DragonFly 2.0: The Alleged Nation-State Actor Hits the Energy Sector Again
Security experts at Symantec have uncovered a hacking campaign against companies in the energy industry that appears to be an activity linked to the infamous Dragonfly group.
"The energy sector in Europe and North America is being targeted by a new wave of cyber-attacks that could provide attackers with the means to severely disrupt affected operations. The group behind these attacks is known as Dragonfly. The group has been in operation since at least 2011 but has re-emerged over the past two years from a quiet period following exposure by Symantec and a number of other researchers in 2014. This "Dragonfly 2.0" campaign, which appears to have begun in late 2015, shares tactics and tools used in earlier attacks by the group." reads the analysis published by Symantec.
The Dragonfly group was first spotted by Symantec in 2011 when it targeted defense and aviation companies in the US and Canada. Only in a second phase in early 2013, Dragonfly has focused its effort on US and European energy firms.
The group was tracked by other security companies such as Kaspersky and CrowdStrike, this latter published a detailed report on the group in 2014, the document reference it as Energetic Bear and links to threat actor to Russia.
"In mid-May 2014, a malicious document (MD5 hash 16b4a8bcaf8c20b0786c97de1a943dc5) exploiting CVE-2014-1761 was identified, which is associated with an adversary tracked by CrowdStrike under the name ENERGETIC BEAR. This exploit document dropped the Havex RAT. ENERGETIC BEAR is an actor with a Russian nexus that has been observed to target a variety of victims with a particular focus on the energy sector." States the analysis published by the security firm CrowdStrike.
The US intelligence also believes the group is linked to the Kremlin, according to the JAR report published by the US Department of Homeland Security, Dragonfly was Russian APT actor working for the Government.
Dragonfly gang conducted a cyber espionage campaign against energy grid operators, major electricity generation firms, petroleum pipeline operators, and energy industry industrial equipment providers.
In 2014, security experts at Symantec uncovered a new campaign targeting organizations located in the US, Italy, France, Spain, Germany, Turkey, and Poland.
After the report went public in 2014, the Dragonfly group went dark and appeared again in December 2015 when it launched cyber-attacks on Turkish energy companies that were also targeted during 2016.
Now the malware experts from Symantec reported Dragonfly targeted energy companies in Europe and the US, but with a substantial difference compared with past campaigns, this time the alleged state-sponsored hackers aimed to control or even sabotage operational systems at energy facilities.
"The Dragonfly group appears to be interested in both learning how energy facilities operate and also gaining access to operational systems themselves, to the extent that the group now potentially can sabotage or gain control of these systems should it decide to do so," continues the report published by Symantec.
According to Symantec, the Dragonfly 2.0 campaign begun in late 2015, threat actors used same TTPs of previous campaigns.
"The energy sector in Europe and North America is being targeted by a new wave of cyber-attacks that could provide attackers with the means to severely disrupt affected operations. The group behind these attacks is known as Dragonfly." reads the analysis published by Symantec. The group has been in operation since at least 2011 but has re-emerged over the past two years from a quiet period following exposure by Symantec and a number of other researchers in 2014. This "Dragonfly 2.0" campaign, which appears to have begun in late 2015, shares tactics and tools used in earlier campaigns by the group."
In the following table are reported the links between the earlier Dragonfly campaigns and the current one.
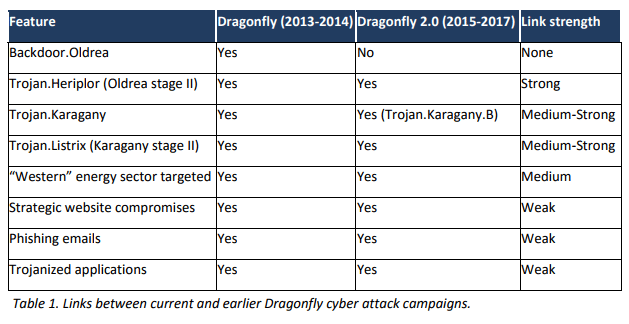
Figure 1 - links between Dragonfly campaigns (Source Symantec Report)
Malware experts discovered many similarities between earlier Dragonfly campaigns and the recent wave of cyber-attacks.
While the first Dragonfly campaigns appear to have been a more reconnaissance phase, the Dragonfly 2.0 campaign seems to have destructive purposes.
The energy sector has become a privileged target for state-sponsored hackers over the last years due to the number of critical infrastructures operated by companies in the industry. Most clamorous cases are the power outages caused in Ukraine in 2015 and 2016 that were attributed to Russian APT groups.
Symantec believes the Dragonfly group is very advanced; it operates to make hard the attribution of the attacks. Below some of the tactics employed by the hackers:
- The attackers used more generally available malware and "living off the land" tools, such as administration tools like PowerShell, PsExec, and Bitsadmin, which may be part of a strategy to make attribution more difficult. The Phishery toolkit became available on Github in 2016, and a tool used by the group—Screenutil—also appears to use some code from CodeProject.
- The attackers also did not use any zero days. As with the group's use of publicly available tools, this could be an attempt to thwart attribution deliberately, or it could indicate a lack of resources.
- Some code strings in the malware were in Russian. However, some were also in French, which indicates that one of these languages may be a false flag.
Symantec reports most attackers' activity in organizations in the US, Turkey, and Switzerland.

Figure 2 - DragonFly (Symantec Report)
Dragonfly 2.0 State-sponsored hackers demonstrated over the years the ability to employ different attack methods, the group leveraged on a broad range of attack vectors, from spear phishing messages to watering holes.
In the first attacks spotted by Symantec in December 2015, hackers used spear phishing messages disguised as an invitation to a New Year's Eve party.
The hackers continued to use spear phishing emails in the campaigns conducted during 2016 and 2017, according to Symantec they were specifically designed with content related to the energy sector.
Phishing emails spotted by Symantec were created with the Phishery toolkit in the attempt to steal victims' credentials via a template injection attack.
The attackers also used watering hole attacks to harvest network credentials; they targeted websites likely to be visited by personnel involved in the energy sector.
Symantec reported that at least in one case, the watering hole attack was used to deliver the Goodor backdoor via PowerShell 11 days later.
"Symantec also has evidence to suggest that files masquerading as Flash updates may be used to install malicious backdoors onto target networks—perhaps by using social engineering to convince a victim they needed to download an update for their Flash player. Shortly after visiting specific URLs, a file named "install_flash_player.exe" was seen on victim computers, followed shortly by the Trojan.Karagany.B backdoor." continues the analysis.
Symantec and most of the experts in the security and intelligence field believe this is a military operation that aims to assess the level of security implemented by critical Western infrastructure.
"I think preparation for a potential attack is what we're seeing. And whoever's doing this, presumably the Russians, want us to know. People in the intelligence business always say that when the Russians are found, it's because they want to be found." said Joel Brenner, former head of U.S. counterintelligence and Inspector General of the National Security, now a senior research fellow at the Massachusetts Institute of Technology.
Symantec believes it might have been a "proof of concept" attack; a foreign government simply aims to demonstrate that it could cause severe damage to a critical infrastructure.
The Department of Homeland Security is aware of the Symantec report and is reviewing the document.
"At this time, there is no indication of a threat to public safety," said the DHS spokesperson Scott McConnell. "We continue to coordinate with government and private sector partners to look into this activity and, through our National Cybersecurity and Communications Integration Center, we have released multiple information products to the critical infrastructure community to provide detection and response recommendations to help them secure their networks."
The North American Electric Reliability Corporation is also investigating the cyber-attacks and is sharing information with industry and government partners, but downplayed the imminent risks for the bulk power system.
"At this time, there are no impacts on the operation or reliability of the bulk power system in North America. NERC continues to monitor potential cyber security risks to reliability and shares information with security stakeholders on emerging and evolving threats," said Bill Lawrence, director of NERC's Electricity Information Sharing and Analysis Center.
The good news is that private firms in the energy industry are taking this threat very seriously and are ready to improve their level of security to prevent further sabotage operations.
References
http://securityaffairs.co/wordpress/62782/hacking/dragonfly-2-0-campaigns.html
http://securityaffairs.co/wordpress/26273/cyber-crime/dragonfly-gang-energy-industry.html
https://www.crowdstrike.com/blog/cve-2014-1761-alley-compromise/
http://securityaffairs.co/wordpress/27224/cyber-crime/kaspersky-report-energetic-bear.html
http://securityaffairs.co/wordpress/54900/hacking/fbi-dhs-jar-report.html
Hands-on threat intel training










