Verizon DBIR 2019 analysis
Introduction
The Verizon Data Breach Investigations Report (DBIR) is now an annual festival of cybersecurity analysis. The 2019 report used data from 41,686 security incidents across 2,013 data confirmed breaches. from both public and private entities, across 86 countries.
These data allow Verizon into the mind of the cybercriminal to see what has been going on the past 12 months. From this, they can also make informed and quantitative analyses of what may happen next in the world of cybersecurity.
DBIR 2019 main findings
One of the key findings of the report is this, taken from the DBIR report brief:
“The most important defense is knowledge.”
Bearing this in mind, let’s look at some of the main findings that came out of the 2019 DBIR report.
The report focuses on nine classification areas, as shown below. This year, however, the report also includes a subsection of financially motivated social engineering (FMSE) attacks. These attacks focus on credential theft and money transfer to accounts controlled by cybercriminals.
The nine classes of attack
- Crimeware
- Cyber-espionage
- Denial of Service
- Insider and privilege misuse
- Miscellaneous errors
- Payment card skimmers
- Point of sale intrusions
- Physical theft and loss
- Web application attacks
Each has their own subsections. There is also a tenth category, “everything else,” into which anything that doesn't fit into the nine above is placed. Verizon has been using these nine categories since 2014, and in the 2019 report, they still fit 98.5% of security incidents and 88% of data breaches.
Some interesting findings from the 2019 DBIR include:
The good news
- Hardly any cryptomining bots were reported (around 2% of malware). This is probably because of the fall in cryptocurrency value
- W2 tax form scams were almost non-existent in the DBIR data. Consequently, attacks targeting Human Resource departments were six times lower in 2018 compared to 2017
The bad news
- Cybercriminals are increasingly targeting company executives. C-level executives are twelve times more likely to be a target for a social incident than in previous years
- Business Email Compromise (BEC) victims experience a greater financial loss than data breaches:
- Median cost for a data breach being $7,611
- Median cost for a BEC being $24,439. Though there is a bit of good news (in the U.S. at least): Actions by the IC3 Recovery Asset Team meant that half of all U.S.-based business email compromises had 99% of the money recovered or frozen
- Payment card web application compromises are on a path to exceeding physical terminal compromises in payment card-related breaches
- Ransomware is still a menace, with around 24% of incidents related to malware being of the ransomware variety
- Mobile phishing is now the most successful in terms of click-through rates
The report highlights the fact that cybercrime is often not a simple case of smash and grab. Cybercrimes like BEC have ongoing repercussions. Even if money is recovered, data stolen as part of the attack is often used for secondary attacks, sold via darknet marketplaces.
Threats and actions
The top three threat actions in a breach were:
- Phishing
- Use of stolen credentials
- Backdoor attacks
The top three threat actions in an incident were:
- DOS
- Loss (various items including credentials)
- Command and control (C2)
Analysis and trends for cybersecurity in 2019
Industry breakdown
The breakdown by industry shows some general patterns:
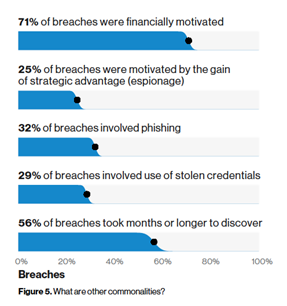
- Money makes the world (and cybercrime) go around, with financial incentives being behind the majority of the breaches. The top reason behind a cyberattack on data is financial gain; in 71% of cases, espionage is behind 25% of breaches
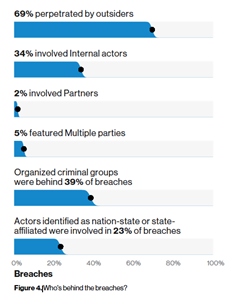
- Insider threat is still an issue but not as prevalent as external threats. The DBIR shows that 69% of attacks are from external actors with 35% being insiders; 5% used multiple parties (collusion)
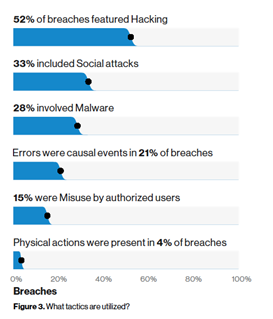
- Errors and web application attacks are common across most industry sectors. Overall, 52% of breaches were from hacking, 33% involved social attacks and 28% malware
The industry sectors analyzed by the DBIR are:
- Retail
- Accommodation
- Financial
- Healthcare
- Information
- Manufacturing
- Professional
- Public
- Education
Retail
81% of breaches were caused by external threats and 19% were insiders. 81% of breaches were due to web applications, privilege misuse and miscellaneous errors. 97% of breaches were financially motivated.
Accommodation and food services
95% of breaches were external. 93% of all breaches in this sector were due to POS intrusion, web applications and crimeware patterns. All incidents were financially motivated.
Financial
72% of breaches were caused by external actors and 36% by insiders. 72% of breaches were caused by web applications, privilege misuse and miscellaneous errors. 88% of these breaches were financially motivated; the rest were cyber-espionage.
Healthcare
59% of breaches in healthcare were carried out by internal parties, with 42% external. 81% of breaches were caused by miscellaneous errors, privilege misuse and web applications. 83% were for financial gain, with a small percentage for fun or a grudge.
Information
56% of breaches were caused by external threats and 44% were insiders. 83% of breaches were due to miscellaneous errors, web applications and cyber-espionage. Financial gain was behind 67% of the breaches.
Manufacturing
75% of breaches were caused by external threats and 30% were insiders. 71% were caused by web applications, privilege misuse and cyber-espionage. 58% of breaches were financially motivated with 27% being for espionage reasons.
Professional
75% of breaches were caused by external threats and 30% were caused by insiders. 81% were caused by web applications, miscellaneous errors and everything else. 88% of breaches were financially motivated.
Public sector
77% of breaches were caused by external threats and 21% were insiders. 72% of breaches were due to cyber-espionage, miscellaneous errors and privilege misuse. 66% of breaches have espionage as the motive, and 29% were financially motivated.
Education
The split of external and internal actors causing the incidents was 57% to 45%, respectively. 80% of breaches were caused by errors, web application attacks and everything else. Breach reasons were mainly financial, but with some just for fun or a grudge.
DBIR suggestions for cyberdefense strategies
A number of suggested strategies were made across the various industry sectors. However, as many of the threats are common across the sectors, there are some general outcomes from the report that should be considered in your security strategy:
- Data theft during capture needs to be addressed. Formjacking, which uses injection to capture data entered in a form, needs to be hardened against
- e-Payment application security needs to be a focus as POS attacks decrease
- Human factors continue to add a layer of complexity to security efforts. This isn’t just about social engineering. Human error in misdelivery and erroneous publishing of data, as well as insider threats, are still prevalent. Misconfiguration of servers and other assets must also be addressed
- Credential theft is seen as a key to opening up further cybercriminal opportunities. Focus on credential safety such as Multi-Factor Authentication (MFA) and good password hygiene practices
- Frequent security awareness training can help reduce the likelihood an employee will be a victim of a cyberscam, including cyberespionage incidents
- DDoS continues to be an issue so needs to be protected against
- Consider monitoring privileged access users
- Use motivation-based awareness training
Conclusion
The DBIR is an important body of work that performs a quantitative analysis based on real-world data. Although it is natural to look at your own sector when reading the full report, it’s also important to take note of other sectors.
Much of the results obtained from the report focus on certain areas that have commonality across industries. Human factors such as social attacks and errors are prevalent. These can be countered with education, care and knowledge.