BendyBear: A shellcode attack used for cyberespionage
BendyBear is a sophisticated and stealthy cyberespionage tool.
This malware was developed by BlackTech, a cyberespionage group linked by threat researchers to the Chinese government. According to Unit 42 researchers, there is no information about the infection vector used to deploy the shellcode on target systems and the payload is well-engineered and difficult to detect.
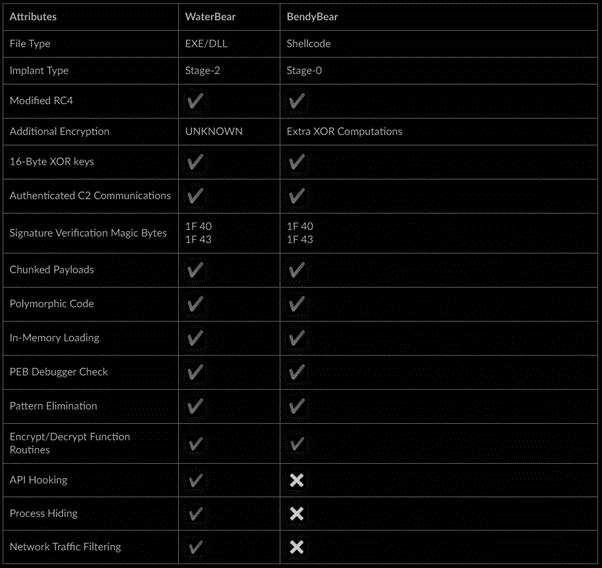
BendyBear malware has blocks of code similar to the WaterBear malware family (active since 2009), and often deployed against East Asian governments such as Japan, Taiwan and Hong Kong. Because of this, the BendyBear shellcode seems to come from the same source of WaterBear and is potentially linked to the BackTech APT group.
Hands-on threat intel training
Figure 1 below compares these pieces of malware and highlights the most important details and their similarities.
Figure 1: BendyBear vs WaterBear.
BendyBear key points
BendyBear is a sophisticated shellcode that implements a group of features to make its detection and analysis difficult and keep it off the radar. A summary of the most important details of this shellcode is described below.
Obfuscation layer and anti-analysis
Once executed, the shellcode checks the target environment for signs of debuffing to prevent observation of important details or behaviors during run-time. The shellcode begins by locating the target’s process environment block (PEB) to check if it’s currently being debugged.
After that, the Kernel32.dll base address is loaded to internally resolve any dependency files required by the shellcode to run. The modules loaded by the shellcode are the following:
Kernel32.dll
Msvcrt.dll
User32.dll
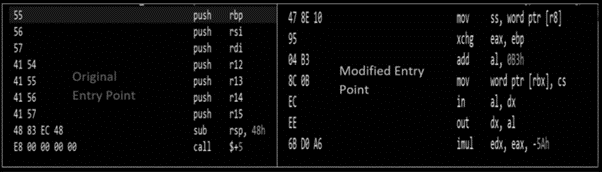
Ws2_32.dllBendyBear uses polymorphic code and its footprint changes during the code execution to avoid forensics and memory analysis and thus evading signature. Figure 2 below shows an example of the shellcode main entry point before and during runtime execution.
Figure 2: Modified shellcode runtime example.
Windows registry and malware config
BendyBear leverages the existing Windows registry key QuickEdit, which is enabled by default in Windows 10, to store configuration data used during the infection chain.
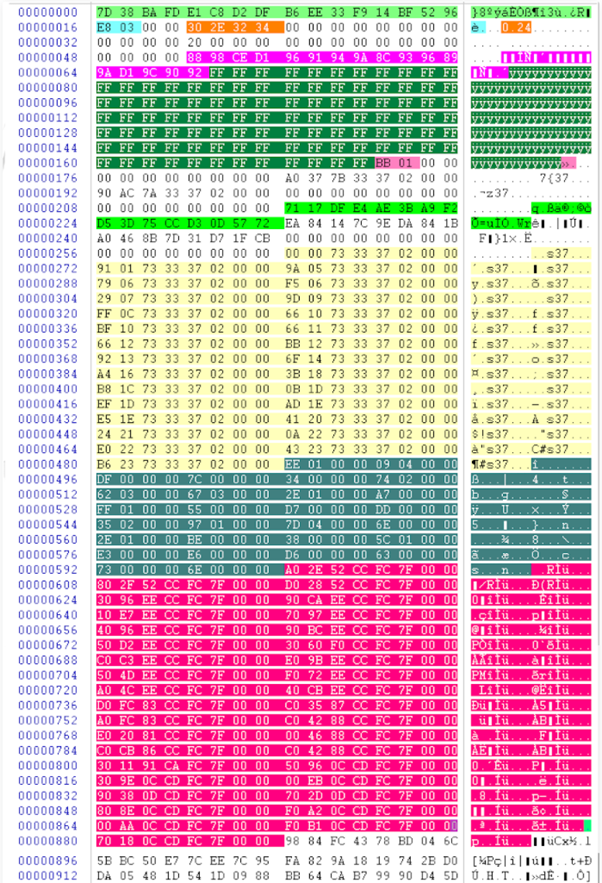
After storing and reading some details from the registry, it then decrypts its internal configuration structure, which is 1,152 bytes (see Figure 3).
Figure 3: BendyBear shellcode configuration structure.
Command and control communication
Before communicating with the C2 server, the shellcode clears the host’s DNS cache every time it tries to connect. With this tactic in place, the C2 IP address is resolved each connection, allowing the C2 IP address to be changed whenever operators find it necessary.
To accomplish this task, the shellcode uses the following module and call:
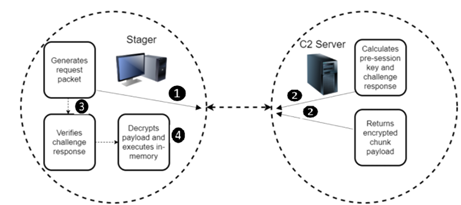
After that, the communication starts. The stager (shellcode) sends a challenge request (1) to the C2 server and waits for a response. When the connection from C2 is received and decrypted, the shellcode checks for magic values of signature bytes at specific offsets to validate if the traffic and post-payloads are legitimate. If the check fails, the connection is immediately aborted.
Figure 4: BendyBear communication diagram.
The shellcode generates unique session keys for each connection with the C2 server and obfuscates the connection protocol by connecting the C2 using the 443 TCP port to make detection difficult. In this sense, malicious traffic is blended with normal SSL network traffic.
The payloads are transmitted using modified RC4-encrypted chunks. With this technique in place, the shellcode turns the traffic decryption as a single RC4 key will not decrypt the entire payload.
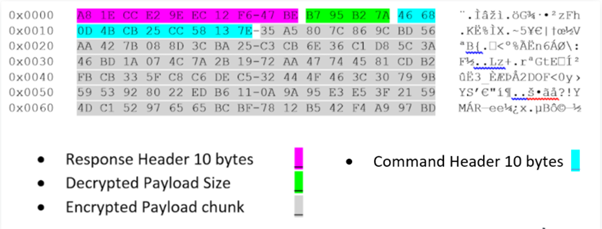
Figure 5 shows an example of one payload chunk that is sent from C2 to the stager (shellcode running).
Figure 5: Encrypted payload header and data.
Being aware of BendyBear
BendyBear is a specially crafted payload with similarities to the WaterBear malware family. The group behind this piece of malware developed advanced features that are not found in common shellcode, using anti-analysis techniques and signature block verification (a clear signal that criminals are focused on making it a stealthy and detection-evasion malware). The shellcode uses custom and crafted cryptographic routines and byte manipulations that suggest a high level of knowledge on the part of the authors behind this piece of malware.
Sources:
BendyBe HYPERLINK "https://unit42.paloaltonetworks.com/bendybear-shellcode-blacktech/"ar research, Unit 42
Waterbear malware, ZDNet