Malvertising: A Growing Threat at the Start of 2014
Word Meaning
The term "malvertising" is coined through the combination of two words – "malware" (i.e., "malicious software") and "advertising."
Hands-on threat intel training
Diagram 1

As an activity taking place online, malvertising is defined as the use of online ads to distribute malicious software. Although malvertising campaigns may not be as frequent as those that involve other types of malware, their after-effects can be equally disruptive and annoying for every link in the chain ad ops-publishers-users. With relation to this point, what makes malvertising a bit different from any other hideous computer threat is the fact that it targets not only users, but it may also attack the other components within the medium of its existence. For that reason, among other things, this paper will regard the malvertising issue from many different perspectives in order to cover to a certain extent this broad topic in a way that properly exposes the gravity of the problem.
1. Ways to Set Up Malvertising
1. Social Engineer Yourself a Good Reputation
Under this approach, a fictitious identity is created, along with "window-dressing" making it appear to be a legitimate advertising agency or a representative of such. A lightning-fast upfront payment, urgent deadlines, and pushy behavior are some of the hocus-pocus tricks in the arsenal of cyber-crooks. Sometimes attackers claim to partner with well-known and legitimate online ad tycoons. In a 2009 case, Gawker Media was duped into featuring infectious Suzuki ads. Cyber-criminals might even have the brazenness to pretend to represent these legitimate agencies on the grounds of a falsified letter of mandate (as the one here).
According to a report prepared by OTA, 60% of malvertising scams are related to fake advertising schemes.
Furthermore, many unsecured ends come are created by third parties such as advertising networks. Their ads are not completely vetted due to the brisk dynamic of real-time bidding and automated sale-trade, and malware occasionally can slip through.
Cyber-criminals offer the targeted publishers ad creatives that have a "clean" initial appearance and therefore can gain trust and a good reputation for an idle period. The ads appear normal on the outside, but they are "embedded with malicious code or JavaScript, often obfuscated to hide the actual code being executed or server calls being made." At a given point later, these "clean" ads are converted into sprinklers that spread viruses or spyware behind the facade (See Diagram 2). Essentially, attackers push through their malvertisements to legitimate users by using the good reputation of the websites under attack.
Diagram 2
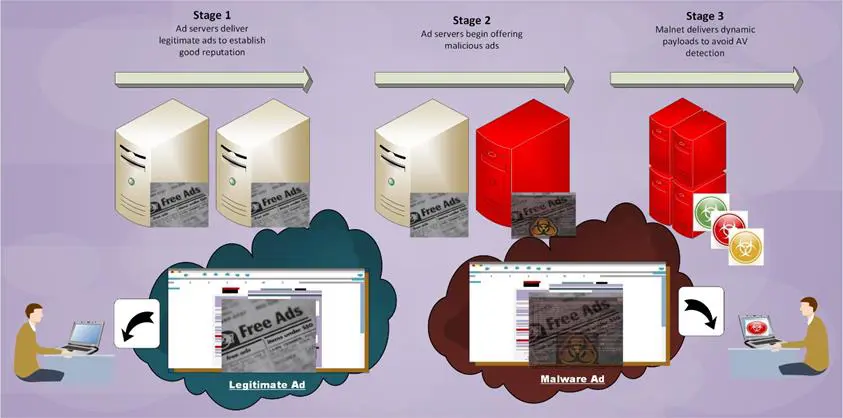
In a situation like this, the complex architecture of the ad network business and, most of all, its impossibility for the positive attribution of detrimental acts to their perpetrators, will shield the attackers' identity from exposure.
2. Hack Your Way In
The other common malvertising attack is made by transforming legitimate ads into malicious ones by hacking trusted websites and planting viruses into banner ads. This offensive move is usually short-lived, and soon after the harm is done the storm abruptly subsides.
2. How Does Malvertising Work?
Malvertisements may be framed as Flash program look-alikes. As a result, the malicious code can execute itself immediately after the advertisement appears, without even needing the user to click on the ad. In addition, Flash-based ads can incorporate logic that decides when and whom to attack.
Seemingly, Flash/ActionScript-based malvertisement has its advantages over those malvertisements using HTML/JavaScript. First, a Flash/ActionScript malvertisement brings in a flavor of flexibility and additional control over the attack logic (as already mentioned). Second, it is less susceptible to examination; in other words, security staff will having a harder time to detect something wrong in the Action Script.
To keep the difficult detection subject still on track, cyber-criminals surely do their best to blend in their malvertisements with the real ones, thus making arduous the process of sorting out which is which organized by the advertisement networks. One way of doing this is by obfuscating the logic embedded as part of the ad's code (both Flash/ActionScript and HTML). The ActionScript implemented in malicious Flash ads can be specifically obfuscated with the commercial and non-malicious tool SWF Encrypt, converting the code practically into unreadable mash.
On the other hand, malicious ads without Flash could simply redirect users to a site hosting an exploit kit. Once arrived at this snug destination, users quickly turn into victims because their machines are subjected to numerous attacks on the browser or the software that a browser can employ, for instance, Java Runtime or Acrobat Reader. To put it another way, victim's browser environment is probed by the exploit kit's code in order to determine how resistant it is to exploitation attempts.
Users Don't Have to Click the Ads to Get Infected!
A common misconception when it comes to malvertising is that users must click on the ad to get infected. Although this presupposition is not entirely wrong, in many cases it is just enough for the user's browser to start loading a certain malicious website and the infection will set in automatically and surreptitiously. The head of the Blue Coat research lab, Chris Larsen, confirmed and documented one modus operandi—a website booby trap that can use JavaScript to call to appear concealed iframes that instantly load PDF code to exploit particular Adobe Reader vulnerabilities.
Another variety of this line of malvertising infections is an ad that launches fake anti-virus software that scans and indicates that the victim's computer is infected. Victims are always "advised" to purchase an infection-removing tool; a false puffery, of course, that, in effect, is another piece of software that is either entirely good for nothing or is another conduit through which criminals smuggle other viruses and infections. A good instance is the malicious banner ad on the New York Times in 2009 that attempted to coax visitors into installing fake AV and then further tried to persuade them to buy an all-cure solution to right the wrongs it claimed to have found.
3. Why Do the Bad Ads Even exist?
Ad Quality Prevails over Security
A very important part of the inspection of newly arrived ads is a process called creative quality assurance, which is executed by ad operators. As the name suggests, it is more like a quality-oriented assurance than any other type of assurance. Greater ad quality matching positively with the brand is priority because advertising is vital for website business and it means greater profit.
Furthermore, in reality, ad operators, even though standing as the last line of defense, are not empowered to make their own decisions and to freely do everything in their power to root out malvertisement. Many companies recognize the problem: "Creative QA is important, but not as high as it should be. We try to catch as much as we can, but there's always a few that slip through."
In the end, much of the unchecked or partially checked content is given a green light just to satisfy sales and management. It all comes down to the need for revenue, and security concerns yield to this argument. Indeed, publishers should change their outlook and realize that revenue is at risk when the security is neglected.
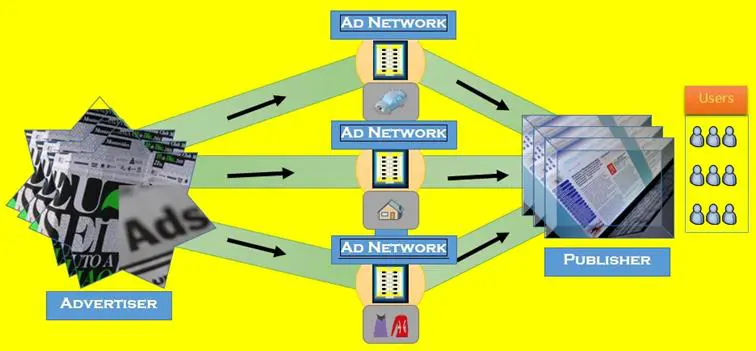
Vulnerabilities in Ad Network Ecosystem
Often ad vulnerabilities are leveraged because of errors made by virtue of practices in ad networking that pursue efficiency over security. It seems that the problem is rooted in the very nature of the ad business, where everything circulates at a great pace, almost unreal, with a myriad of affiliates that come and go every moment.
The heart of the problem is the unsecure chain of intermediaries created by the majority of advertisers who outsource to third parties, who may in turn contract out further. As little as one weak link is sometimes enough to shake the entire structure to its foundations.
Diagram 3
Ad Network Ecosystem
With respect to this point, Jiri Sejtko from Avast! reported that ad networks, especially the large-scale ones, are primarily responsible for the delivery of malvertising content. According to a malvertising campaign discovered and tracked by Avast!, online services that are most frequently attacked on the Internet are Fimserve.com (FOX Audience) and YieldManager.com (Yahoo). Nevertheless, malvertisements should not be associated with particular ad networks or even a route since they can also be delivered via rad.msn.com (Microsoft) and DoubleClick (Google), as well as through webmail services, such as Yahoo Mail and Windows Live (Hotmail).
Elad Sharf from Websense noted that malvertising campaigns are convenient mechanisms that are attractive to cyber-criminals because of the way they "can be easily spread across a large number of legitimate websites without directly compromising those websites."
4. Dealing With Malicious Ads and Consequences
A prima facie thorough check-up of ad candidates through the authenticity of their credentials and a financial background search is advisable. In-depth research is required on the integrity of new advertisers through domain registry lookup that detects irregularities—for example, recently-created data, hidden contact details, modified records, etc.
Apropos of the ads themselves, analysis instruments (e.g., web proxies or automated analyses) can be used to examine Flash ads. This can be a wise move, as Sean Power, a security manager at DOSarrest, warned that many banner ad publishers let through too many Java scripts or advertisements having other code inside. The bad news is that the script of Flash ads can be obfuscated so as to dodge detection. Perhaps if there is a script that raises suspicion, it is better if the ad does not run at all.
Finally, before displaying an ad to the public, it should be duly sanitized, digitally signed, and then give a "Go" directive, in Sean Power's view. He also stated that the responsibility for this processing should rest upon the ad company with respect to every single ad it intends to send out to publishers. What happens actually is a massive wave of negative criticism directed almost one-sidedly at the website displaying the ad, not the ad provider. Perhaps this behavior is understandable in a way because "no one is going to take kindly to a ‛not my responsibility' attitude when they got a virus after visiting your site," as Power remarked.
Reputation-based Governance
Based on the description of malvertising given so far, we know that it is a clandestine act. The bad thing for the publishers, ad networks and every other affiliate taking part, however, is the fact that traffic captures invariably project a powerful searchlight beam on them. And while this publicity is always not good, the bad guys remain in the shadows (perhaps wealthier and feeling victorious and intoxicated with joy).
Despite the carelessness or greed that may eventually embroil them in embarrassing and brand-damaging scandals as a result of exposing their customers to dangerous online threats, website owners and ad networks still do not have enough of an incentive to address and tackle the problem decisively. And even if there is a problem, they still get to keep the payment. Lenny Zeltser from Infosecisland comes right to the point when he enumerates the vicious cycle where those responsible just pass the ball to one another until everybody stops care:
Diagram 4

Well, let's not judge everyone by the same standard, many ad networks do a better job at blocking harmful advertisements.
As of this writing, there have been four noteworthy malvertising incidents from the beginning of the year. Three of them—against the DailyMotion.com , the South African Mail & Guardian, and the Swedish news site Aftonbladet—were fake A/V-based attacks, while the fourth one, against Yahoo, redirected visitors to a corrupt website.
DailyMotion.com is a video-sharing platform ranked in world's top 100 with more than 17 million monthly viewers. On January 7, 2014, the security company Invincea reported that malvertisements attacked visitors of DailyMotion. It works like this: When the user loads the page, an indiscernible iframe redirects them to a Fake AV, which scans and alerts the user's that his PC is critically infected. The initial JavaScript redirect is loaded with the help of engine.adzerk.net and it loads to a third-party domain in Poland (webantivirusprorh[.]pl/ (93.115.82.246), according to Invincea. Users are then presented with a dialog box prompting them to pay $99.99 to "activate" a removal tool that is, in fact, a malicious executable.
Malvertising on Yahoo
The Dutch Fox-IT first broke the news about the malvertisements streaming from Yahoo in the last days of 2013. The longevity, structure, and purpose of the versions of this campaign differ, as you are about to see.
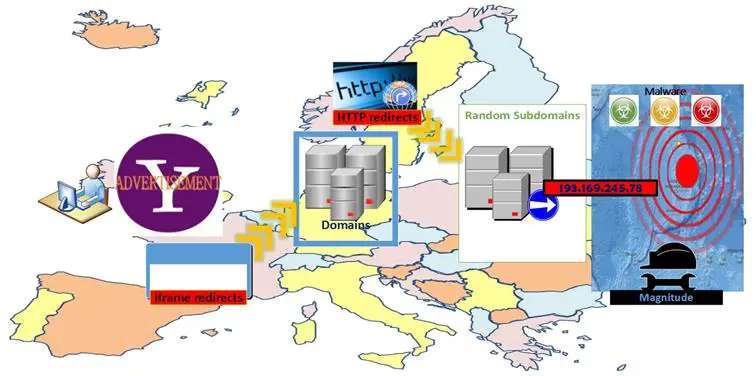
According to Fox-IT, the scheme is simple (see Diagram 5):
1) There are some malicious advertisements, iframes, served by ads.yahoo.com, but hosted on a group of domains;
2) Upon visiting yahoo.com, users are redirected by those malvertisements first to one of the domains.
3) Then the visitors are directly redirected further via HTTP (clicking on ads is not necessary) to subdomains hosting the infamous "Magnitude" exploit kit, which diagnoses systems for software vulnerabilities related to the Java application framework. The hitmanPro team has found "CVE-2012-0507 to be associated with this campaign on infected computers, confirming the fact that many computers have outdated software."
If a backdoor is found, the users may receive a "nice treatment" with one or a combination of the following malware:
- ZeuS
- Andromeda
- Dorkbot/Ngrbot
- Advertisement clicking malware
- Tinba/Zusy
-
Necurs
Diagram 5
Yahoo Malvertising — Fox-IT Version
Fox-IT staff made calculations based on a sample of traffic that the total number of visits to the website is around 300k/hr. Since the normative infection rate is 9%, it would mean approximately 27,000 infections. every hour. Based on the information they provide, the Yahoo malvertising began sometime on December 30, 2013, and ended at an unspecified time on January 03, 2014.
Light Cyber firm from Israel propounds that Yahoo's venomous advertisements were set to unleash a piece of Bitcoin mining malware. With the increasing popularity of virtual money, cyber-attacks of this type will perhaps grow in near future.
On the other hand, Cisco Systems links the Yahoo malvertising to broader underhand machinery for pushing traffic.
As they claim, the Yahoo incident is a turn-out, "just one attack in a long series of other attacks waged by the same group."
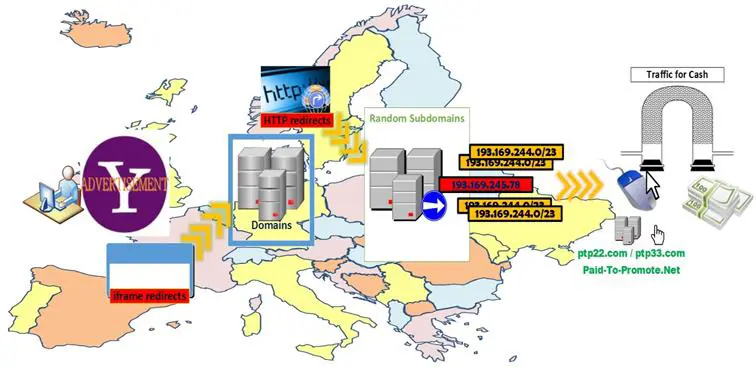
Jason Schultz, a threat research engineer with Cisco, attests that the IP address 193.169.245.78 associated with the Yahoo malvertising appears to be connected with other IP addresses within the 193.169.244.0/23 netblock. It seems likely that they have been utilized by the same entity. Instead of redirecting to a page armed with an exploit kit, Cisco reveals that an HTTP response code 302 actually sends users to domains ptp22.com or ptp33.com, which belong to an organization holding the unequivocal name Paid-To-Promote.Net (see Diagram 6), which pays "people fees to push traffic to other website." Everything seems crystal-clear, traffic monetizing might as well be the new money-laundering machine dressed up in a pseudo-legitimate form.
Moreover, Schultz uncovers that this is a part of an "older domain infrastructure inside 199.204.72.0/24, which appears to have been used by the same group for the same purpose, beginning on November 28, 2013, and continuing well into early January."
Diagram 6
Yahoo Malvertising — Cisco Version
As the vice president at ProofPoint's Armorize Technologies explained to the readers of Security Week: "Spreading malware over the Web is about traffic volume. Large websites have the volume, but it's much harder to hack [them]. However, all larger websites serve advertisements." With so many forms of online treats emerging on a daily basis the last couple of years, computer visitors are already cautious about which sites to visit or where not to click. Major platforms as Yahoo appear legitimate and secure in the users' eyes. Yet the digital ads seem like the ideal device for hiding a malicious payload, which is to be spread to hundreds of thousands of unsuspecting people; the final product is a payload in a trusted package "delivered" to many and waiting to be cash in one way or another.
It must be noted in conclusion that malvertising incidents increased 20 times from 2010 to 2012, with more than half of all publishers having to deal with such at least once. This fact, in combination with the recent cases, indicates that malvertising is a growing attack vector for quite some time and it is here to stay.
Reference List
Anti-Malvertising. com. About Malvertising. Retrieved on 10/02/2014 from http://www.anti-malvertising.com/malvertising
Beeler, R. (2013). The Ad Ops Pat Down: The Creative QA Process. Retrieved on 10/02/2014 from http://www.admonsters.com/blog/ad-ops-pat-down-creative-qa-process
Danchev, D. (2013). Malvertising campaigns at multiple ad networks lead to Black Hole Exploit Kit. Retrieved on 10/02/2014 from http://www.zdnet.com/malvertising-campaigns-at-multiple-ad-networks-lead-to-black-hole-exploit-kit-7000010707/
Finley, K. (2010). What You Need to Know About Malvertising. Retrieved on 10/02/2014 from http://readwrite.com/2010/09/09/what-you-need-to-know-about-ma#awesm=~ovuEnAPiFOoJ0Y
Fox-IT (2014). Malicious advertisements served via Yahoo. Retrieved on 10/02/2014 from http://blog.fox-it.com/2014/01/03/malicious-advertisements-served-via-yahoo/
HitmanPro (2014). Malware served via Yahoo affected millions. Retrieved on 10/02/2014 from http://hitmanpro.wordpress.com/2014/01/05/malware-served-via-yahoo-affected-millions/
http://www.infosecurity-magazine.com, (2014). Yahoo's Malvertising Issue is Bigger Than Originally Thought. Retrieved on 10/02/2014 from
http://www.infosecurity-magazine.com/view/36394/yahoos-malvertising-issue-is-bigger-than-originally-thought/
http://www.spamfighter.com. News Portal South African Mail & Guardian Victimized with Malvertising Assault. Retrieved on 10/02/2014 from http://www.spamfighter.com/News-18773-News-Portal-South-African-Mail-Guardian-Victimized-with-Malvertising-Assault.htm
Invincea (2014). DailyMotion.com redirects to Fake AV Threat. Retrieved on 10/02/2014 from http://www.invincea.com/2014/01/dailymotion-com-redirects-to-fake-av-threat/
Jacoby, D. (2014). Largest Website in Sweden Spreading Malicious Code. Retrieved on 10/02/2014 from http://www.securelist.com/en/blog/208216070/Largest_Website_in_Sweden_Spreading_Malicious_Code
Mimoso, M. (2014). Malicious Ads on DailyMotion Redirect to Fake AV Attack. Retrieved on 10/02/2014 from http://threatpost.com/malicious-ads-on-dailymotion-redirect-to-fake-av-attack/103494
Moraff, C. (2014). Yahoo malvertising breach offers lessons in ad security. Retrieved on 10/02/2014 http://smartblogs.com/social-media/2014/01/10/yahoo-malvertising-breach-offers-lessons-in-ad-security/
Prince, B. (2014). Yahoo Attack Spotlights Challenges of Malvertising. Retrieved on 10/02/2014 from http://www.securityweek.com/yahoo-attack-spotlights-challenges-malvertising
Raywood, D. (2014). Responsibility for malvertising lies with the advertising platform. Retrieved on 10/02/2014 from http://www.itsecurityguru.org/responsibility-malvertising-lies-advert-platform-website/#.Uvkgv_tBEXZ
Schultz, J. (2014). Malicious Ads from Yahoo Just the Tip of the Iceberg. Retrieved on 10/02/2014 from
http://blogs.cisco.com/security/malicious-ads-from-yahoo-just-the-tip-of-the-iceberg/
Segura, J. (2013). Malvertising and the joys of online advertising. Retrieved on 10/02/2014 from http://blog.malwarebytes.org/online-security/2013/12/malvertising-and-the-joys-of-online-advertising/
Weaver, J. (2013). How Publishers Guard Against Malvertising. Retrieved on 10/02/2014 from http://www.admonsters.com/blog/how-publishers-guard-against-malvertising
Zeltser, L. (2011). Malvertising: The Use of Malicious Ads to Install Malware. Retrieved on 10/02/2014 from http://www.infosecisland.com/blogview/14371-Malvertising-The-Use-of-Malicious-Ads-to-Install-Malware.html
Diagrams
Diagram 1 is based on a figure provided by Anti-Malvertising. Com in the About Malvertising section. Retrieved on 10/02/2014 from http://www.anti-malvertising.com/malvertising
Diagram 3 is based on an image provided by IAB. Retrieved on 10/02/2014 from http://i1.ytimg.com/vi/1C0n_9DOlwE/maxresdefault.jpg
Hands-on threat intel training
Diagram 4 is based on information provided by L. Zeltser in Malvertising: The Use of Malicious Ads to Install Malware. Retrieved on 10/02/2014 from http://www.infosecisland.com/blogview/14371-Malvertising-The-Use-of-Malicious-Ads-to-Install-Malware.html









