GhostNet - Part I
Introduction
Several years after the revelation of GhostNet, a massive case of cyber exploitation directed mostly against the Tibetan community, in terms of originality, this contribution appears as an interesting survey of the events happened pre and post that period.
Hands-on threat intel training
In GhostNet part I, the reader can learn more about the process of investigation —researchers and investigators responsible for bringing this case to light, affected parties, attack vector, methods employed, technical data resulting from all the efforts, etc. The existing pieces of technical evidence are summarized at the end, which, in turn, would serve as an unostentatious foreword of the supervening part II.
In GhostNet part II, which is to be published separately, the main plot revolves around the reactions and allegations/denials of security experts, parties involved, politicians, and so on, with respect to the news of this cyber-exploitation network that have made the headlines. In addition, there is a subsection examining the legal side of the GhostNet.
It might be useful for the readers to understand more about the Chinese-Tibetan relationships in historical perspective. Briefly, after a Chinese invasion that had begun in 1950, the Tibetan spiritual leader and head of government, the Dalai Lama, fled to India in 1959 from where he initiated a campaign for Tibetan independence.
Discovery and Researchers of GhostNet
In the spring of 2008, after a series of strange incidents with foreign diplomats and dignitaries canceling their appointments with the Dalai Lama, allegedly pressured by the Chinese government, the people working for the Tibetan spiritual leader started to suspect cyber-exploitation as a possible explanation. They decided to contact experts in the field who could carry out a full-scale investigation (Nagaraja & Anderson, 2009).
The case was discovered and received its name after a ten-month investigation led by the Information Warfare Monitor (IWM). It includes among its staff researchers from Citizen Lab, Munk Centre for International Studies at the University of Toronto, and small contingent from Secdev Group. Researchers from the University of Cambridge had a meaningful participation as well in Dharamsala, the headquarters of the Tibetan government-in-Exile. As a result of the uncovered cyber-exploitation network, several reports were issued referring to the subject extensively (IWM report and University of Cambridge report).
Between June 2008 and March 2009, the IWM conducted a thorough two-phase investigation based on the Tibetan community concerns that their cyber-security had been compromised, as they believed, by a Chinese cyber-exploitation.
The first phase investigation was conducted a field-based research at the Office of His Holiness the Dalai Lama (OHHDL), the facilities belonging to the Tibetan Government-in-Exile, and some Tibetan NGOs, all located in India. The Tibetan missions in New York, London, and Brussels were also inspected. The fieldwork from all sites revealed the existence of malware that had penetrated the Tibetan computer systems (Information Warfare, 2009).
The second phase encompassed a number of different analytical methods, which we are going to examine in detail later on. They led to the discovery of a complex malware-based cyber-exploitation network dubbed GhostNet.
Short Summary of the Key Findings
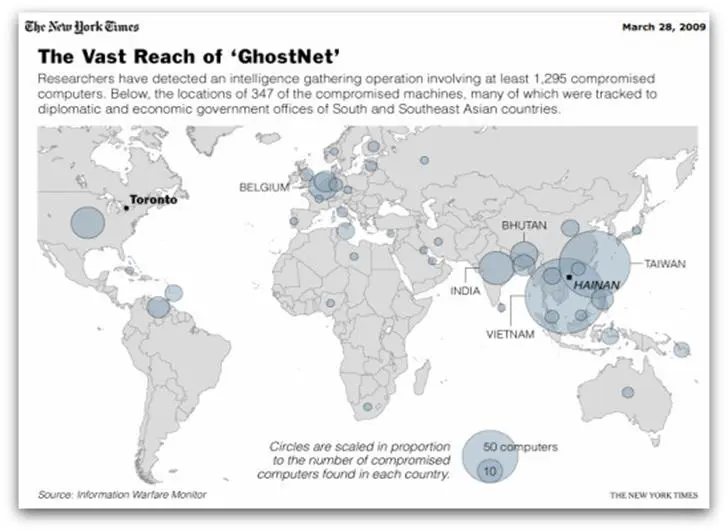
Records, samples, data, and analysis serve as evidence for the existence of the wide-ranging cyber-exploitation network GhostNet, contaminating minimum 1,295 computers in 103 countries. According to the IWM research, 30% of the targeted objects are to be evaluated as high value, as far as the political, diplomatic, economic, and military criteria are concerned. The following spots fall into range of the high-value targets' list:
- Ministries of foreign affairs of Bangladesh, Barbados, Bhutan, Brunei, Indonesia, Iran, Latvia, Philippines
- Embassies of Cyprus, Germany, India, Indonesia, Malta, Pakistan, Portugal, Romania, South Korea, Taiwan, Thailand
- The Asian Development Bank, the ASEAN (Association of Southeast Asian Nations) Secretariat, SAARC (South Asian Association for Regional Cooperation).
- An unclassified NATO headquarters computer (Information Warfare, 2009).
Despite this broad list of targets spanning half the globe, the reports stressed that the most affected victims of GhostNet cyber-exploitation are the Tibetan community, including OHHDL. In fact, the reports speak of documented evidence of penetration of the computer systems used by the Tibetans that have some sensitive, and even secret, information at their disposal.
Additionally, the researchers studied in breadth the modus operandi of the GhostNet —attack vectors, targeting and delivery mechanism, data exfiltration, and the skeleton of the cyber exploitation. Again, this information as a whole reveals covert, sophisticated, and almost impossible to detect cyber-exploitation network, which allows the intruders virtually unrestricted access to the affected computer systems.
Targeted malware — previous research
As early as September 2002, there were reports from Tibetan groups claiming that they were targeted with malware coming from Chinese servers. The attacks in question were massive, directed against diverse groups and NGOs such as human rights institutions, exile or labor groups, non-state actors, trade unions, scholars, writers, intellectuals, and diaspora. The technical samples gathered since that period were analyzed and identified control servers that may have directly or obliquely been involved in at least 50 incidents (Information Warfare, 2009).
According to rumors, Chinese hackers have persistently performed denial of service (DoS) cyber-attacks against pro-Tibetan administration and activists' websites. Nevertheless, with its sophisticated nature and far-reaching octopus tentacles, the GhostNet is a product of another level, is far more advanced, and is child of the new cutting edge technology (Michael, 2010).
The GhostNet attack vector spreads infection through social means. Carefully written emails, with contextually relevant content, are sent to a target marked in advance. Usually, the massages prompt the receiver to open corrupt attachments or malicious links. This technique is known as "social engineering."
Most often, the documents are files that have malicious payload that exploits Microsoft Office or Adobe Acrobat Reader vulnerabilities. From the recipient's perspective, the document will open and appear normal. However, in some instances the user may notice something that can raise his suspicion "since exploits usually crash Microsoft Word or Adobe Acrobat Reader before relauching the application with a real file. That leads to a quick screen flash, and sometimes ends up putting the name of the exploit file in Word's recovered document's panes (Singel, 2008, par. 24)."
Not long before the GhostNet, pro-Tibet organizations and the Pentagon have acknowledged similar breaches leveraging social engineering techniques. The chief researcher for software security vendor F-Secure Mikko Hyppönen was one of the first to link the cyber exploitation cases "to a series of patches that Microsoft pushed out without explanation (Singel, 2008, par. 4)." The patches in question emerged in 2006 and 2007, aimed at remediating security holes in Microsoft Office that have been taken advantage of by China —at least for those willing to judge solely by the place of origin.
The researchers from Cambridge University consider that in the GhostNet case, the break-in occurred after "one monk clicked on an infected attachment, giving the attacker the foothold (Nagaraja & Anderson, 2009, p.6). Given the fact that the monks taking care of the administrative dealings in OHHDL were also engaged in various online activities such as participating in discussion websites and blogs, this theory seems very plausible: "a passive observer could easily note their names, their interests and the names of people with whom they interacted (Nagaraja & Anderson, 2009, p.6)."
Keeping this in mind, the researchers further assess that "the attackers probably used publicly-accessible mailing-list archives to construct the social-malware emails that they sent to their first targets (Nagaraja & Anderson, 2009, p.6). On the other hand, the researchers cannot exclude completely scenarios such as visiting bogus web sites containing drive-by exploits, a mail server compromise, or cracked password.
The thin layer between open policy and needful secrecy
Transparency and openness are inherent and leading principles of the policy propagated by Tibetan officials. Nonetheless, when consequences of a leak might be severe, secrecy is needed. An example for such need is:
While organizing Tibetan-language schools in India or the USA is an open matter, such schools in Tibet itself may have to be covert. Their operation may place teachers' and even students' lives at risk. Indeed, everyone associated with the Tibetan movement who sets foot in Tibet or China is at risk of their lives. Another potentially sensitive information asset is a database of Tibetan refugees, including where they lived in Tibet, when they left and where they live now. (Nagaraja & Anderson, 2009, p.4)
It has been found evidence of a removed email contact list of the dignitaries who Dalai Lama met and a document concerning his negotiating position with the Chinese government. A spokesman for the Tibetan government-in-Exile in Dharamsala, Thupten Samphal, asserted in official communique that even though the Tibetan government is transparent and has nothing to hide, the people working there are concerned about the culprit behind the cyber-exploitation and how the disclosed information might be used by unfriendly agents (Radio Free Asia, 2009).
GhostNet Technical Investigation Results
By employing specific "triangulated analysis" of—1) the information collected from the social engineering 2) the network traffic captured from Tibetan targets 3) the information gained accessing the command and control infrastructure—IWM researchers managed to map out the methods, structure, and capabilities of the GhostNet (Information Warfare, 2009).
Network monitoring software was installed to collect technical data from infected computers. From the very beginning, the data obtained revealed that malware resides in these computers and that some information is being transferred to several control servers.
GhostNet honey-pot
The "honey-pot" computer was set out to perform two major tasks:
- To detect additional malicious servers by examining the inbound/outbound traffic.
- To download all the available malicious code for follow-up research.
At some point after that, an unknown intruder was spotted assuming control, first inquiring about the basic characteristics of the infected machine. Then, the mysterious entity at the other end rummaged through a couple of folders such as "My Documents" and searched to establish as well the geographical location of the "honey-pot" computer (Akkad, 2009).
Greg Walton from the University of Toronto's Munk Centre for International Studies testifies to the truth of such an incident: "Whilst I was in the private office of His Holiness the Dalai Lama, we saw a hacker, seemingly based in China, retrieving sensitive documents." (BBC News, 2009, par.32)
The staff behind the GhostNet investigation succeeded in connecting the "honey-pot" machine to the attacker's gh0st RAT client by initially executing a command on the attacker's web-based administration interface to download a gh0st RAT, a famous type of Trojan used in GhostNet. Eventually, several IP addresses within a DSL range in Hainan Island, China, were identified. The exploiters utilized them to maintain communication connections with the compromised computers (Information Warfare, 2009).
GhostNet Command & Control Infrastructure
The data collection at Tibetan missions and especially in Dharamsala, combined with the supervening analysis, provide a proof of the existence of four control servers and six command servers. Apparently, the computer that was compromised first called home to the control server on May 22, 2007 (Information Warfare, 2009).
The simple IP look provided some valuable information about the control servers such as geo-location. Speaking metaphorically, "if the 1,295 infected computers in 103 countries were the limbs, the four servers were the spine, and three of those servers were located in China (Akkad, 2009, p.20)."
The Control servers provided the attacker with graphical user interface facilities with which he could spy and control the infected computer systems. On the other hand, command servers functioned mainly as repositories of malware (Kak, 2012).
The existing Send Command link empowers the exploiter to send specific instructions to each particular infected machine. Such instructions may vary, obtaining system information, download of malicious files appearing as a plain image file that might provide additional functionalities like keystroke logging or making the malware remain in a dormant state.
Gh0st RAT
One of the commands at hand to the intruders is to instruct the "possessed computers" to download Gh0stRAT.' RAT' stands for "Remote Administration Tool." The exploiter is able to direct the actions of such a Trojan via a "RAT Management Tool," which appear as the fore-mentioned graphical user interface (Kak, 2012).
The Gh0stRAT infection, in turn, would give them a complete, real-time control and the possibilities of performing the following tasks (and even more):
- Spy on the currently running processes
- Spy on the installed applications
- Spy on the current network connections
- Turn on/off webcam or microphone and capture screens and audio
- Send corrupt emails to those whose email addresses are discovered on the infected machine
- Capture keyboard events
- Download additional malware or Gh0stRAT updates
- Establish connection to the Gh0stRAT owner
Evidence leading to the culprit
What did the digital traces say? Not much really, but it is not surprising given the attribution problem surrounding these events.
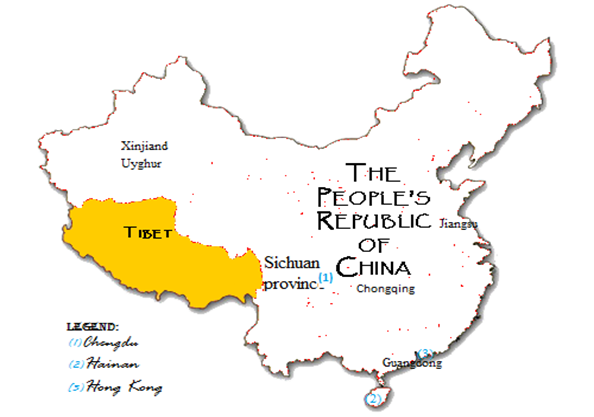
In the beginning, when the Cambridge University researchers checked up on OHHDL's web hosting and email services provider, they found out that a number of successful logins belonged to Hong Kong and Chinese ISPs. Presumably, none of the people at OHHDL have associated with anyone from there. Moreover, most of the suspicious IP addresses belonged to ISPs in Xinjiand Uyghur Autonomous Region, China – the place where is thought that the local authorities (police & intelligence) are entrusted with the oversight of the Tibetan independence campaigners (Nagaraja & Anderson, 2009).
In following observations by the same research group, they come across exfiltration of sensitive files from OHHDL via a modified HTTP protocol. The lead goes to three servers in China's Sichuan province, which is "the location of the Chinese intelligence unit specifically tasked with monitoring the OHHDL (Nagaraja & Anderson, 2009, p.7)."
According to IWM, although one of the four control servers is located in the United States, all the others are in China —Hainan, Sichuan and Guangdong. Similarly, one of the control servers is located in Hong Kong and the others are in mainland China—Hainan, Sichuan, Guangdong, and Jiangsu.
Whereas the GhostNet command and control center appears to be situated somewhere on Hainan Island (headquarters of Lingshui intelligence bureau and the Third Department of the PLA), some traces lean towards hackers residing in Chengdu, which is by coincidence or not one of the PLA's technical reconnaissance bureaus responsible for gathering intelligence (Hays, 2012).
The independent cyber-security researcher Greg Walton points to Chongqing: "Chongqing is interesting in that it's like a nexus of organized crime, the party, a big computer-hacking scene and all sorts of PLA installations. It is not a secret that the data is ending up with the state (Hays, 2012, par.2)."
He admits that at this point, there is no direct evidence linking GhostNet to the central government, however, he ascertains that, "Some people shy away from saying it's the state, but there's a growing body of evidence. My own feeling is that sooner or later someone will be able to prove it (Hays, 2012, par.14)."
Reference List
Akkad, O. el, (2009). Meet the Canadians who busted GhostNet. Retrieved on 13/04/2013 from http://www.theglobeandmail.com/technology/meet-the-canadians-who-busted-GhostNet/article1214210/?page=all
BBC News, (2009). Major cyber spy network uncovered. Retrieved on 13/04/2013 from http://news.bbc.co.uk/2/hi/americas/7970471.stm
Information Warfare Monitor, (2009). Tracking GhostNet: Investigating a Cyber Espionage Network. Retrieved on 08/03/2013 from http://www.nartv.org/mirror/GhostNet.pdf
Hays, J., (2008). Who is behind China's Internet attacks. Retrieved on 13/04/2013 from http://factsanddetails.com/china.php?itemid=2245&catid=7&subcatid=44
Kak, A., (2013). Lecture 30: Mounting Targeted Attacks with Trojans and Social Engineering — Cyber Espionage. Retrieved on 13/04/2013 from https://engineering.purdue.edu/kak/compsec/NewLectures/Lecture30.pdf
Markoff, J., (2009). Vast Spy System Loots Computers in 103 Countries. Retrieved on 13/04/2013 from http://www.nytimes.com/2009/03/29/technology/29spy.html?_r=3&
Michael A., (2010). Special Series Cyber Probing: The Politicisation of Virtual Attack. Retrieved on 13/04/2013 from http://www.conflictstudies.org.uk/files/Cyber_Probing.pdf
Hands-on threat intel training
Nagaraja S. & Anderson R., (2009). The snooping dragon: social-malware surveillance of the Tibetan movement. Retrieved on 13/04/2013 from http://www.cl.cam.ac.uk/techreports/UCAM-CL-TR-746.html
Singel. R. (2008). Espionage Against Pro-Tibet Groups, Others, Spurred Microsoft Patches. Retrieved on 13/04/2013 from http://www.wired.com/politics/security/news/2008/04/chinese_hackers?currentPage=all
Radio Free Asia, (2009). Cyber-Spy Probe Sought. Retrieved on 13/04/2013 from http://www.rfa.org/english/news/china/GhostNet-04072009103413.html