All about SamSam Ransomware
Ransomware: Perhaps Today's No.1 Security Threat
Threatening and Risky for you and fruitful for hackers, ransomware has taken over as today's no. 1 security threat. Attacks related to ransomware have increased over the past few years and will continue as it gets more destructive as the time passes. The question arises what is ransomware and why it is so dangerous? Ransomware is malicious software which encrypts files on your computer or completely locks you out. It is done by cybercriminals who demand a ransom (sometimes in bitcoins), an assertion that, if you pay, you will receive the decryption key to recover your infected files.
A Brief History
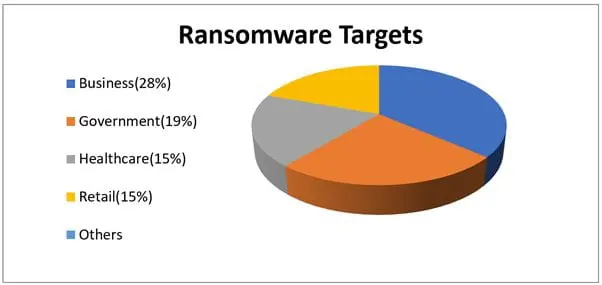
The first-time ransomware came into being or you can say the first attack occurred in 1989 when evolutionary biologist Joseph Popp infected floppy disks with the AIDS Trojan and distributed them to fellow researchers. The malware did not start immediately, but it waited till PC was booted 90 times. Then, it locked all system files and asked the users to pay $190 to get the locked files back. Fortunately, experts came up with tools to remove the malware and decrypt infected files. Soon the question aroused that is ransomware a virus? Nope. Viruses are different from ransomware, the virus infects your files or software, and it can replicate, but ransomware scrabbles your files to make them unusable, then demands you must pay up as per asked. They can be deleted with antivirus, but if your files are encrypted chances are you'll never get them back. After this, ransomware attacks continued, and still, we see they happen as recently SAMSAM ransomware attack took place, let us see what it was all about with the help of the following pie chart.
Hands-on threat intel training
About SAMSAM
The SamSam group has been notorious since 2015, causing it first major scene of mass chaos in 2016(several infected hospitals in the USA), and starting to increase the cost of their ransom in 2017 regularly. Recently in USA (Colorado and Atlanta) have both had run-ins with SamSam as you may have seen from ongoing news coverage. You can trace SamSam's first appearance back to January 2018. There's "persistent," and then there's SamSam. MedStar hospital was in worst position after this ransomware attack because it was required to pay 45 bitcoins or $18,500 in exchange for the encrypted data. Sometimes it's often that you have backups same was in the case of hospital what it had, and at last, that was able to manage the removal of SamSam, and hence cyber criminals did not receive the money. Not only this SamSam ransomware's main targets are organizations and businesses. FBI has already warned the corporations and businesses to increase their cybersecurity.
SamSam ransomware is a type of infection used in targeted attacks, often deployed using a wide range of exploits or brute-force tactics (trial and error method). Based on target's activity with the infection, it was observed that attacks were made on targets via vulnerable JBoss host servers during the attacks which took place mainly in 2017. In 2018, SamSam used the vulnerabilities present in remote desktop protocols (RDP), file transfer protocol (FTP) servers and Java-based web servers to gain control of the victims' network or brute force against weak passwords to obtain an initial foothold. From there, the ransomware "fun and games" begin for the makers of the ransomware. For the targets, it's chaos.
The ransom note is quite interesting, giving the option of randomly-selected file encryption. They'll also unlock one file for free as a token of trust that they will give your files back after payment.
What actually happens?
All your files get encrypted with RSA-2048 encryption.
RSA(Rivest-Shamir-Adlemen) is quite a slow algorithm, and because of this, it is less used to encrypt the user data. RSA passes encrypted keys for symmetric key cryptography which can perform bulk encryption-decryption operations at a very good speed.
How to recover?
RSA is a mathematical algorithm based upon Asymmetric Cryptography. Two keys are involved: The Public Key and the Private Key. The former is used for encryption, and the latter is for decryption. So, you need the private key to recover your files. It's not possible to recover your files without the private key.
How is a private key issued?
You can obtain your private key only if the attacker's given conditions are satisfied. As we know that ransomware is all about ransom, so it is, as we saw above that once your files are hijacked they will get opened by the private key which is availed after following the certain conditions put by the attacker. They can be like: You must send us 10 Bitcoins for each affected PC or 40 Bitcoins to receive all private keys for all affected PCs. Then they will then send the decryption key.
SamSam: Still it exists, yes it does
This ransomware has already racked up around $850,000 in profit and shows no sign of slowing down. Consider that their estimated $850k profit is still nowhere near the cost of recovery for the Atlanta City alone, and then consider how much the total cost of clean has been thus far.
SamSam won't leave anytime soon but can be there for long and other infections too that are waiting to strike. It is just a moment of inattentiveness or ignorance, and you could be faced with some difficult decisions indeed.
By the way, there is no such attack which can affect you badly until you have listed
COUNTERMEASURES:
- Immediately take the infected system offline from the Network Infrastructure so that the malware will not further spread itself.
- Determine the affected area as some sensitive data that may require additional reporting and mitigation measures.
- Determine if the decryptor is available. Online resources such as No more ransom! Can help.
- Restore files from regularly maintained backups.










