Threat hunting with Cymon API
Introduction
In this article, we’ll discuss mock intrusion attempts on our systems and show you how to make use of Cymon API to query important information that you can use in an effective threat hunt. In our case, we’ll demonstrate how we halted progression of the attack, effectively stopping it in its tracks.
It should be noted that although the discussed scenarios are entirely fictional, they are very possible in today’s world of increasing threats.
Become a certified threat hunter
Introduction to the Cymon API
Cymon is the largest tracker of malware, phishing, botnets, spam and more. It is maintained by the private security company eSentire. Cymon allows you to:
- Search threat reports for free. Reports could include reported IPs, domains, binary hashes and so much more
- Collaborate with other researchers. Cymon allows you to create your own feed and invite users to contribute IoC data or submit reports to other feeds
- Export feeds. You are able to export your own feeds or public ones
- Integrate with existing tools. Cymon allows you to integrate with existing tools in order to deliver on threat intelligence
The above functions can be performed directly on the Cymon app or by interacting with the provided API. It should be noted that the first version of Cymon will be discontinued on April 30th, 2019, paving the way for the improved second version.
Intrusion detection and threat hunting with Cymon API
Before we can begin using the Cymon API, we are required to register for an account through Cymon. You will also need to use your credentials to create a session here in order to access the API. The steps to be followed are as follows:
- Click on “Create Session”
- On the left panel, click on “Switch to Console”
- We click on “body” and manually feed in our credentials as shown below:
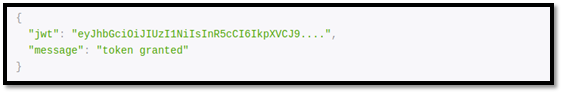
- We receive a JWT token as shown below. We need this in order to interact with some crucial parts of the API.
On registering, we are issued a JSON Web token that will be used to authenticate our session. For first timers, familiarizing with the API is important. You can play with sample requests to understand how the API functions here. You can make some mock calls on the mock server or make actual real ones on the production server.
Let’s discuss some mock intrusion scenarios and made use of the Cymon API to make sense of certain aspects of the attack.
Intrusion Attempt 1 — Loki Ransomware Attack
On February 21st, 2019, we detected an email with a suspicious attachment discussing an upcoming cybersecurity and mobile money transactions event in western Germany. We discovered that the email had been sent to three employees within our organization and that they had received similar emails in the past month, although previous attempts were unsuccessful. Our security team determined that the suspicious attachment named 01019-CS-EG.pdf had malicious code which attempted to exploit the famous CVE-2018-8495 vulnerability.
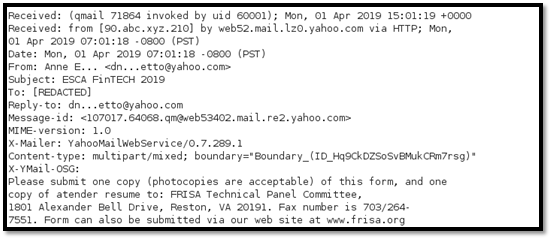
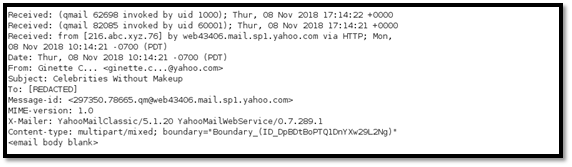
The email header was extracted and is presented below.
Our researchers discovered that the malicious PDF concealed a Portable Executable (PE) file which was used to install a backdoor to the target system. The attackers were intelligent enough to encrypt the PE and include shellcode within the malicious PDF. On opening the PDF, the shellcode contained within it would execute, decrypting the PE and storing it at C:UsersUserAppDataLocalTemp before executing it to launch the attack.
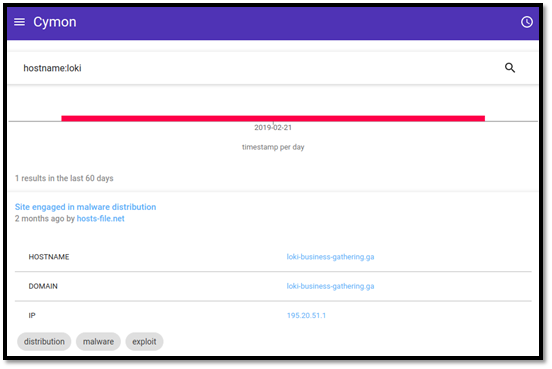
Our malware research team discovered that the malware made attempts to download variants of the malware from the IP address 195.20.51.1. We resolved the IP address to the domain loki-business-gathering.ga and discovered from Cymon that this domain was actively involved in malware distribution. The command below was used to interact with Cymon for more information.
curl 'https://api.cymon.io/v2/ioc/search/domain/loki-business-gathering.ga' | jq '.'
The following is the screenshot we obtained from running the command.
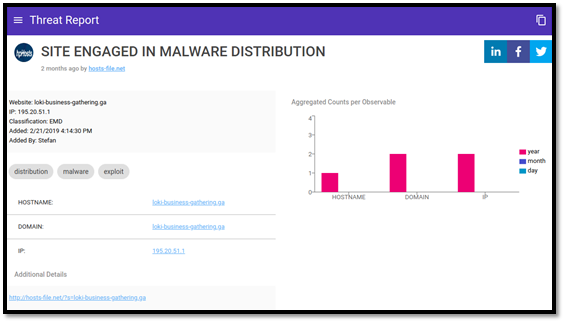
We also visited the Cymon app to find more statistics on the malware. The most recently reported attacks could be viewed by querying the discovered hostname (loki-business-gathering.ga) on Cymon here. We can see that there was a reported Loki campaign employing the same attack vector two months ago. The screenshot below shows this.
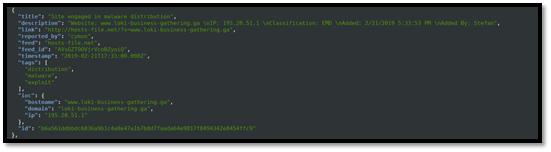
To view more information on the report above, we simply click on “Site engaged in malware distribution.” Doing so presents us with the screenshot below, giving more information such as a graph representation and any additional meaningful information.
From the information above, we understood that we were dealing with a potential ransomware attack. We quickly blacklisted any traffic coming from or going to that domain from within our internal network. The fast response of our IR team allowed us to thwart this attack before the adversary was able to complete their objectives.
Two days later, we began noticing suspicious activities targeting our VoIP servers. Incident Response showed that the source of the suspicious traffic was the IP address 46.148.18.162.
Using Cymon’s API, we were able to query for more information from this source. We used the following curl command to achieve our results:
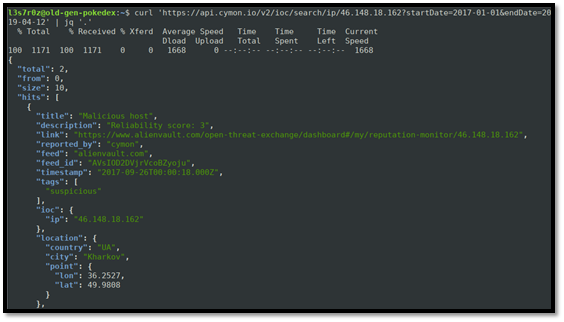
curl 'https://api.cymon.io/v2/ioc/search/ip/46.148.18.162?startDate=2017-01-01&endDate=2019-04-12' | jq '.'
The screenshot below shows the output:
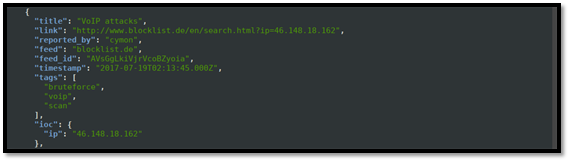
From the screenshot, we can see that the attack seems to originate from Kharkov in Ukraine. Cymon also gives us the longitude and latitude of the city. We can see below that the report identifies the IP to be notorious for VoIP attacks as well:
The table below summarizes the key indicators according to the different phases arising from the intrusion attempt.
Intrusion Attempt 2 — WannaCryptor Ransomware Attack
On November 8th, 2018, we noticed an attempt to breach our internal network. An employee received an email containing a PowerPoint attachment that attempted to exploit two previously known vulnerabilities — CVE-2017-0143 and CVE-2016-0092. We discovered that CVE-2016-0092 attempted to exploit a Windows OLE memory remote code execution vulnerability and CVE-2017-0143 attempted to exploit the Windows SMB remote code execution vulnerability.
The captured email header details are as shown below.
A timely course of action allowed us to thwart this attack using available network defenses. However, had this attack been targeted at employee’s personal emails, then their personal devices would have been compromised.
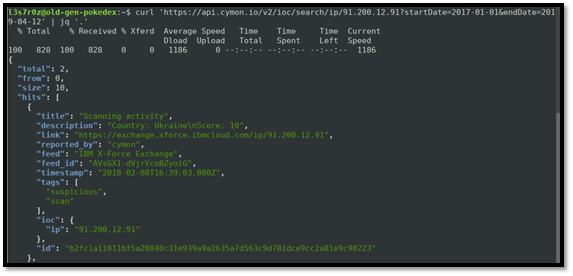
After the failed attack, we noticed numerous scan activities against our web infrastructure from the IP address 91.200.12.91. We decided to query Cymon using the API for any related events as shown below:
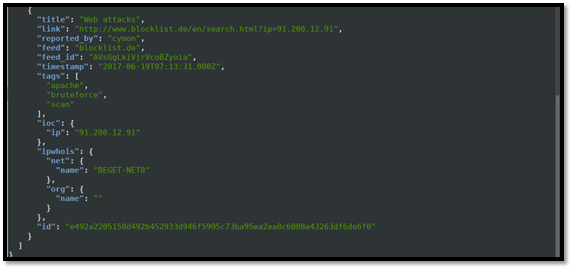
The IP address is reported to be actively engaged in scanning activities and is hosted in (or spoofed to appear to be from) Ukraine, as can be seen above. The screenshot below also shows the specific activities that the controllers of the server seem to be engaged in. As can be seen, the server targets Apache Web servers and attempts various brute-force attacks against them.
We decided to blacklist the IP address above to prevent any traffic towards it from the internal network and reconfigured our VoIP infrastructure by redesigning access to now require VPN authentication.
The table below summarizes the key indicators according to the different phases arising from the intrusion attempt.
Conclusion
Cymon is a useful resource that allows for the collection of information related to various threats. This information can be especially helpful when dealing with large numbers of threats, with the need to identify malware families.
The Cymon API also allows for integration with various tools that can effectively increase the effectiveness of threat-hunting teams. Teams can contribute by sharing feeds and obtaining crucial information from the hundreds of available feeds.
Become a certified threat hunter
Sources
- Cymon API v2, eSentire
- cymon-python, GitHub
- CVE-2018-8495 Detail, National Vulnerability Database
- Microsoft Edge Remote Code Execution, Leucosite