling issues can be exploited and mitigated.