Threat Hunting for File Names as an IoC
Introduction
Just like any good treasure hunt, you need a map or clues to be successful. Threat hunting is no different – Indicators of Compromise (IoC) can be used by threat hunters to track down threats in their environment. File names can be used effectively as IoCs, as they reveal trails of clues that can lead threat hunters to their target. This article will examine the use of file names as an IoC for threat-hunting purposes.
Become a certified threat hunter
Indicators of Compromise
Indicators of Compromise, or IoCs, are pieces of forensic data artifacts that can act as a proverbial breadcrumb trail leading threat hunters to potential threats in their environments. IoCs can often help organizations spot attacker activity in their environments faster so that they can either prevent a breach from happening or stop the attack early on.
How File Names Can be Used as an IoC
File names can be a gold mine for threat hunters regarding clues to attacker activity. Since the earliest days of malware, file names have been manipulated by attackers to allow them entry to networks that they have no business being in. While threat-hunting tactics and technology have changed since the beginning of malware, file names are still viable IoCs.
File Extensions
File extensions are one of the easiest ways that attackers can use file names to help them launch and manage attacks. It is common knowledge among information security professionals, and well-informed basic users that files found online and in unsolicited emails containing a .exe extension should not be opened. These files are frequently malware, and no one wants to install that.
However, .exe files are one part of the spectrum of file extensions that are used to install malware covertly. Other notable file extensions to look out for include .bat, .cmd, .com, .lnk, .pif, .vb, .scr and .wsh just to name a few. Other extensions are used in specific systems: systems that have Oracle’s Java installed will have to steer clear of .jar files, as they can launch malicious Java programs.
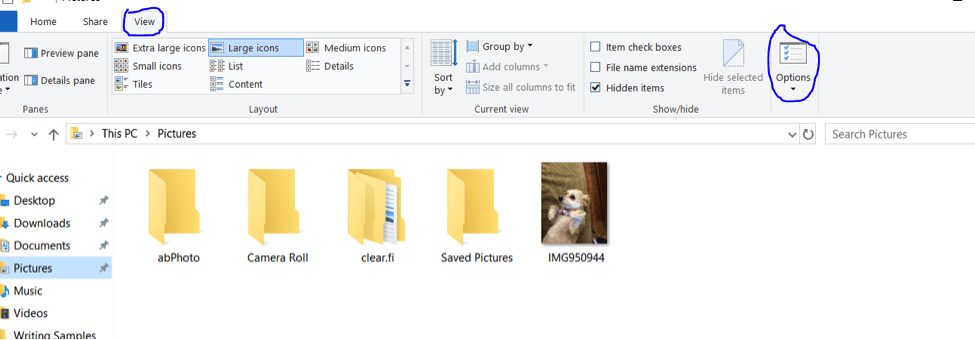
With that said, there is a major problem here – the default setting in Windows is to hide file extensions. This can have a significant impact on user activity and is an asset that attackers can exploit. For example, a file named photo.jpg may actually be photo.jpg.exe, which could launch malware once it is double-clicked. This kind of attack is called a filename spoof. If you think this is the case in your threat situation, you can change this default setting via User Account Control and prevent that from happening going forward:
- Within Windows Explorer, click the Organize button and click on the View tab to select Options:
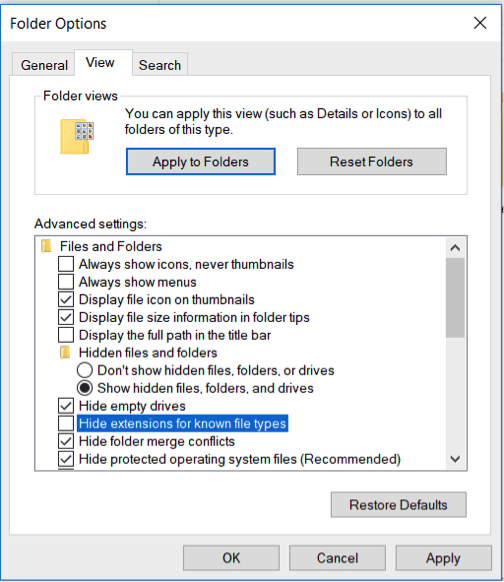
- You will be presented with a Folder Options window. Uncheck “Hide extensions for known file types,” click Apply and OK.
From this point forward, you will no longer be at the whim of attackers because of Microsoft’s bad planning. If you happen to have a file on your system with a hidden file extension, the file will look like this:
Left to Right Override
Another filename-related method that attackers use is called Left to Right Override. Also called the Unitrix exploit, this method takes advantage of Unicode character U+202E which allows the Hebrew and Arabic text to be read in their native right to left orientation. This modified text display allows for the characters in file names to be presented in that way as well.

What this does is make a file name look like “MyJamRCS.mp3” but in reality, the file name is actually “MyJam[U+202e] 3 pm.SCR”. The special character [U+202e] makes the file extension be read in reverse and conceals the extension .SCR, which is an executable that could be hiding malware.
You can evade this type of attack by detecting this reversed extension with a simple view change within your Windows 8 or Windows 10 system. First, download the file to a folder – your download folder will work just fine. Then, change the “Change your view” ruler setting to “Content.” With this setting changed you can see that these files are not .jpg and .pdf but rather applications that are probably malware.
 If you detect this in your environment, do not double-click the file and delete it. It always pays to know the full name of a file. It should be noted that those still using Windows XP will always see the true name of the file as XP does not allow for hidden file types the way that other versions of Windows do, but XP users today are probably few and far between.
If you detect this in your environment, do not double-click the file and delete it. It always pays to know the full name of a file. It should be noted that those still using Windows XP will always see the true name of the file as XP does not allow for hidden file types the way that other versions of Windows do, but XP users today are probably few and far between.
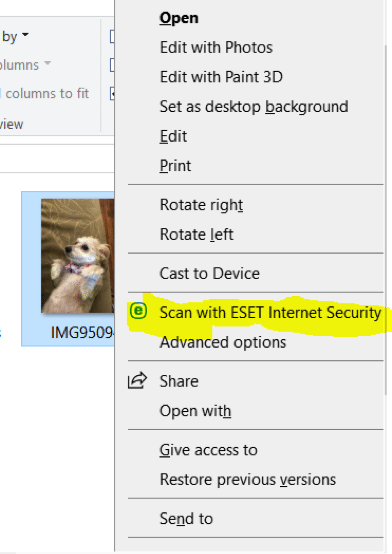
You may find that you have files with suspect file names that you do not know how to detect for sure if they are not harboring malware. If you are at all suspicious, simply scan the file with your antivirus software. Any organization worth its salt from an information security perspective will have an antivirus solution deployed in their environment than can handle this task.
In this example, I am using ESET Endpoint Antivirus. Simply right-click on the file with the suspect file name. Select “Scan with ESET Internet Security” and if the file is an executable, your antivirus solution will let you know.
Sources
Top 15 Indicators Of Compromise, Dark Reading
How Hackers Can Disguise Malicious Programs With Fake Files Extensions, How-To Geek
Become a certified threat hunter
7 sneak attacks used by today’s most devious hackers, InfoWorld