Reinventing Threat Intelligence
Effective threat intelligence is one major service that most companies offer to alert about the latest threats. Threat intelligence alerts about the latest threats, vulnerabilities, malware attributes, malicious IPs, etc., which can cause risk to an organization. This information will help the engineers to plan and prepare themselves to prevent their organization from falling under an attack. Such services are now common in the IT industries and an organization won't hesitate to pay a bunch of money for getting the latest updates via threat intelligence. Some services include Dell Secureworks, RSA cyber-threat intelligence, Norse Corp., Symantec, Deepsight, and many more.
Private sources are only available on a paid basis; they charge based on the information they provide, the number of user accesses, or on a monthly basis. An organization can subscribe to such services to receive regularly updated threat feeds. These feeds have the advantage of providing quality data.
Anyway, monitoring the latest threats populating the market is one of the major tasks that an information security officer needs to carry out daily. He/she must be aware of the current trends in the cyber-world to understand the latest attacks, prevention mechanisms, mitigations, workarounds, etc.
For sure, this is one of the mechanism that can be adopted to prevent against advanced persistent threats (APTs). Let's say an outside organization is brought down by malware that exploited a loophole in the systems; as a security engineer, it will be our duty to check whether our organization is also vulnerable to that exploit.
Current Intelligence Systems
Malicious actors actively use resources and develop new methods of attacking Internet users. With the rapidly changing nature of the threats, threat intelligence must be acted on quickly to receive its full value. There are also some open Intelligence systems available in the market that some organizations rely on, but the information like the malware IPs, and botnet IPs that they provide can't be relied on. Following are some free sources from where one can get malicious IPs.
On a daily basis they have an update of 10-15 IPs that can be malicious, but when checked with websites like virustotal.com to see the reputation of the website, some are shown as not being malicious. This is a big concern for the companies that rely much on free threat feeds. Public sources are available to anyone and generally there is no cost associated with access.
The other way of getting intelligence feeds is to set up a honeypot; there are numerous projects like honey project that organizations can collaboratively work on. Debian and Nepentheses are some easy honeypots that an information security professional can use to collect malicious IPs. Being a part of honey project, one can get information to share with the team for analysis.
Output of Threat Intelligence
The output of these systems needs to be fed in to an SIEM system. This is where we bring more value to the logs that we get via SIEM solution. If we look at any SIEM vendor, they combine their SIEM service with threat intelligence at a cost or free. Most companies are willing to connect attacks and specific actors that is occurring outside with what is in our internal network by using threat intelligence.
Future Intelligence systems
The next advanced method is the IOC which was developed by Mandiant. Indicators of compromise (IOC) are referred as artifacts of an intrusion that resides in OS and network devices. They can also be called logically grouped sets used for referring specific threats. IOC can be used to categorize various threats that can be used in ways in cyber-security. Indicators of compromise are among the most easily actionable types of threat intelligence and some of the most commonly used IOCs are IP addresses, domain names, uniform resource locators (URLs), and file hashes. IOC definitions are stored in XML schemas.
IOCs tie to observables and observables tie to measurable events or stateful properties that can represent anything from the creation of a registry key on a host to the presence of a mutex. It is a piece of information that can be used to search for or identify potentially compromised systems. Upon detecting a security incident and knowing the type, pattern, changes done, etc., they can be used to formulate attributes. The attributes that can be used in IOC are mutex, registry value, IP address, hash, URL, DNS, etc.
Earlier IOC was used by Mandiant only but other sources are also now using it. The website http://ioc.forensicartifacts.com/ gives a xml schema of all submitted files. McAfee has also developed products to accept the IOC files; Operation Troy IOC has been released by McAfee in IOC format.
Advantages of IOC
- Helps gain faster access to actionable security information.
- Helps organizations share threat intelligence with each other, thereby building trust relationships.
- Can be created very easily.
- Supports an intelligence-driven security model.
Types of IOC
Open IOC
Open IOC stands for "open indicators of compromise" and was created by Mandiant. It is an extensible XML schema for the description of technical characteristics that identify a known threat, an attacker's methodology, or other evidence of compromise.
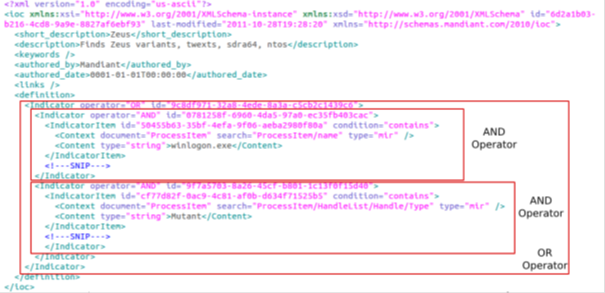
Fig: Open IOC Sample
OpenIOC is written in XML (Extensible Markup Language), which provides a well-recognized standard format of encoding data into a machine-readable format that is used in many different standardized methods of communication. The use of XML offers several benefits for consumers of OpenIOC. It can also be extended with indicator sets that are written in XML and supplied with the base schema. Also, custom indicators that suit a particular environment or threats that are not already described can be created and added if an organization needs them. OpenIOC can be converted or parsed to other formats that might contain information that could feed into or benefit from the threat information contained in an IOC.
OpenIOC is focused on describing technical characteristics of a threat through an extensible XML schema. It has a comprehensive vocabulary for describing low-level attributes that can be easily translated into machine-understandable formats. These can then be used as input to configure various IT security monitoring and detection tools, such as anti-virus, IDS (intrusion detection system), IPS (intrusion prevention system), firewalls, and OS (operating system) security controls and policies. Thus, the intelligence gathered from an incident may be used to protect and prevent compromise of the entire environment.
Cybox (Cyber-Observable Expression)
Cybox is an open language (XML) describing events (cyber-observables) in the security domain. Cyber-observables are called attributes that a threat exhibits, such as deletion of a file, hash value, IP address, etc. According to the Mitre definition of Cybox:
Cybox is a standardized schema for the specification, capture, characterization, and communication of events or stateful properties that are observable in the operational domain. A wide variety of high-level cyber-security use cases rely on such information, including event management/logging, malware characterization, intrusion detection, incident response/management, attack pattern characterization, etc. Cybox provides a common mechanism (structure and content) for addressing cyber-observables across and among this full range of use cases improving consistency, efficiency, interoperability, and overall situational awareness.
IODEF(Incident Object Description Exchange Format)
The incident object description exchange format (IODEF) defines a data representation that provides a framework for sharing information commonly exchanged by computer security incident response teams (CSIRTs) about computer security incidents. More information on IODEF can be seen at http://www.ietf.org/rfc/rfc5070.txt.
STIX (Structured Threat Information Expression)
Structured threat information expression (STIX) format is primarily for sharing of threat intelligence pertaining to incidents. STIX can be used to share techniques, tactics, courses of action, procedures, and basic indicators. The most frequently used types of indicators include IP addresses of known and suspected command-and-control (C2) servers, registry values, email addresses, and malware hashes. STIX also represents the relationships between these objects, forming a graph of relationships that potentially link different campaigns through particular actors and malware hashes. Incidents and indicators are made up, in part, of "observables," as defined by the CYBOX format.
So STIX and Cybox have been developed my MITRE, which invested a sufficient amount of time in developing tools for sharing threat information. MITRE has developed a threat collaboration platform called Collaborative Research Into Threats (CRITs), which makes heavy use of STIX and the related formats. Much publicly available information won't be available about CRITs at the moment, but it represents one of the leading-edge efforts for threat sharing and is used by select threat-sharing partners in a walled garden community.
Let's take an example of how we can represent a phishing attack in STIX format. Phishing is one of the malicious cyber-attacks in which the attacker entices users to click a link that opens a malicious attachment or takes the user to a fraudulent website. When such a phishing mail is received by an incident investigator, he does the normal analysis to find the root cause by checking the domain name reputation, computing the hash file of the attachment, analyzing the structure to look for any kind of phishing, such as a message ID, receiver ID, etc., copying the URL in the email and Googling them. Sending this phishing information to an external party can be in the STIX format. There are tools available to convert phishing email or other threats in to STIX format, which basically saves the analyst a significant amount of time by automating the analysis that is performed on each threats.
This STIX Indicator and any related STIX content can then be easily shared in an automated fashion with threat information-sharing partners as desired, utilizing a trusted automated exchange of indicator information (TAXII) agent in support of a variety of sharing models.
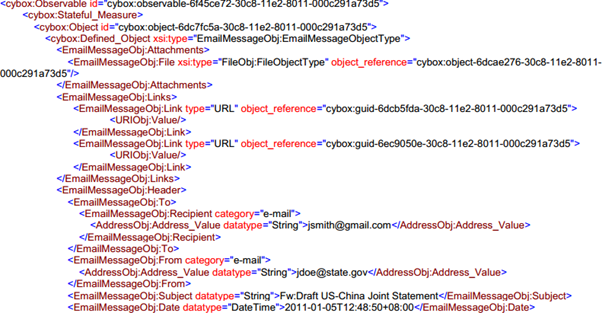
Fig: STIX Architecture
Fill out the Form Below to Download the Accompanying STIX Phishing Example File.
MAEC (Malware Attribute Enumeration and Characterization)
MAEC is a standardized language for encoding and communicating high-fidelity information about malware based upon attributes such as behaviors, artifacts, and attack patterns. MAEC's main function is to serve as a standard method of characterizing malware. This will allow for the description and identification of malware based on distinct patterns of attributes rather than a single metadata entity (which is the method commonly employed in signature-based detection)
By eliminating the ambiguity and inaccuracy that currently exists in malware descriptions and by reducing reliance on signatures, MAEC aims to improve human-to-human, human-to-tool, tool-to-tool, and tool-to-human communication about malware; reduce potential duplication of malware analysis efforts by researchers; and allow for the faster development of countermeasures by enabling the ability to leverage responses to previously observed malware instances. At present Cuckoo sandbox and Fireye are used for after analysis.
TAXII (Trusted Automated Exchange of Indicator Information)
TAXII defines a set of services and message exchanges that enable sharing of actionable cyber-threat information across organizations and product or service boundaries. TAXII, through its member specifications, defines concepts, protocols, and message exchanges to exchange cyber-threat information for the detection, prevention, and mitigation of cyber-threats. TAXII is not a specific information-sharing initiative or application and does not attempt to define trust agreements, governance, or other non-technical aspects of cyber-threat information sharing. Instead, TAXII empowers organizations to achieve improved situational awareness about emerging threats, enabling organizations to share the information they choose with the partners they choose. This trusted information can be categorized into different levels and can be shared with various organizations across the globe.
Conclusion
IOC enhances the operational capabilities of incident management. A common format is necessary for incident handlers to share threat information for incident handling and subsequent analysis. Several communities have come up with models that will improve the ability to resolve security incidents.
References
http://www.rsaconference.com/writable/presentations/file_upload/dsp-w25a.pdf
http://openioc.org/resources/An_Introduction_to_OpenIOC.pdf
http://maec.mitre.org/index.html
http://stix.mitre.org/about/documents/STIX_Use_Case_Examples_v1.0.pdf
Hands-on threat intel training
http://maec.mitre.org/about/docs/Introduction_to_MAEC_white_paper.pdf










